Question 16
What is an advantage of the Junos Telemetry Interface(JTI) over SNMP?
Question 17
What are two protocols used by NorthStar Controller to discover the network topology?(Choose two) **************
Question 18
Which Juniper product is used to remotely provision the NFX250 platform for Network Functions Virtualization?
Question 19
Juniper Networks supports which two alternatives to layer 2 loop prevention protocols, such as STP, in an underlay network? (Choose two)
Question 20
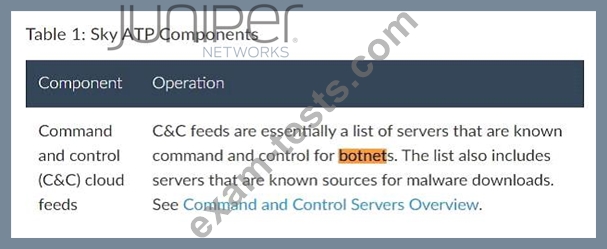
Devices in your data center have become unwilling participants of botnet attacks.
In this scenario, which security technology should you use to stop this behavior?
In this scenario, which security technology should you use to stop this behavior?
Premium Bundle
Newest JN0-211 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing JN0-211 Exam! BraindumpsPass.com now offer the updated JN0-211 exam dumps, the BraindumpsPass.com JN0-211 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com JN0-211 pdf dumps with Exam Engine here: