Question 161
Which process is used to protect file system structures against corruption through 32-bit CRC checksums?
Question 162
A customer has two Isilon clusters in an Active-Passive setup. The customer has latency sensitive media editing workflows. Most of the media editing work occurs prior to broadcasting between 7:00-8:00, 11:00-12:00,
17:00-18:00 and 19:00-20:00.
What should be recommended to minimize the risk of including latency to the client workflow?
17:00-18:00 and 19:00-20:00.
What should be recommended to minimize the risk of including latency to the client workflow?
Question 163
What is an accurate statement when configuring an Isilon Gen 6 cluster with Compliance SmartLock?
Question 164
You meet with the IT Director of a large single site campus. The IT department has recently taken over Physical Security from the facilities department and plans a complete overhaul of the surveillance solution.
They are looking to you as a storage architecture expert to provide the correct amount of storage needed.
The IT Director asks you what items they need to provide in order to size this solution.
What data do you require from the customer?
They are looking to you as a storage architecture expert to provide the correct amount of storage needed.
The IT Director asks you what items they need to provide in order to size this solution.
What data do you require from the customer?
Question 165
Refer to the Exhibit.
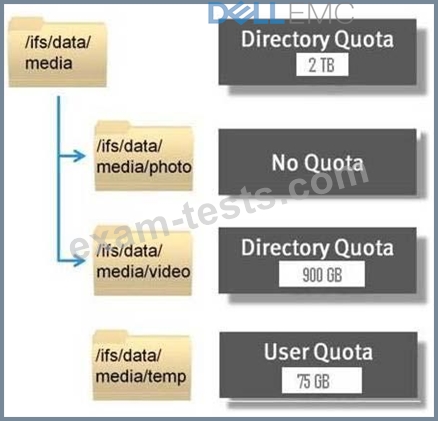
What is represented by the information shown?

What is represented by the information shown?

