Question 26
You are a service provider and have multiple customers in a building.
You are installing a new switch that can host all of your customers. However, you would like to ensure that one customer cannot see or broadcast to another customer.
You would also like to have them use a common gateway IP address from the building. What should be used to provide this access?
You are installing a new switch that can host all of your customers. However, you would like to ensure that one customer cannot see or broadcast to another customer.
You would also like to have them use a common gateway IP address from the building. What should be used to provide this access?
Question 27
Routet-1 and Router-2 must connect through the Internet using a tunneling technology. Hosts that are connected to Router-1 and Router-2 will be sending traffic up to 1500 bytes. The maximum segment size that is supported across the path is 1520 bytes.
Which tunneling technology will allow this communication to take place?
Which tunneling technology will allow this communication to take place?
Question 28
You notice that currently two MAC addresses are associated with a single access port in the bridge table of one of your EX Series switches.
What are two explanations for this behavior? (Choose two.)
What are two explanations for this behavior? (Choose two.)
Question 29
You have configured storm control on your network devices. Your network has grown and you no longer have time to investigate each occurrence of a storm control violation. You want to enable a port to automatically be re-enabled after a storm violation.
In this scenario, which Junos OS configuration timeout would accomplish this task?
In this scenario, which Junos OS configuration timeout would accomplish this task?
Question 30
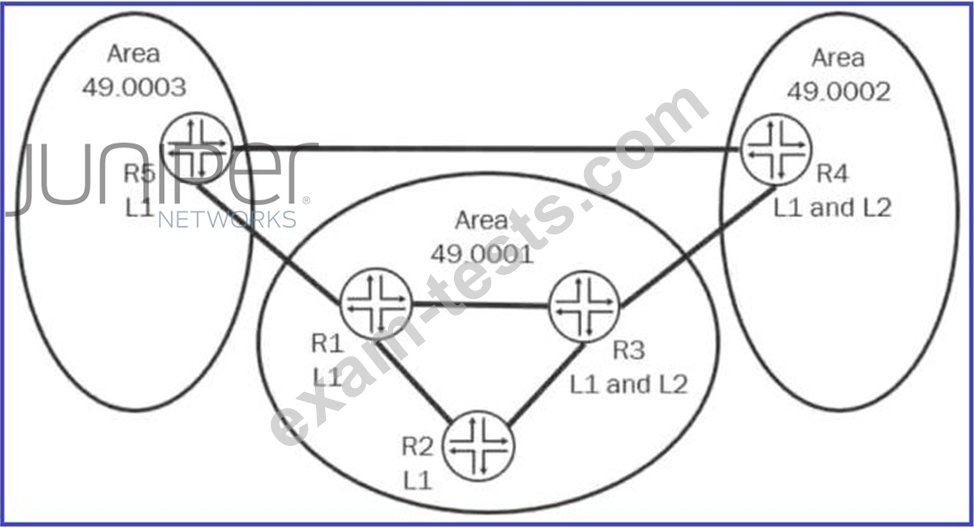
Referring to the exhibit, which two statements are correct? (Choose two.)