Question 56
Which of the following descriptions about the properties of BGP is correct?
Question 57
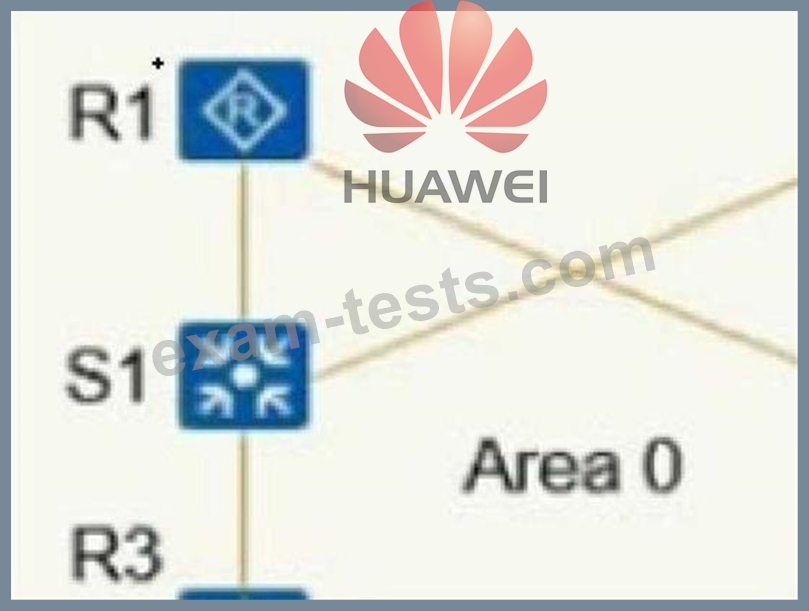
As shown in the figure, a company has built an OSPF network. The links in the figure all form an OSPF adjacency relationship, and all OSPF devices announce their own loopback interface addresses. One day, the two links of S1-R2 and S2-R1 suddenly failed. In order to check whether the network is running normally, the engineer checked the equipment status. Which of the following descriptions is correct?



Question 58
The security protection actions that can be performed by a secure MAC address do not include which of the following?
Question 59
In a shared network, PIM-SM. Which mechanism is used to prevent duplicate traffic?
Question 60
Which of the following attacks areDoS ( Denial of service) attack?

