Question 256
A security analyst is reviewing logs and sees a former employee's account has been used to access critical information on a private cloud resource. The analyst examines firewall and IPS logs but does not find traffic that is relevant to the breach. Which of the following is the MOST likely source of the compromise?
Question 257
A VM was deleted by mistake today at 11:05 a.m. Below are the backups currently available for the VM:
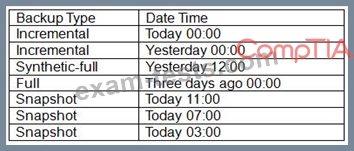
Crash-consistent restore is acceptable. Which of the following backups should be chosen?

Crash-consistent restore is acceptable. Which of the following backups should be chosen?
Question 258
Company A recently acquired Company B.
A cloud administrator needs to give access to the accounting and time-reporting systems for Company B's employees. Company A's employees use a single account to access both systems.
To give access to Company B's employees, the cloud administrator should:
A cloud administrator needs to give access to the accounting and time-reporting systems for Company B's employees. Company A's employees use a single account to access both systems.
To give access to Company B's employees, the cloud administrator should:
Question 259
Instruction:
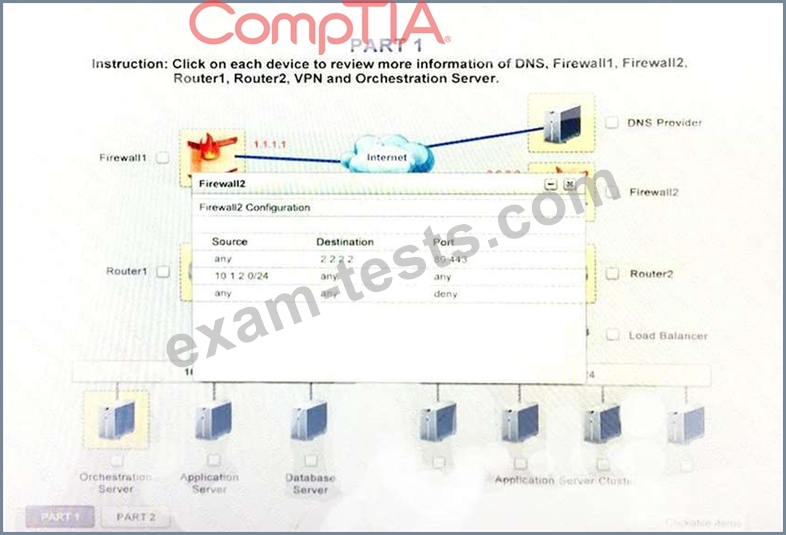
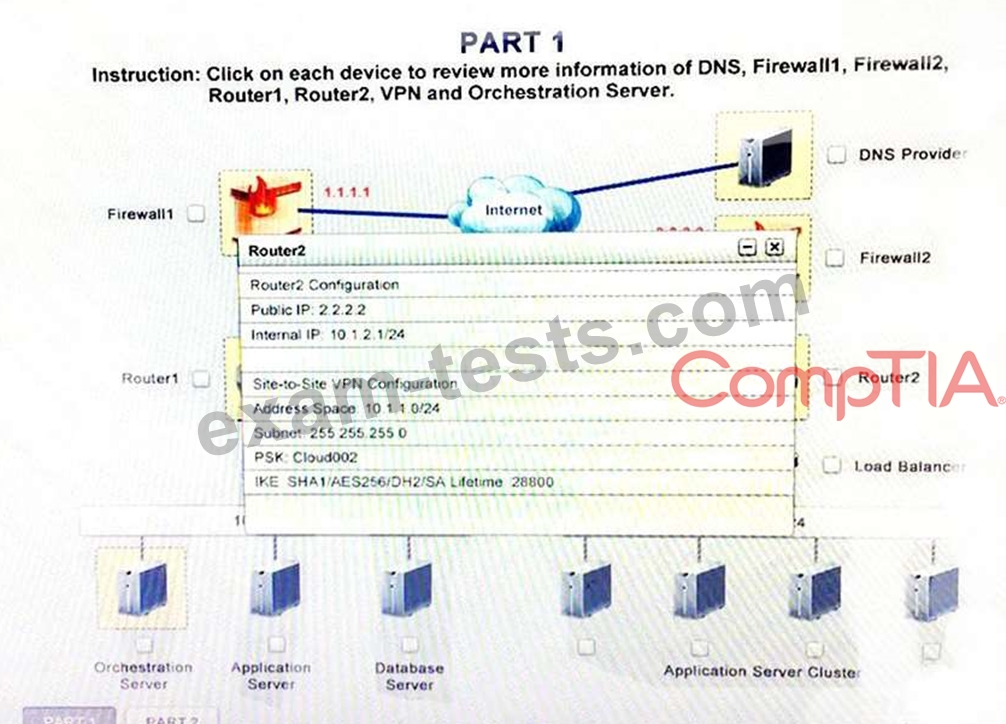
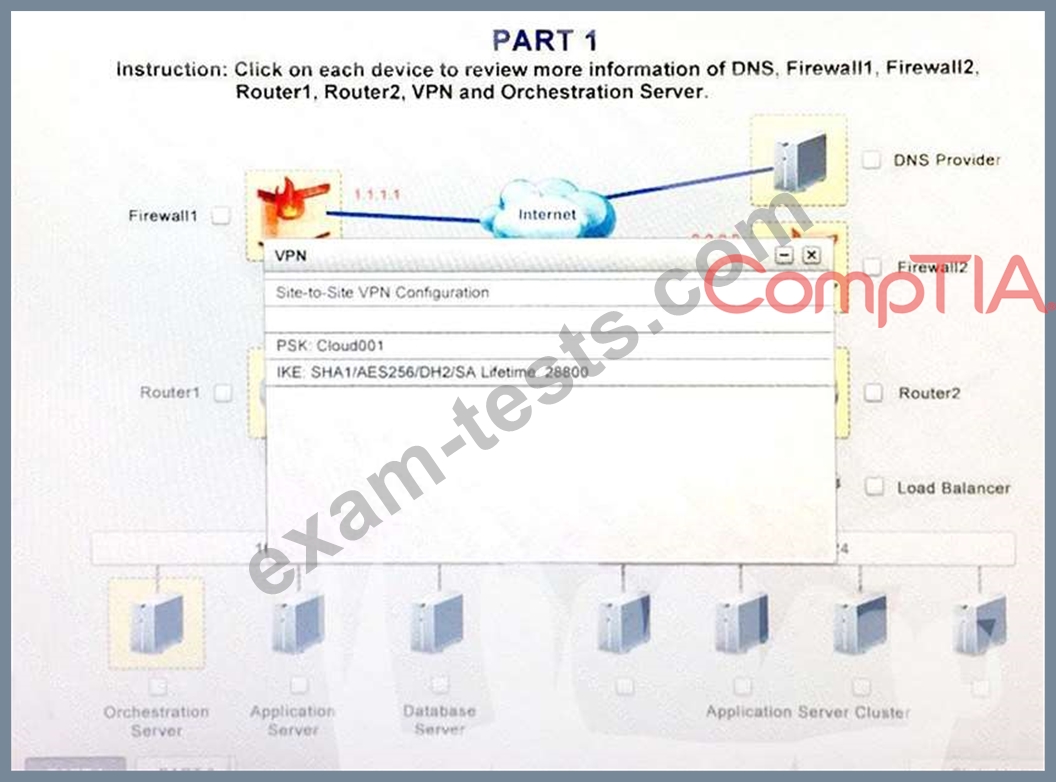
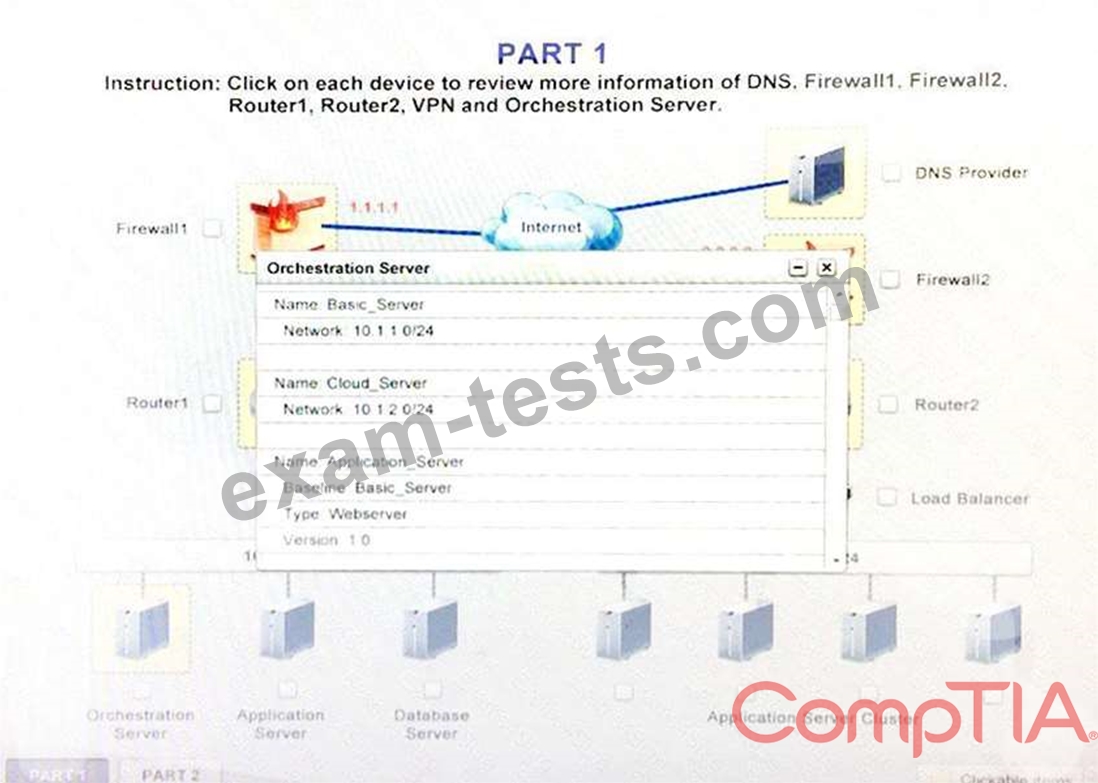
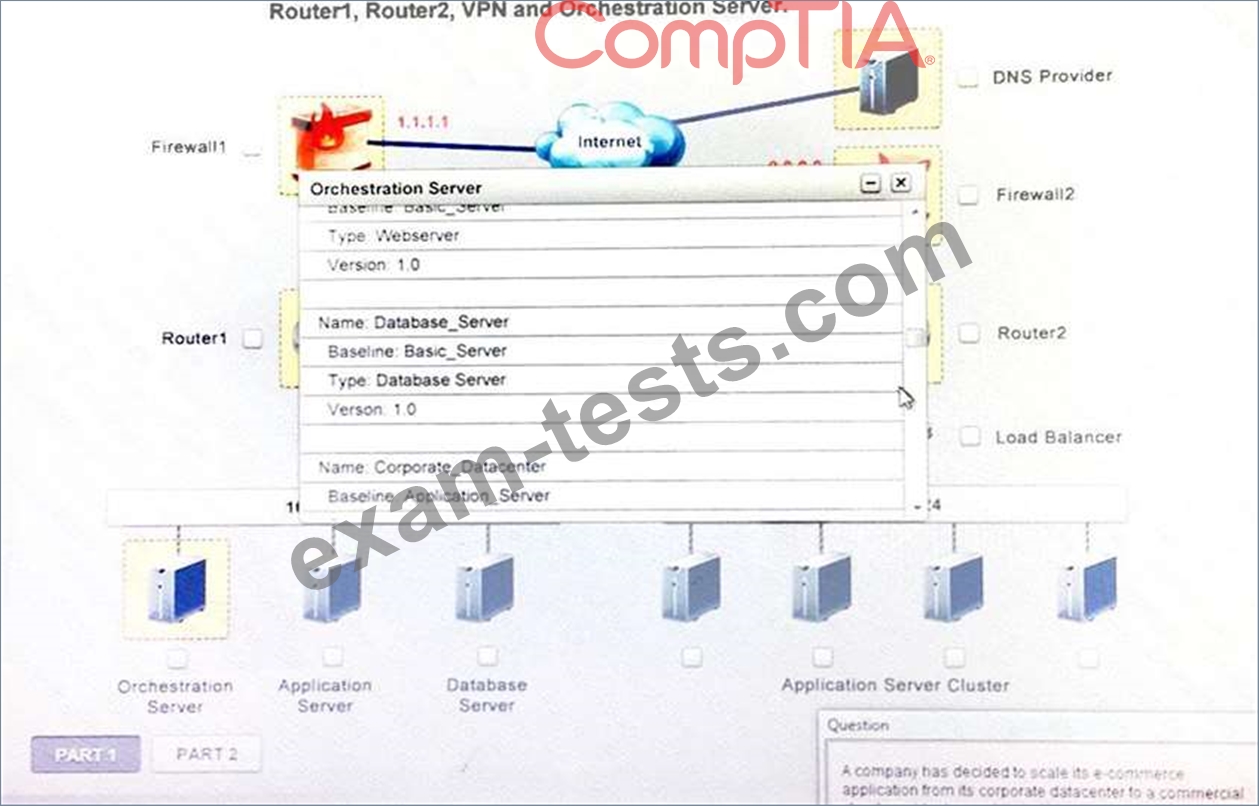
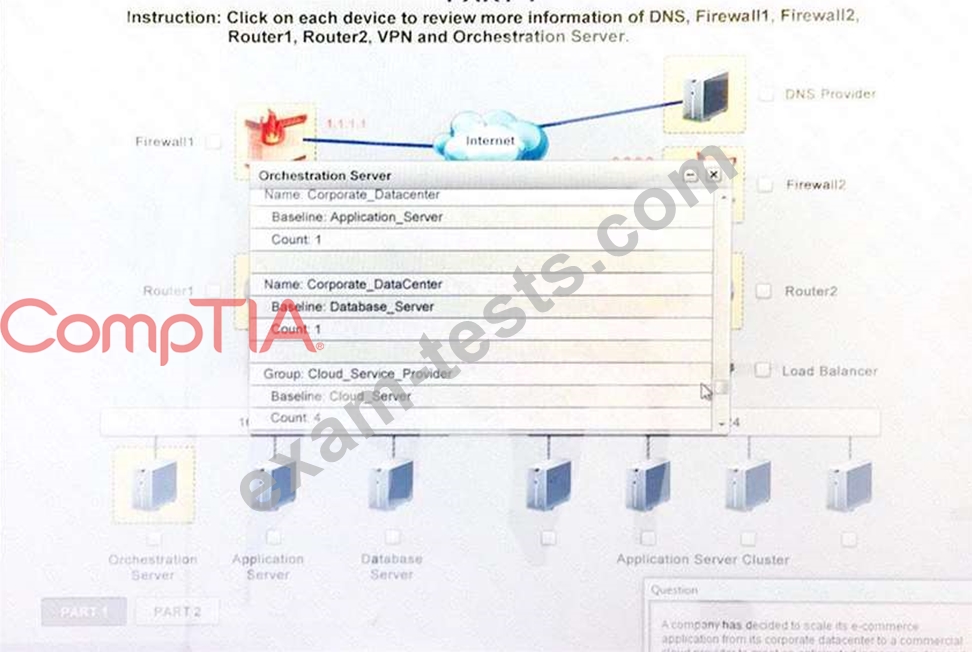
Only select a maximum of TWO options from the multiple choice question.






Only select a maximum of TWO options from the multiple choice question.
Question 260
Joe, a cloud administrator, is no longer able to SSH to his cloud management console after he returns from a two-week vacation. A coworker was able to connect from the management station with no issue. During the last two weeks, the desktop team replaced all administrator machines with newer ones. Which of the following must Joe do FIRST to troubleshoot his access?

