Question 1
Click the Exhibit button.
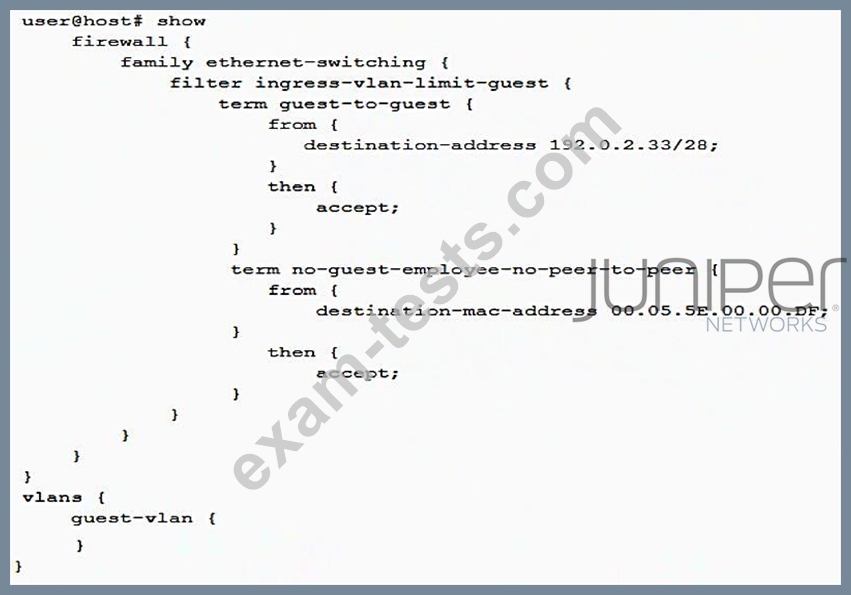
A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic.
In this scenario, what must you do to implement the security policy?

A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic.
In this scenario, what must you do to implement the security policy?
Question 2
What are two methods for reducing the size of an OSPF link-state database? (Choose two.)
Question 3
What BGP attribute is mostly likely to influence a remote AS that you do not peer with?
Question 4
When configuring firewall filters, which function does the interface-specificparameter enable on an EX Series switch?
Question 5
Which statement is true about IP-IP tunnels?

