Question 11
Refer to the exhibit.
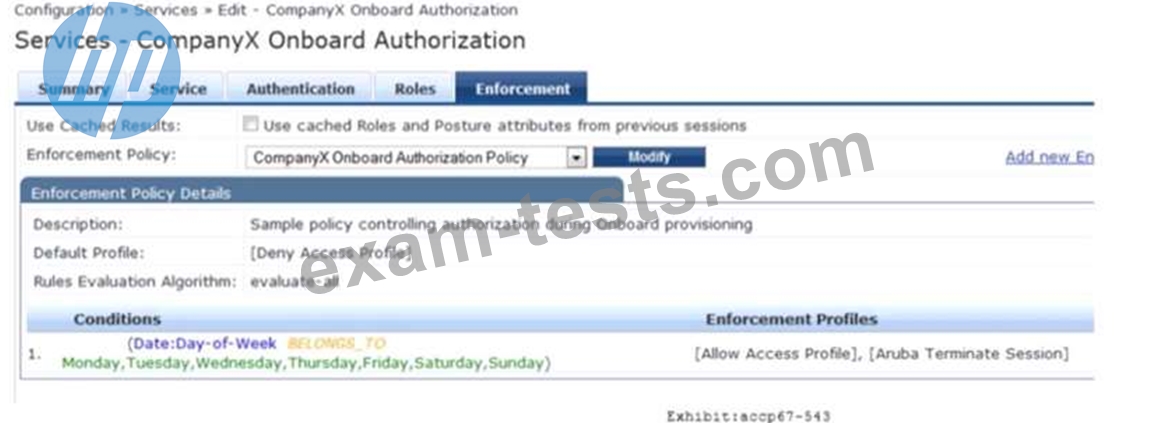
Based on the configuration of the Enforcement Profiles In the Onboard Authorization service shown, which Onboarding action will occur?

Based on the configuration of the Enforcement Profiles In the Onboard Authorization service shown, which Onboarding action will occur?
Question 12
Refer to the exhibit.
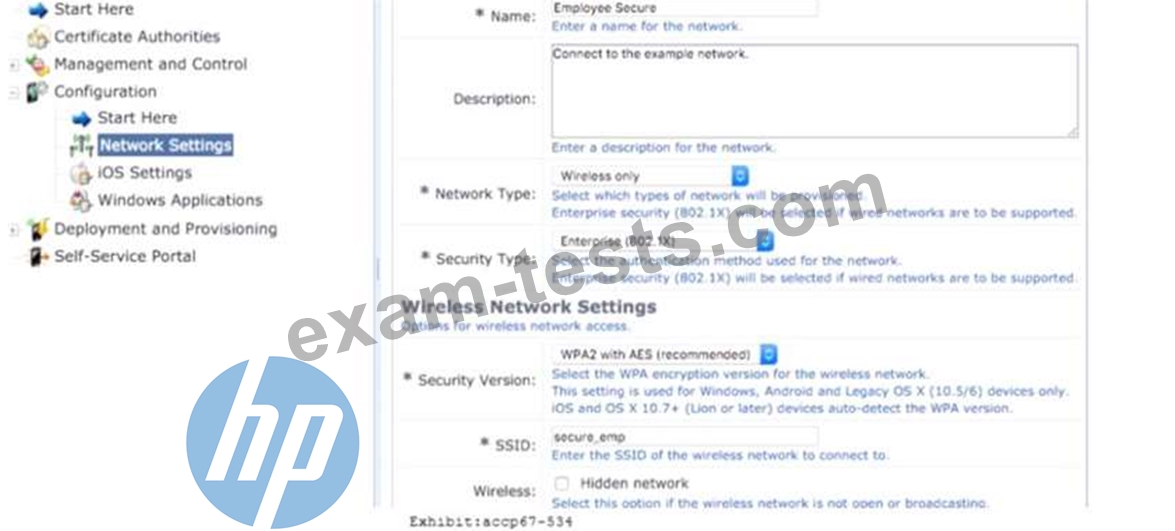
Which statements accurately describe the status of the Onboarded devices in the configuration tor the network settings shown? (Select two.)

Which statements accurately describe the status of the Onboarded devices in the configuration tor the network settings shown? (Select two.)
Question 13
Refer to the exhibit.
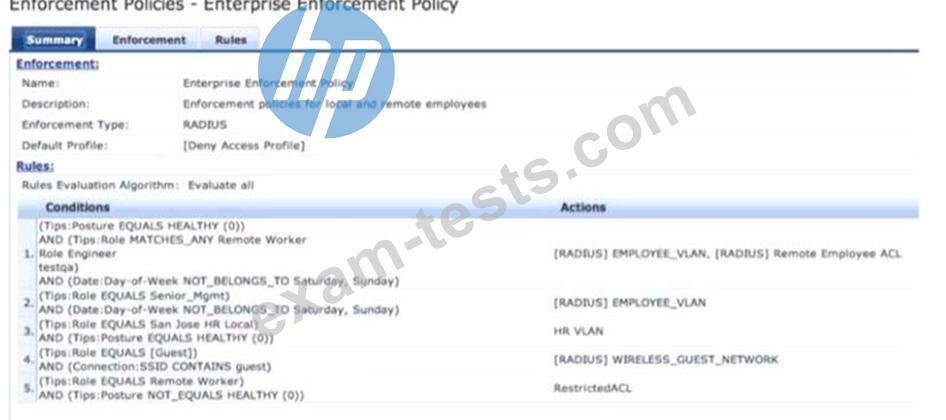
Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?

Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
Question 14
Refer to the exhibit.
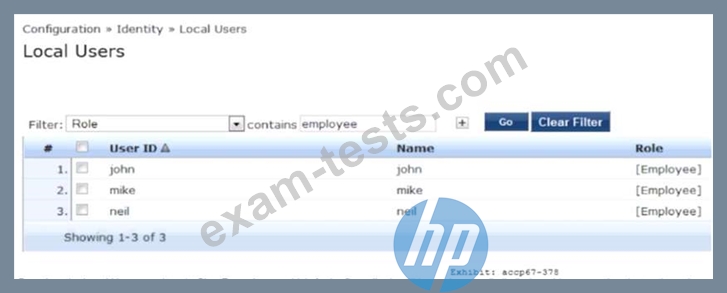

Question 15
An administrator deploys an AP at a branch office. The branch office has a private WAN circuit that provides connectivity to a corporate office controller. An Ethernet port on the AP is connected to a network storage device that contains sensitive information. The administrator is concerned about sending this traffic in clear-text across the private WAN circuit.
What can the administrator do to prevent this problem?
What can the administrator do to prevent this problem?

