Question 21
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
Question 22
Your company uses Gmail as a corporate email solution.
You purchase a Microsoft 365 subscription and plan to move all email data to Microsoft Exchange Online.
You plan to perform the migration by using the Exchange admin center.
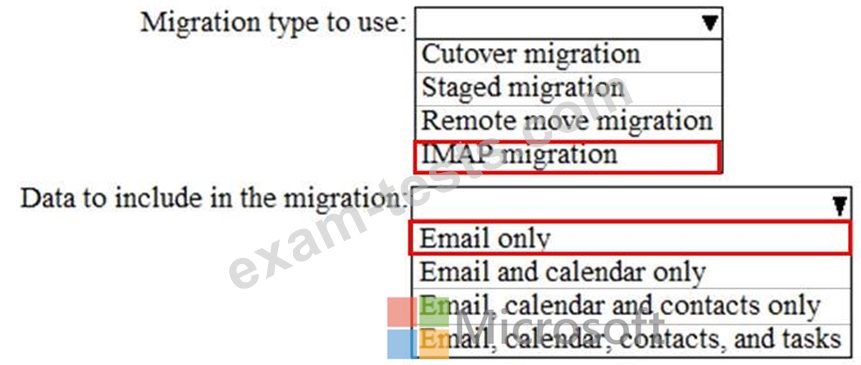
You need to recommend which type of migration to use and which type of data to migrate.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
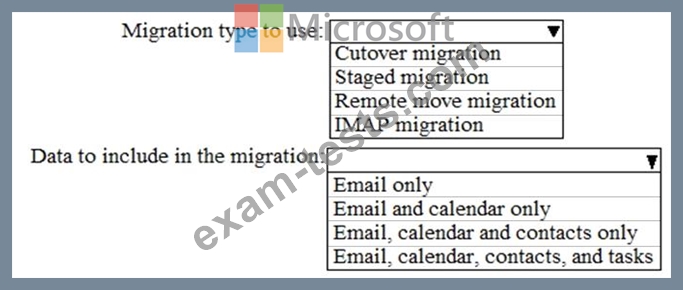
You purchase a Microsoft 365 subscription and plan to move all email data to Microsoft Exchange Online.
You plan to perform the migration by using the Exchange admin center.
You need to recommend which type of migration to use and which type of data to migrate.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 23
Your company has offices in several cities and 100.000 users.
The network contains an Active Directory domain contoso.com.
You purchase Microsoft 365 and plan to deploy several Microsoft 365 services.
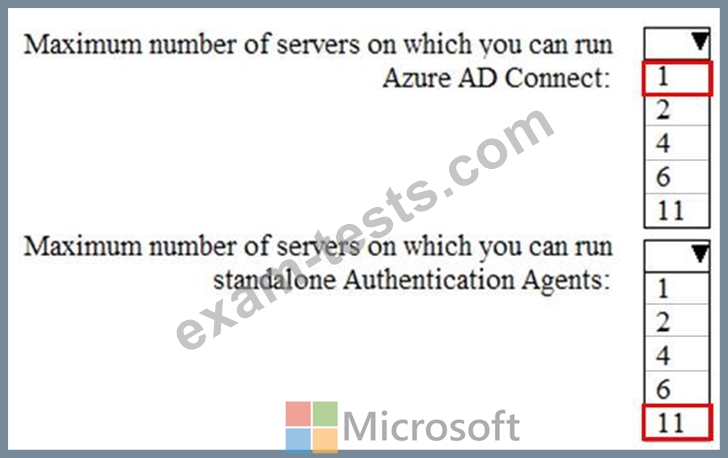
You are evaluating the implementation of pass-through authentication and seamless SSO. Azure AD Connect will NOT be in staging mode.
You need to identify the redundancy limits for the planned implementation.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
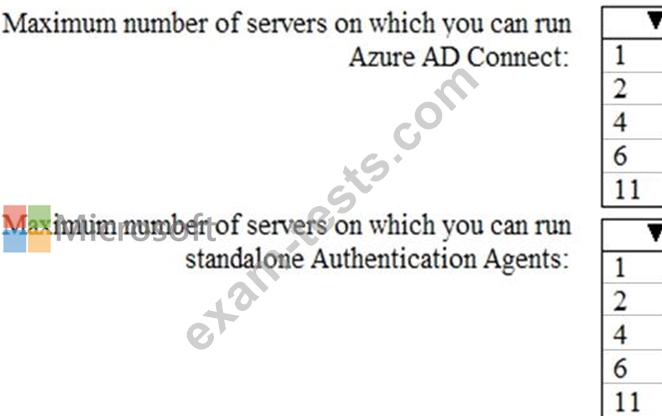
The network contains an Active Directory domain contoso.com.
You purchase Microsoft 365 and plan to deploy several Microsoft 365 services.
You are evaluating the implementation of pass-through authentication and seamless SSO. Azure AD Connect will NOT be in staging mode.
You need to identify the redundancy limits for the planned implementation.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 24
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
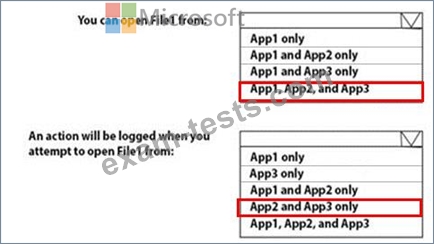
You have three applications App1, App2, App3. The Apps use files that have the same file extensions.
Your company uses Windows Information Protection (WIP). WIP has the following configurations:
Windows Information Protection mode: Silent
Protected apps: App1
Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.

You have three applications App1, App2, App3. The Apps use files that have the same file extensions.
Your company uses Windows Information Protection (WIP). WIP has the following configurations:
Windows Information Protection mode: Silent
Protected apps: App1
Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.

Question 25
Your network contains an on-premises Active Directory domain named Contoso.com.
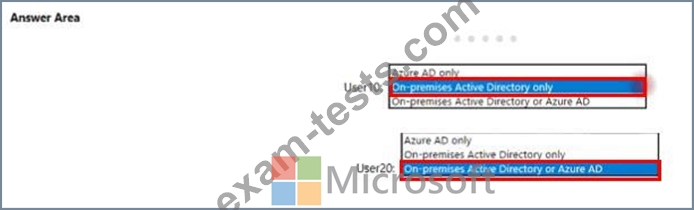
Your company purchase a Microsoft 365 subscription and establishes a hybrid deployment of Azure Active Directory (Azure AD) by using password hash synchronization.
You need to identify where an administrator can reset the password of each new user.
What should you identify? To answer, select the appropriate option in the area.
NOTE: Each correct selection is worth point.
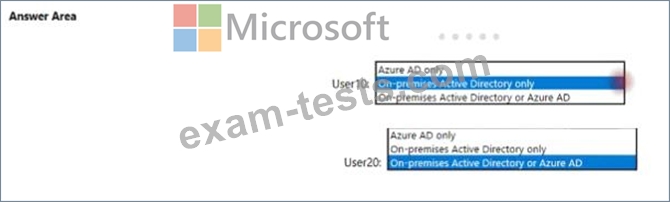
Your company purchase a Microsoft 365 subscription and establishes a hybrid deployment of Azure Active Directory (Azure AD) by using password hash synchronization.
You need to identify where an administrator can reset the password of each new user.
What should you identify? To answer, select the appropriate option in the area.
NOTE: Each correct selection is worth point.