Question 11
Refer to the exhibit.
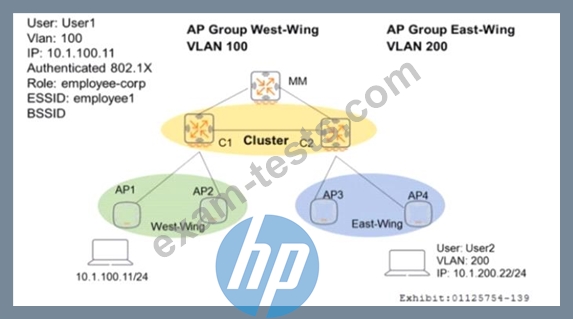
Controllers are configured m a cluster as shown in the exhibit. These are the network details.
* A Mobility Master (MM) manages the cluster.
* The cluster contains two controllers: C l and C2.
* API and AP2 use CI as their Active AP Anchor Controller (A-AAC). with C2 as their Standby AAC (S-AAC).
* AP3 and AP4 use C2 as their A-AAC, with CI as their S-AAC.
User1 establishes a wireless connection via API, where the Active User Anchor Controller (A-UAC) assigned is CI. with C2 as the standby. What happens when User I roams the wireless network and eventually their session is handled by AP3?

Controllers are configured m a cluster as shown in the exhibit. These are the network details.
* A Mobility Master (MM) manages the cluster.
* The cluster contains two controllers: C l and C2.
* API and AP2 use CI as their Active AP Anchor Controller (A-AAC). with C2 as their Standby AAC (S-AAC).
* AP3 and AP4 use C2 as their A-AAC, with CI as their S-AAC.
User1 establishes a wireless connection via API, where the Active User Anchor Controller (A-UAC) assigned is CI. with C2 as the standby. What happens when User I roams the wireless network and eventually their session is handled by AP3?
Question 12
What is true about clustering and AP connections to cluster members?
Question 13
An administrator implements the MultiZone feature and uses two clusters that utilize CPSec. A primary and a data zone are created. MultiZone APs successfully build sessions to the primary cluster but fail to establish sessions to the data zone cluster.
What must the administrator do to solve this problem?
What must the administrator do to solve this problem?
Question 14
What is a primary use case for RPVST+ on AOS-Switches?
Question 15
An administrator deploys Aruba Mobility Controller 7005s to a company's branch offices. The administrator wants to disable the console port to prevent unauthorized access to the controllers.
Which controller command should the administrator use to implement this policy?
Which controller command should the administrator use to implement this policy?

