Question 51
You are asked to secure your network against TOR network traffic.
Which two Juniper products would accomplish this task? (Choose two.)
Which two Juniper products would accomplish this task? (Choose two.)
Question 52
You are asked to look at a configuration that is designed to take all traffic with a specific source ip address and forward the traffic to a traffic analysis server for further evaluation. The configuration is no longer working as intended.
Referring to the exhibit which change must be made to correct the configuration?
Referring to the exhibit which change must be made to correct the configuration?
Question 53
In a Juniper ATP Appliance, what would be a reason for the mitigation rule to be in the failed-remove state?
Question 54
Click the Exhibit button.
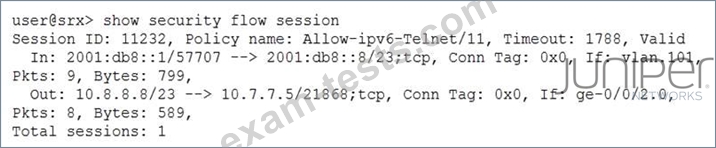
Which type of NAT is shown in the exhibit?

Which type of NAT is shown in the exhibit?
Question 55
Click the Exhibit button.
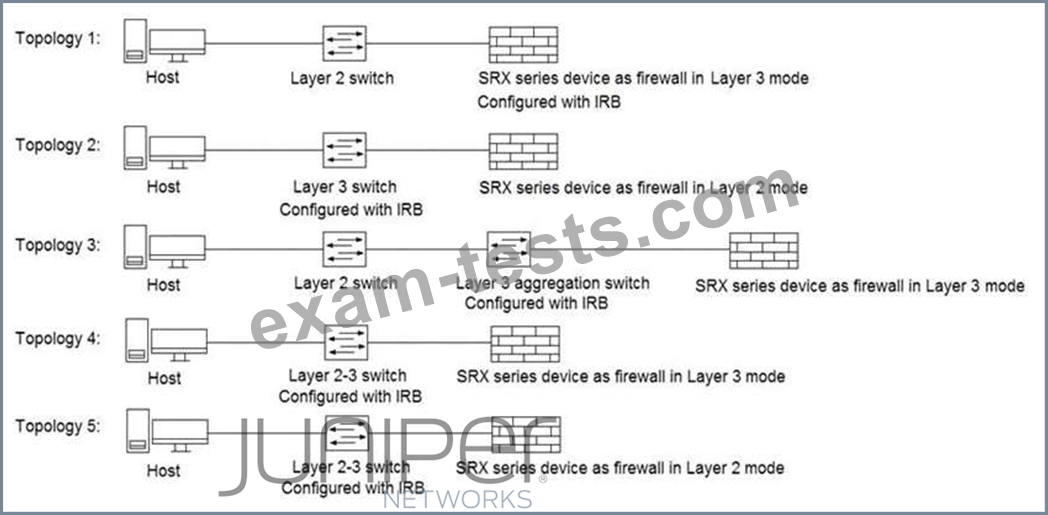
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)

Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)

