Question 41
Configuring DHCP Snooping can be used to prevent copycat attacks. Which of the following steps need to be included in the configuration process? (Multiple choice)
Question 42
Regarding the description of OSPF's neighbor relationship failure, which of the following statements is false?
Question 43
Regarding the site in the BGP/MPLS IP VPN network architecture. Which of the following descriptions is correct?
Question 44
According to this figure, what can we judge? (Multiple choice)
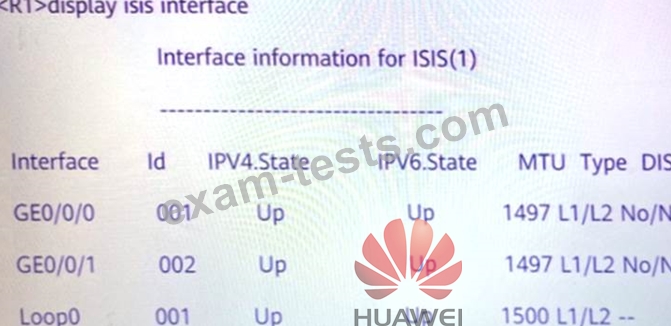

Question 45
In the NFV architecture, what are the specific underlying physical devices? (Multiple choice)

