Question 1
Which Junos security feature is used for signature-based attack prevention?
Question 2
Click the Exhibit button.
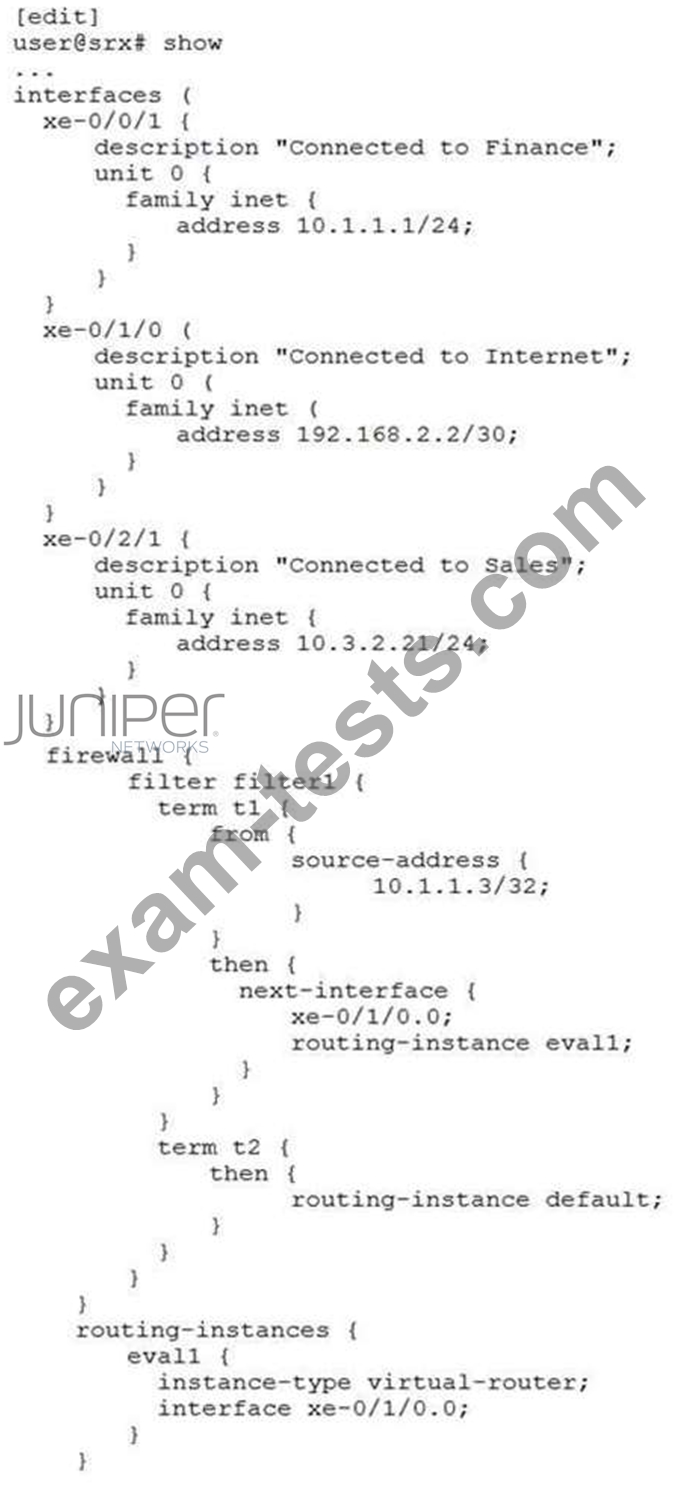
You are asked to look at a configuration that is designed to take all traffic with a specific source IP address and forward the traffic to a traffic analysis server for further evaluation. The configuration is not working as intended.
Referring to the exhibit, which change must be made to correct the configuration?

You are asked to look at a configuration that is designed to take all traffic with a specific source IP address and forward the traffic to a traffic analysis server for further evaluation. The configuration is not working as intended.
Referring to the exhibit, which change must be made to correct the configuration?
Question 3
Click the Exhibit button.
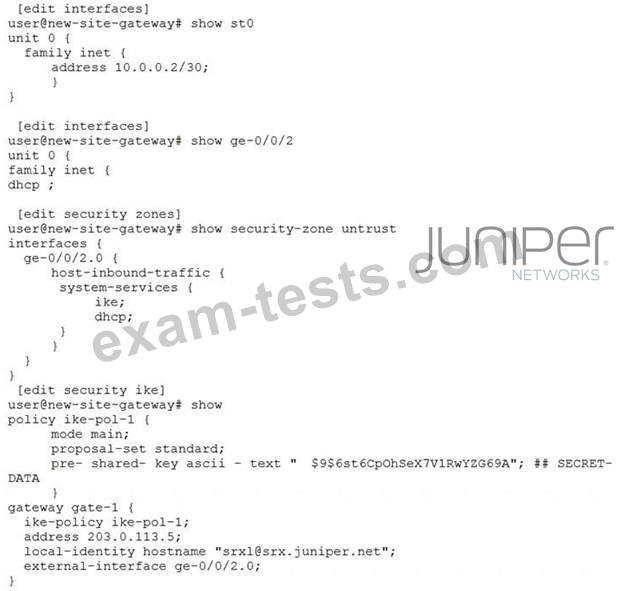
Your company has purchased a competitor and now must connect the new network to the existing one. The competitor's gateway device is receiving its ISP address using DHCP. Communication between the two sites must be secured; however, obtaining a static public IP address for the new site gateway is not an option at this time. The company has several requirements for this solution:
* A site-to-site IPsec VPN must be used to secure traffic between the two sites;
* The IKE identity on the new site gateway device must use the hostname option; and
* Internet traffic from each site should exit through its local Internet connection.
The configuration shown in the exhibit has been applied to the new site's SRX, but the secure tunnel is not working.
In this scenario, what configuration change is needed for the tunnel to come up?

Your company has purchased a competitor and now must connect the new network to the existing one. The competitor's gateway device is receiving its ISP address using DHCP. Communication between the two sites must be secured; however, obtaining a static public IP address for the new site gateway is not an option at this time. The company has several requirements for this solution:
* A site-to-site IPsec VPN must be used to secure traffic between the two sites;
* The IKE identity on the new site gateway device must use the hostname option; and
* Internet traffic from each site should exit through its local Internet connection.
The configuration shown in the exhibit has been applied to the new site's SRX, but the secure tunnel is not working.
In this scenario, what configuration change is needed for the tunnel to come up?
Question 4
Click the Exhibit button.
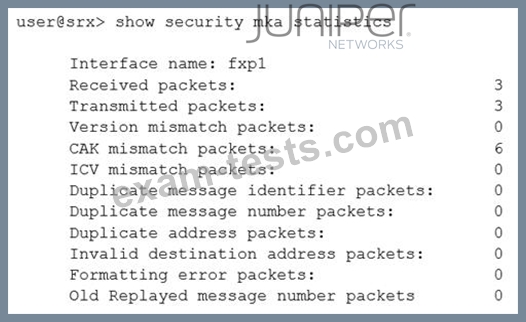
While configuring the SRX345, you review the MACsec connection between devices and note that it is not working.
Referring to the exhibit, which action would you use to identify problem?

While configuring the SRX345, you review the MACsec connection between devices and note that it is not working.
Referring to the exhibit, which action would you use to identify problem?
Question 5
You correctly configured a security policy to deny certain traffic, but logs reveal that traffic is still allowed.
Which specific traceoption flag will help you troubleshoot this problem?
Which specific traceoption flag will help you troubleshoot this problem?

