Question 106
Drag the warning level of the network security emergency response on the left into the box on the right, and arrange it from top to bottom in order of severity.[fill in the blank]*
Question 107
In the Linux system, which of the following commands is used to query IP address information?
Question 108
( ) Can block discovered network intrusions in real time. (fill in the blank)
Question 109
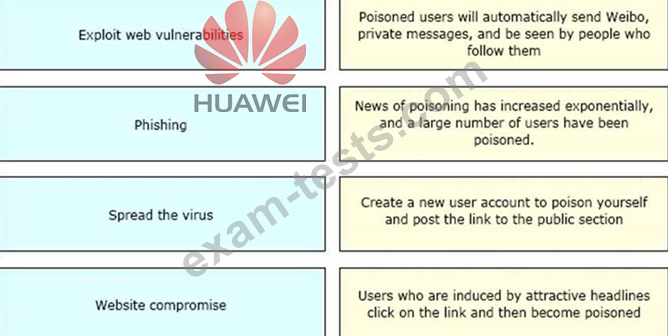
Please match the whole worm virus attack process and attack description.

Question 110
Regarding the description of vulnerability scanning, which of the following is false?



