Question 41
A US business-to-consumer (B2C) company is planning to expand to Latin America. They project an initial Latin American customer base of about one million, and a growth rate of around 10% every year for the next 5 years. They anticipate privacy and data protection requirements similar to those in the European Union to come into effect during this time. Their initial analysis indicates that key personal data is stored in the following systems:
1. Legacy mainframe systems that have remained untouched for years and are due to be decommissioned.
2. Salesforce Commerce Cloud Service Cloud, Marketing Cloud, and Community Cloud.
3. The company's CIO tasked the integration architect with ensuring that they can completely delete their Latin American customer's personal data on demand.
Which three requirements should the integration architect consider?
Choose 3 answers
1. Legacy mainframe systems that have remained untouched for years and are due to be decommissioned.
2. Salesforce Commerce Cloud Service Cloud, Marketing Cloud, and Community Cloud.
3. The company's CIO tasked the integration architect with ensuring that they can completely delete their Latin American customer's personal data on demand.
Which three requirements should the integration architect consider?
Choose 3 answers
Question 42
A company's security assessment noted vulnerabilities on the un managed packages in their Salesforce orgs, notably secrets that are easily accessible and in plain text, such as usernames, passwords, and OAuth tokens used in callouts from Salesforce.
Which two persistence mechanisms should an integration architect require to be used to ensure that secrets are protected from deliberate or inadvertent exposure?
Choose 2 answers
Which two persistence mechanisms should an integration architect require to be used to ensure that secrets are protected from deliberate or inadvertent exposure?
Choose 2 answers
Question 43
Universal Containers is building an integration between Salesforce and their Accounting system. The integration will utilize outbound messaging with call back pattern to Salesforce. The security officer would like to understand the authentication solution.
What are the three ways that the call back can authenticate itself to Salesforce?
Choose 3 answers
What are the three ways that the call back can authenticate itself to Salesforce?
Choose 3 answers
Question 44
An Enterprise Customer is planning to implement Salesforce to support case management. Below, is their current system landscape diagram.
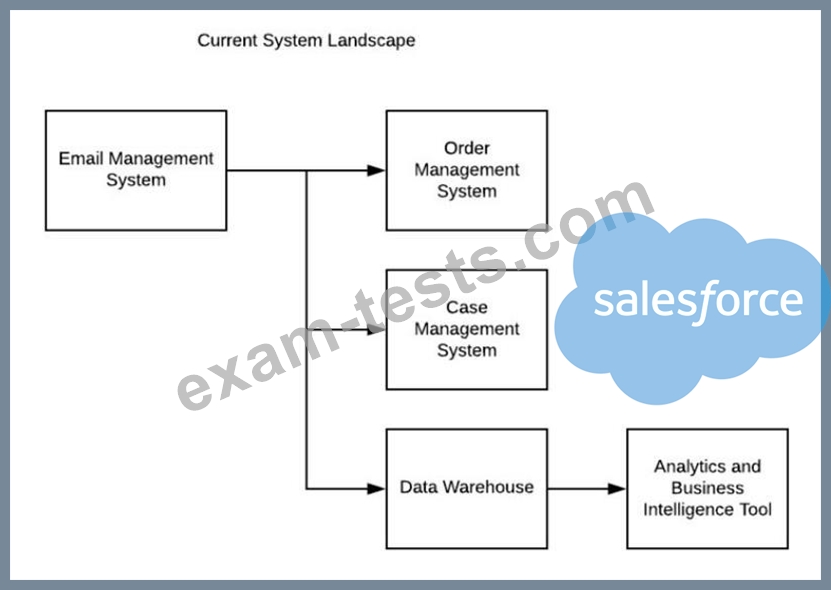
Considering Salesforce capabilities, what should the Integration Architect evaluate when integrating Salesforce with the current system landscape?

Considering Salesforce capabilities, what should the Integration Architect evaluate when integrating Salesforce with the current system landscape?
Question 45
An Architect has received a request to prevent employees that leave the company from accessing data in Salesforce after they are deactivated in the company's HR system.
What should an Architect determine before recommending a solution?
What should an Architect determine before recommending a solution?

