Question 56
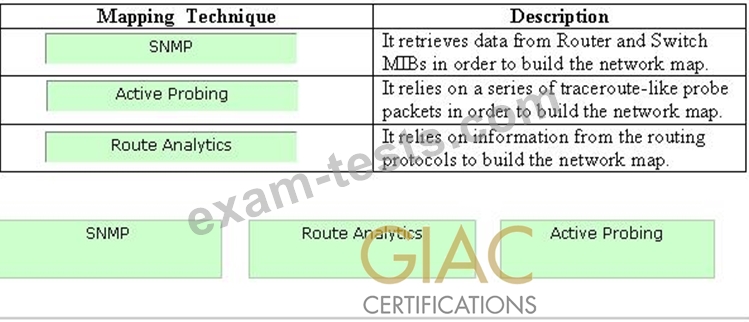
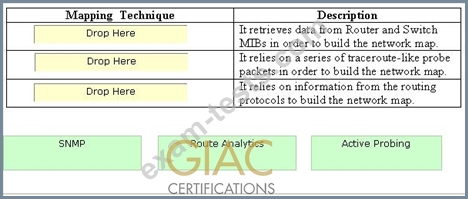
Drag and drop the mapping techniques to their respective descriptions.

Question 57
Which of the following tools can be used for steganography?
Each correct answer represents a complete solution. Choose all that apply.
Each correct answer represents a complete solution. Choose all that apply.
Question 58
Which of the following is a type of computer security vulnerability typically found in Web applications that allow code injection by malicious Web users into the Web pages viewed by other users?
Question 59
Which of the following incident response team members ensures that the policies of the organization are enforced
during the incident response?
during the incident response?
Question 60
Which of the following attacks involves multiple compromised systems to attack a single target?