Question 76
When MPLS is deployed in the network and the network layer protocol is IP, the route corresponding to the FEC must exist in the IP routing table of the LSR, otherwise the label forwarding entry of the FEC will not take effect.
Question 77
The security protection actions that can be performed by a secure MAC address do not include which of the following?
Question 78
Which of the following statements about IPSG is false?
Question 79
What can we infer from this graph? (Multiple choice)
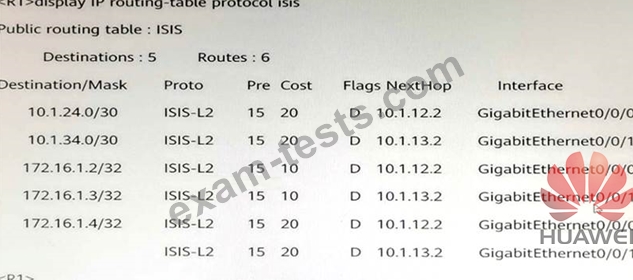

Question 80
R1, R2, R3, and R4 belong to OSPF area 0, and the cost of the link is shown in the figure.
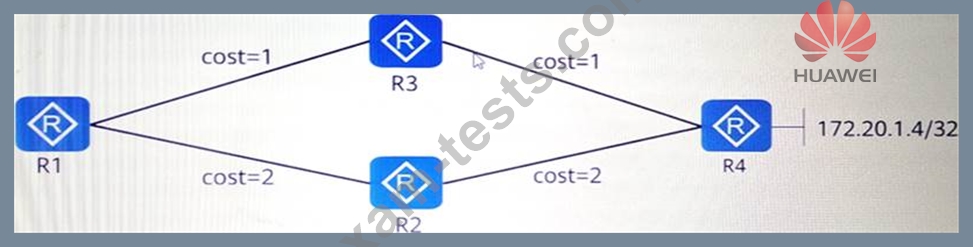
Loopback0 of R1, R2, R3, and R4 is advertised into OSPF. R1, R2, R3, and R4 use Loopback0 as the connection interface to establish an IBGP peer relationship. R1, R2, and R3 are clients of R4. The directly connected network segment 172.20.1.4/32 of R4 is advertised into BGP. Regarding the traffic trend of R1 accessing 172.20.1.4/32, which of the following analysis is correct? (Multiple choice)

Loopback0 of R1, R2, R3, and R4 is advertised into OSPF. R1, R2, R3, and R4 use Loopback0 as the connection interface to establish an IBGP peer relationship. R1, R2, and R3 are clients of R4. The directly connected network segment 172.20.1.4/32 of R4 is advertised into BGP. Regarding the traffic trend of R1 accessing 172.20.1.4/32, which of the following analysis is correct? (Multiple choice)

