Question 16
Which of the following options describes the IntelliSense engine IAE incorrectly?
Question 17
The network-based intrusion detection system is mainly used to monitor the information of the critical path of the network in real time, listen to all packets on the network, collect data, and divide Analyze the suspicious object, which of the following options are its main features? (multiple choices)
Question 18
Which of the following options does not belong to the security risk of the TCP/IP stack application layer?
Question 19
The following figure is a schematic diagram of the detection file of the firewall and the sandbox system linkage.
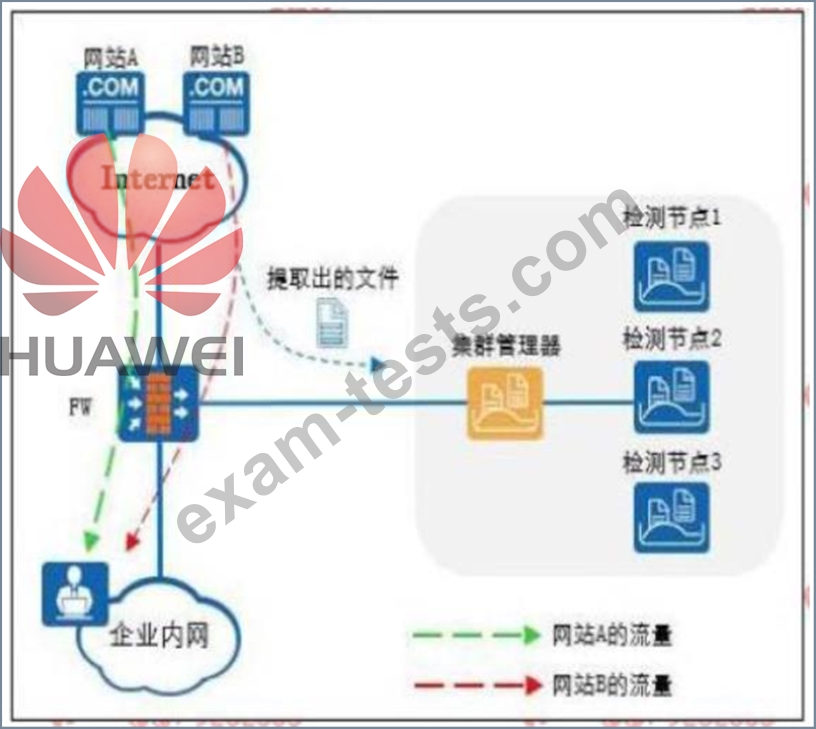
The Web reputation function is enabled on the firewall, and website A is set as a trusted website and website B is set as a suspicious website.
Which of the following statements is correct

The Web reputation function is enabled on the firewall, and website A is set as a trusted website and website B is set as a suspicious website.
Which of the following statements is correct
Question 20
Single-packet attacks are divided into scanning and snooping attacks, malformed packet attacks, and special packet attacks. Ping of death is a special packet attack.

