Question 136
According to this picture, we can judge:
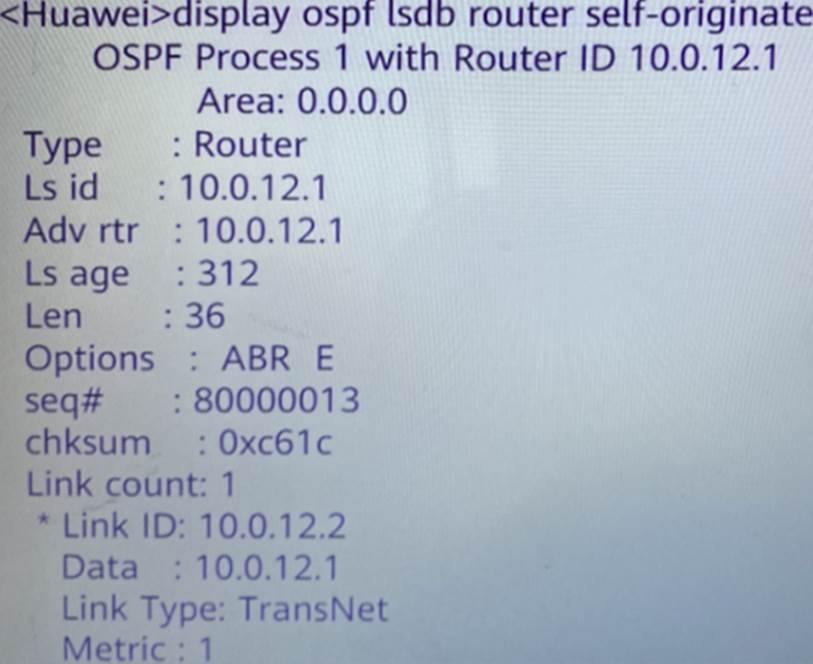

Question 137
An engineer uses two routers to test IPv6 services, and simulates the interconnection between the headquarters and branches by running BGP4+.

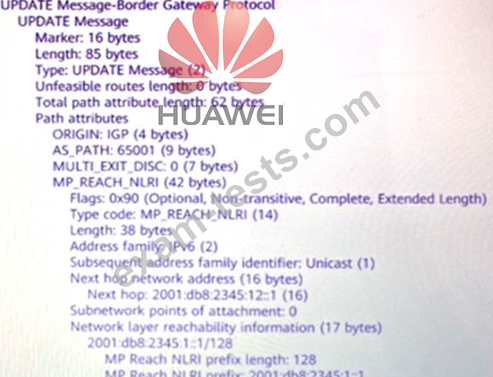
As shown in the figure, an engineer captures the packet to view the update message sent by R1. Regarding the description of the message information, which of the following statements is correct?


As shown in the figure, an engineer captures the packet to view the update message sent by R1. Regarding the description of the message information, which of the following statements is correct?
Question 138
The routing policy tools that BGP can use mainly include Filter-policy and Route-policy, of which Fiter-policy can only filter routes, and Route-policy can only modify routes.
Question 139
Man-in-the-middle attacks or IP/MAC Spooping attacks can lead to information leakage and other hazards, and are more common in the intranet. To prevent man-in-the-middle attacks or IP/MAC Spooping attacks, which of the following configuration methods can be taken.
Question 140
Which of the following options are there for the conditions for the firewall security policy to match traffic? (Multiple choice)

