Question 56
Click the Exhibit button.
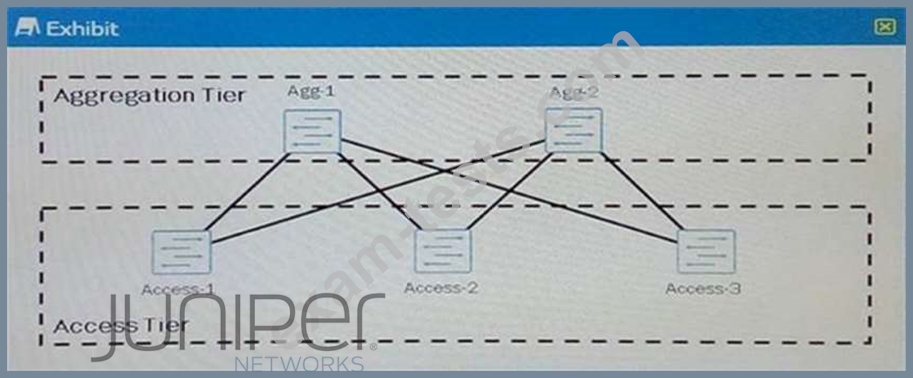
Referring to the exhibit, you are designing a Layer 2 data center and you want to make sure that all the links between the access tier and the aggregation tier are used.
What should you do to accomplish this task?

Referring to the exhibit, you are designing a Layer 2 data center and you want to make sure that all the links between the access tier and the aggregation tier are used.
What should you do to accomplish this task?
Question 57
Your corporate network is located in a single, multifloor building. Several smaller, remote buildings connect into your main corporate network.
Which topology describes your network?
Which topology describes your network?
Question 58
You are designing a WAN implementation to securely connect two remote sites to the corporate office. A public Internet connection will be used for the connections.
Which statement is true in this situation?
Which statement is true in this situation?
Question 59
You are designing a data center network that will require the rapid deployment and removal of security features between virtual machines based on triggered traffic flows.
The data center will require the ability to scale up and down rapidly according to traffic load, and then release resources when security services are not needed.
In this scenario, which type of security design would fulfill this requirement?
The data center will require the ability to scale up and down rapidly according to traffic load, and then release resources when security services are not needed.
In this scenario, which type of security design would fulfill this requirement?
Question 60
What would be a Juniper Networks best practice for a network management network?

