Question 71
The filter-policy 2000 export command is run in an ISIS process. Which of the following statements about the functions of a filter policy is false?
Question 72
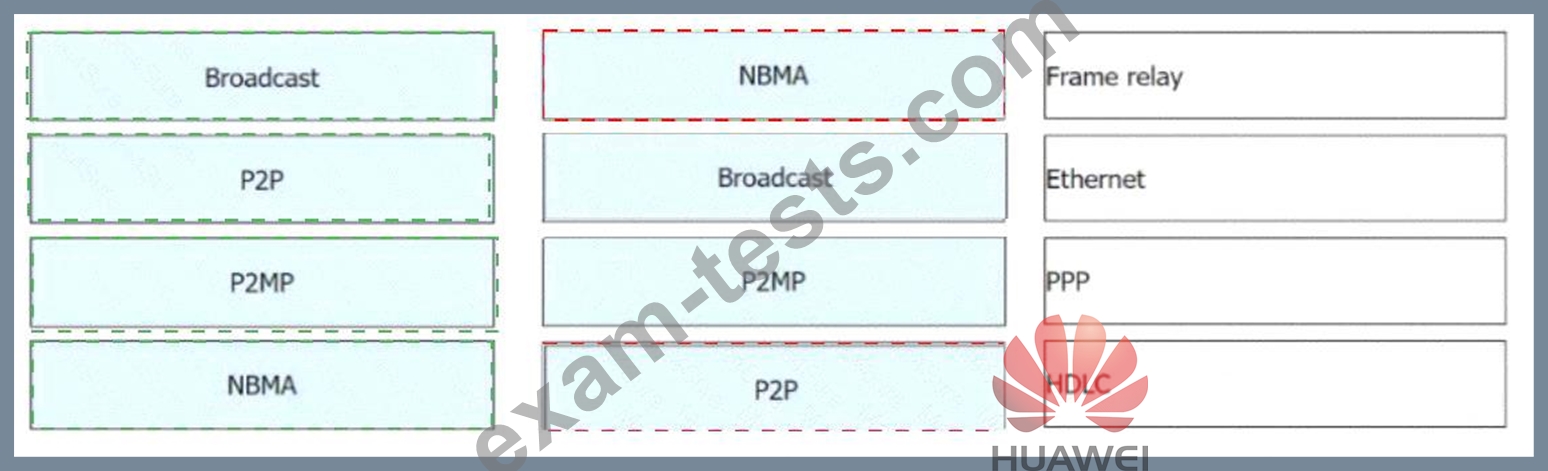
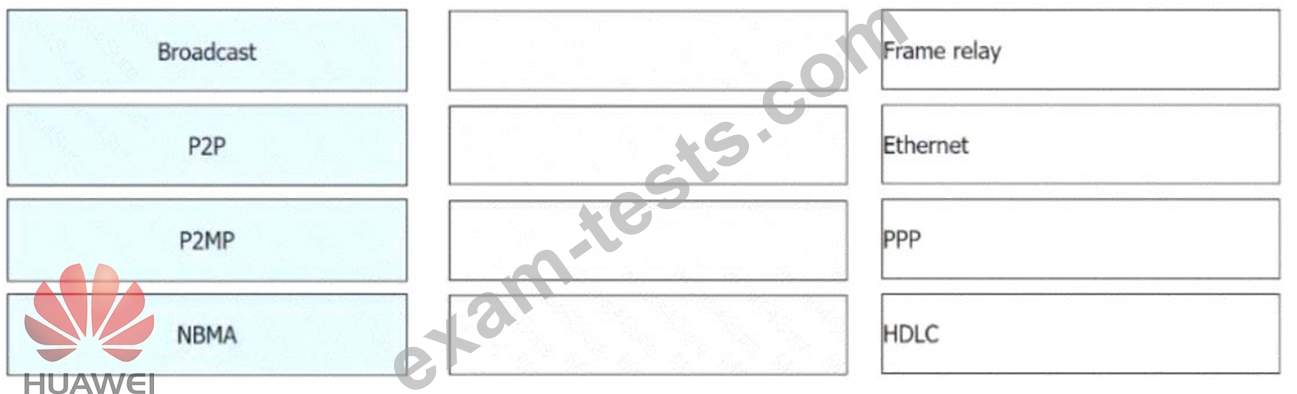
OSPF networks are classified into four types of networks by link layer protocol. Drag the following link layer protocols to the corresponding network types.(Token is reusable)

Question 73
On an OSPF network, if two routers with the same router ID run in different areas and one of the routers is an ASBR, LSA flapping occurs.
Question 74
The Origin attribute is used to define the origin of BGP path information. There are three types of Origin attributes. Which of the following lists the Origin attributes in descending order of priority?
Question 75
When an SSH client accesses an SSH server for the first time and the SSH server's public key is not configured on the SSH client, you can enable first-time authentication on the SSH client. This allows the SSH client to access the SSH server and saves the SSH server's public key on the SSH client. In this way, the next time the SSH client accesses the SSH server, the SSH client can use the saved public key to authenticate the SSH server.