Question 1
Which compliance standard provides policies and procedures to optimize the security of credit card
transactions?
transactions?
Question 2
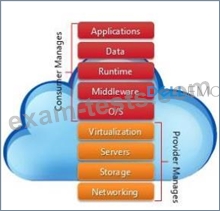
Which cloud service model is represented in the exhibit?
Question 3
What term refers to the entry points from which an attack can be launched?
Question 4
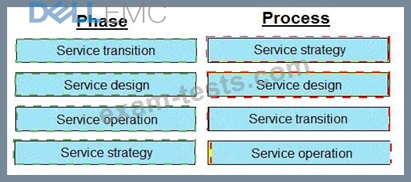
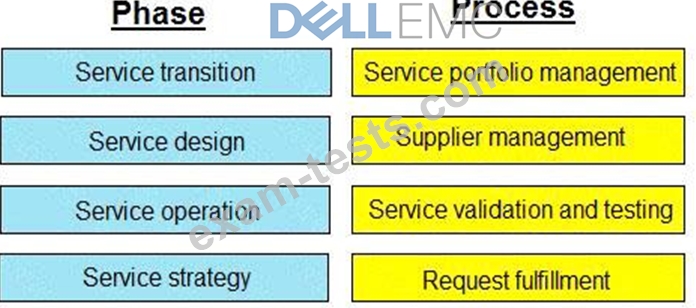
Match each service management phase with its process.

Question 5
What are the key approaches to application transformation?