Question 16
Refer to the exhibit:
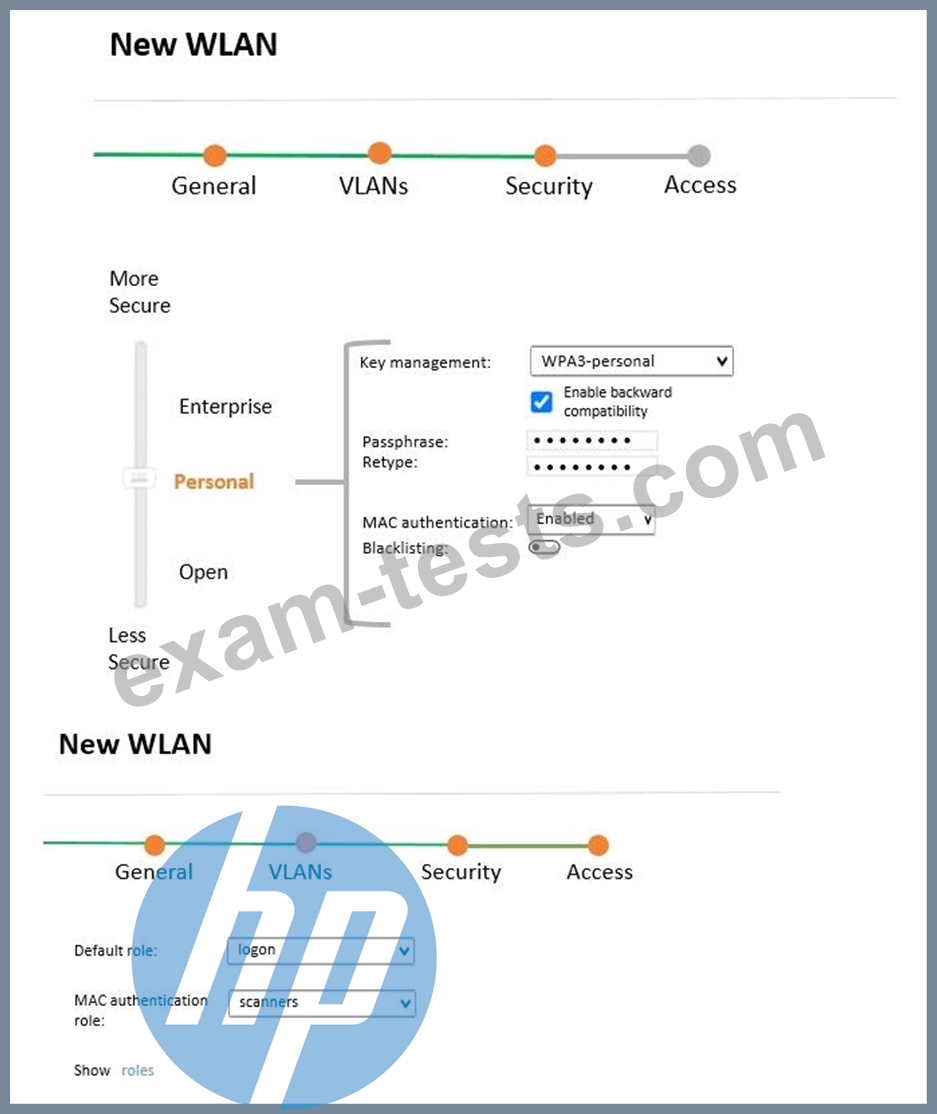
A company acquires ten barcode scanners to run inventory tasks. These WiFi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit.
What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?

A company acquires ten barcode scanners to run inventory tasks. These WiFi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit.
What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
Question 17
Refer to the exhibit.
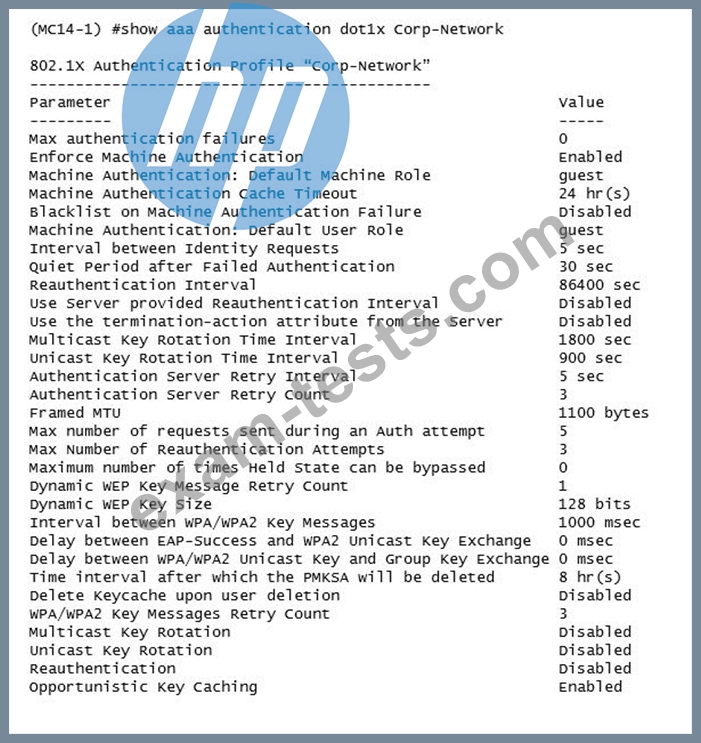
The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?

The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?
Question 18
Refer to the exhibit.

A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit.
Which additional steps must be done to make sure this configuration takes effect over the contractor users?


A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit.
Which additional steps must be done to make sure this configuration takes effect over the contractor users?


