Question 101
Which of the following is correct configuration strategy for anti-virus policy?
1. Load feature library
2. Configure security policy and reference AV profile
3. Apply and activate license
4. Configure AV Profile
5. Submit
1. Load feature library
2. Configure security policy and reference AV profile
3. Apply and activate license
4. Configure AV Profile
5. Submit
Question 102
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
The purpose of the Internet behavior.
Question 103
URL filtering technology can access control URLs for users according to different time objects and address objects, and achieve the purpose of accurately managing user online behavior.
Question 104
Threats detected by the big data intelligent security analysis platform will be synchronized to each network device at the same time C and then collected from the network device Collect it in the log for continuous learning and optimization.
Question 105
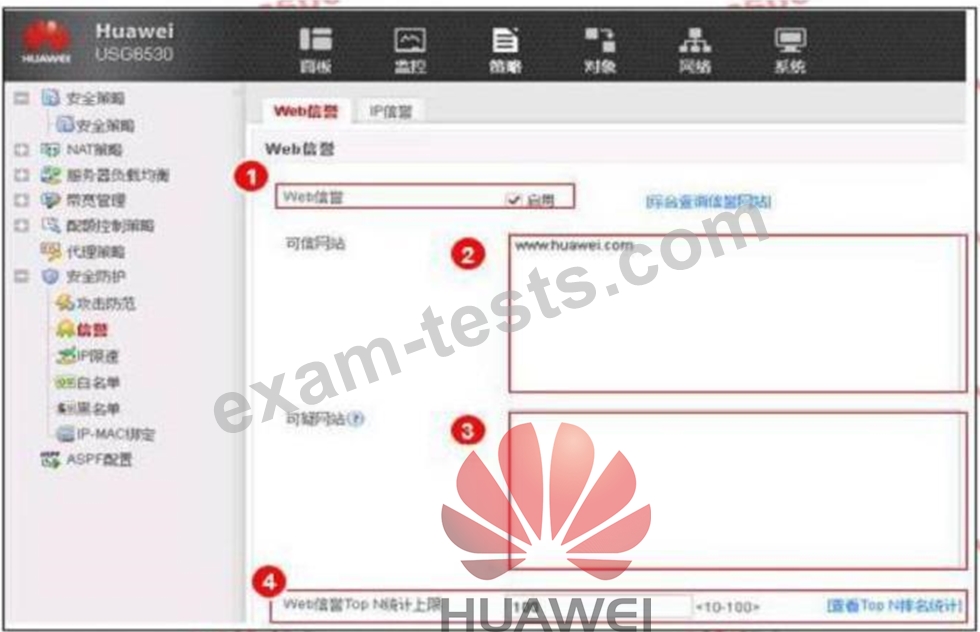
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?