Question 146
You have a Microsoft Azure Active Directory (Azure AD) tenant.
Your company implements Windows Information Protection (WIP).
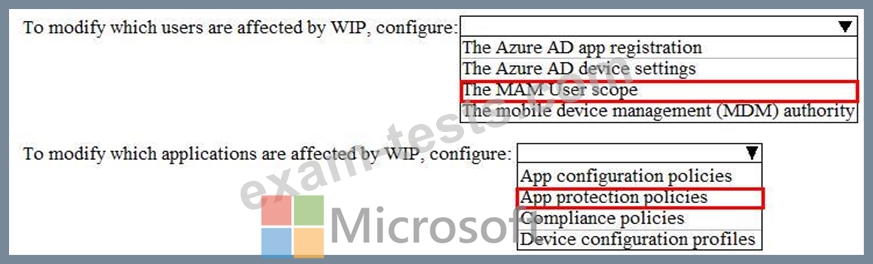
You need to modify which users and applications are affected by WIP.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
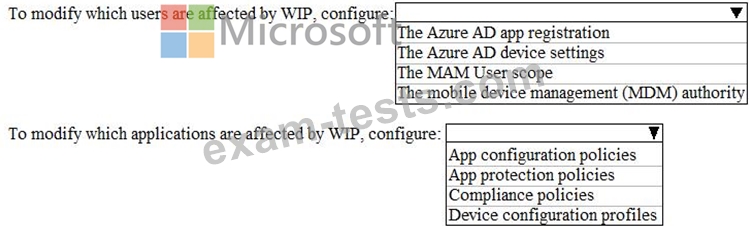
Your company implements Windows Information Protection (WIP).
You need to modify which users and applications are affected by WIP.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 147
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.

The domain syncs to an Azure Active Directory (Azure AD) tenant named contoso.com as shown in the exhibit. (Click the Exhibit tab.)
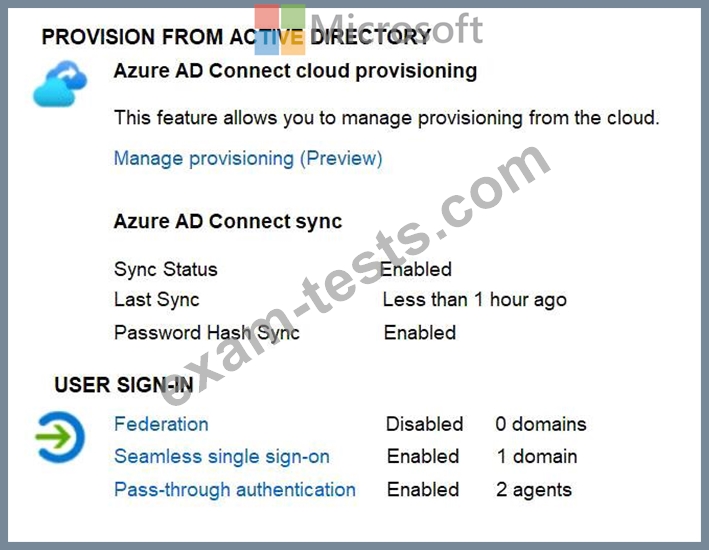
User2 fails to authenticate to Azure AD when signing in as [email protected].
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the Azure Active Directory admin center, you add fabrikam.com as a custom domain. You instruct User2 to sign in as [email protected].
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.

The domain syncs to an Azure Active Directory (Azure AD) tenant named contoso.com as shown in the exhibit. (Click the Exhibit tab.)

User2 fails to authenticate to Azure AD when signing in as [email protected].
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the Azure Active Directory admin center, you add fabrikam.com as a custom domain. You instruct User2 to sign in as [email protected].
Does this meet the goal?
Question 148
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
* Users must be able to authenticate during business hours only.
* Authentication requests must be processed successfully if a single server fails.
* When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
* Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that contains a pass-through authentication model. You install an Authentication Agent on three servers and configure seamless SSO.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
* Users must be able to authenticate during business hours only.
* Authentication requests must be processed successfully if a single server fails.
* When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
* Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that contains a pass-through authentication model. You install an Authentication Agent on three servers and configure seamless SSO.
Does this meet the goal?
Question 149
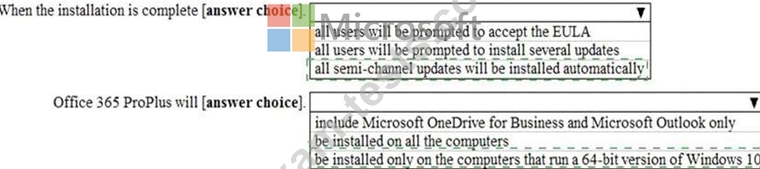
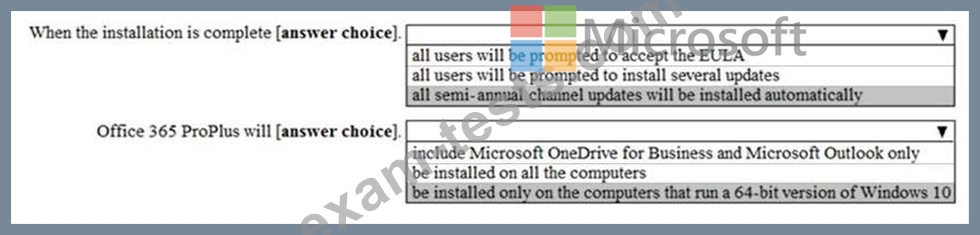
Your company has 500 client computers that run Windows 10.
You plan to deploy Microsoft Office 365 ProPlus to all the computers.
You create the following XML file for the planned deployment.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

You plan to deploy Microsoft Office 365 ProPlus to all the computers.
You create the following XML file for the planned deployment.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Question 150
Your network contains an Active Directory domain named contoso.com.
All users authenticate by using a third-party authentication solution.
You purchase Microsoft 365 and plan to implement several Microsoft 365 services.
You need to recommend an identity strategy that meets the following requirements:
Provides seamless SSO
Minimizes the number of additional servers required to support the solution Stores the passwords of all the users in Microsoft Azure Active Directory (Azure AD) Ensures that all the users authenticate to Microsoft 365 by using their on-premises user account You are evaluating the implementation of federation.
Which two requirements are met by using federation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
All users authenticate by using a third-party authentication solution.
You purchase Microsoft 365 and plan to implement several Microsoft 365 services.
You need to recommend an identity strategy that meets the following requirements:
Provides seamless SSO
Minimizes the number of additional servers required to support the solution Stores the passwords of all the users in Microsoft Azure Active Directory (Azure AD) Ensures that all the users authenticate to Microsoft 365 by using their on-premises user account You are evaluating the implementation of federation.
Which two requirements are met by using federation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.