Question 96
We should choose the encryption algorithm according to our own characteristics. When we need to encrypt a large amount of data, it is recommended to use the _____ encryption algorithm to improve the speed of encryption and decryption.
Question 97
For the description of buffer overflow attacks, which of the following options are correct? (Multiple choice)
Question 98
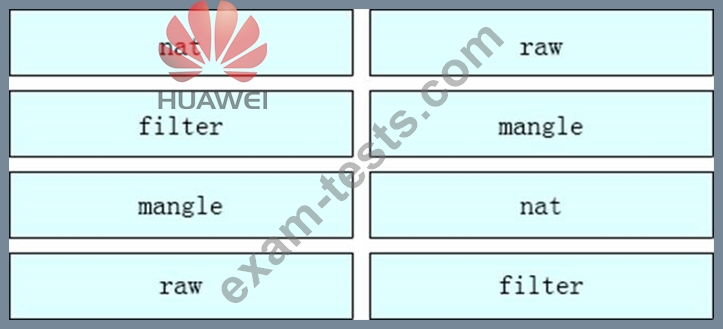
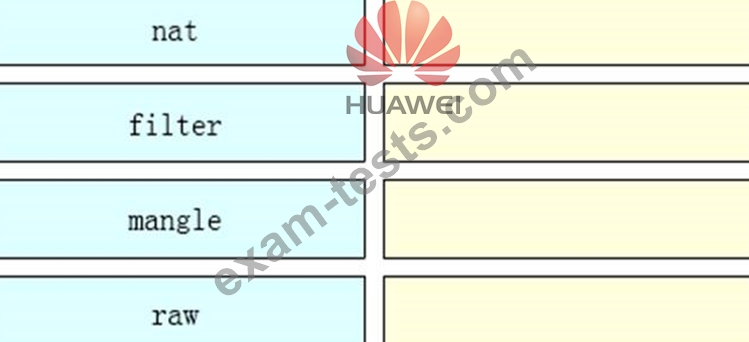
Please sort by iptables table processing priority from largest to smallest.

Question 99
Which of the following is the encryption technology used in the digital envelope?
Question 100
Which of the following NAT technologies can realize a public network address to provide source address translation for multiple private network addresses? (Multiple choice)