Question 51
Which protocols below can guarantee the confidentiality of data transmission? (Multiple Choice)
Question 52
Regarding the online user management, which of the following is incorrect?
Question 53
Clients in the Trust zone of the firewall can log in to the FTP server in the Untrust zone, but cannot download files. Which of the following methods can solve the problem? (Multiple Choice)
Question 54
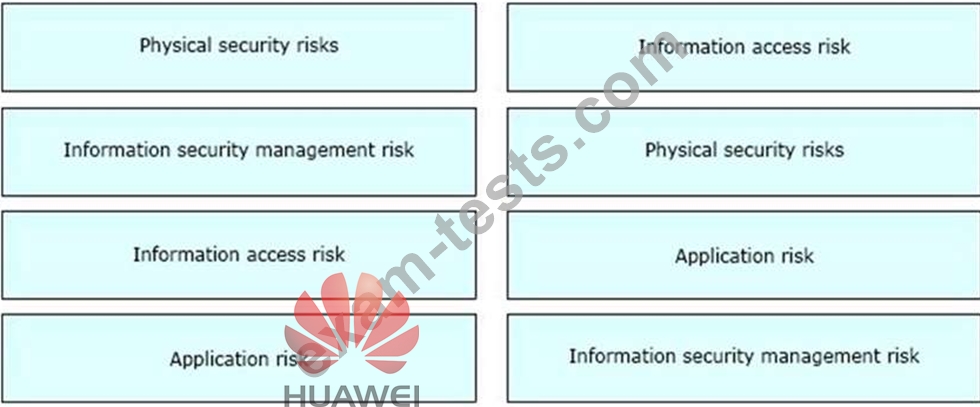
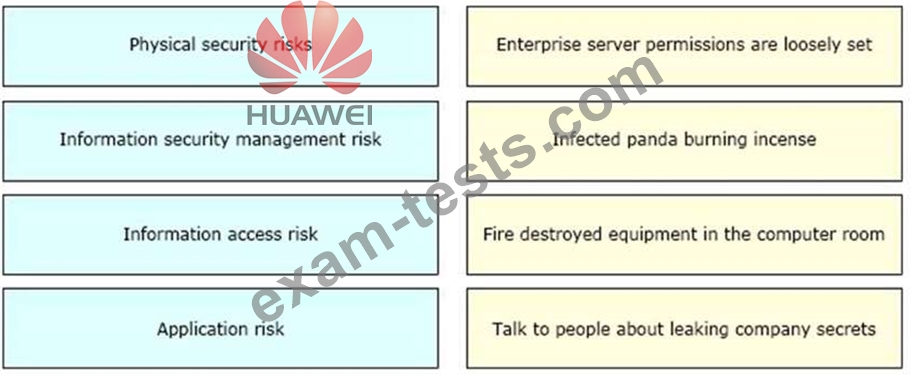
Please match the following information security risks with information security incidents one by one.

Question 55
About the description of the vulnerability scan, which of the following is wrong?