Question 56
Your company has a Microsoft 365 tenant.
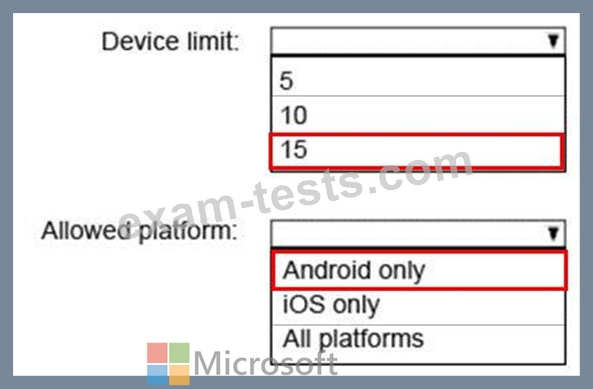
You plan to allow users from the engineering department to enroll their mobile device in mobile device management (MDM).
The device type restrictions are configured as shown in the following table.
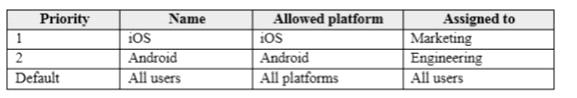
The device limit restrictions are configured as shown in the following table.
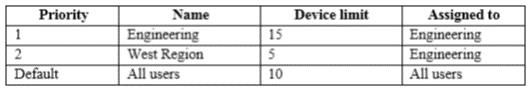
What is the effective configuration for the members of the Engineering group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You plan to allow users from the engineering department to enroll their mobile device in mobile device management (MDM).
The device type restrictions are configured as shown in the following table.

The device limit restrictions are configured as shown in the following table.

What is the effective configuration for the members of the Engineering group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 57
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a hybrid deployment of Microsoft 365 that contains the objects shown in the following table.

Azure AD Connect has the following settings:
Password Hash Sync: Enabled
Password writeback: Enabled
Group writeback: Enabled
You need to add User2 to Group 2.
Solution: From Azure PowerShell, you run the Set-AzureADGroup cmdlet.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a hybrid deployment of Microsoft 365 that contains the objects shown in the following table.

Azure AD Connect has the following settings:
Password Hash Sync: Enabled
Password writeback: Enabled
Group writeback: Enabled
You need to add User2 to Group 2.
Solution: From Azure PowerShell, you run the Set-AzureADGroup cmdlet.
Does this meet the goal?
Question 58
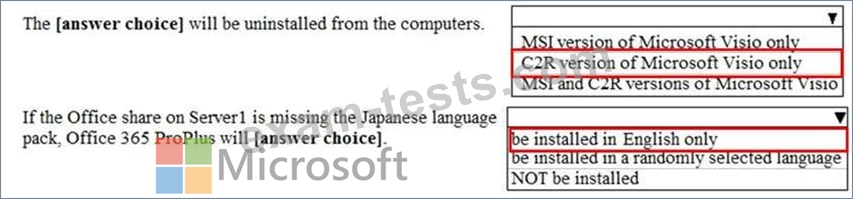
You have a Microsoft 365 subscription.
You use the Microsoft Office Deployment tool to install Office 365 ProPlus.
You create a configuration file that contains the following settings.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

You use the Microsoft Office Deployment tool to install Office 365 ProPlus.
You create a configuration file that contains the following settings.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Question 59
You have a Microsoft 365 subscription that contains a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
In the tenant, you create a user named User1.
You need to ensure that User1 can publish retention labels from the Security & Compliance admin center. The solution must use the principle of least privilege.
To which role group should you add User1?
In the tenant, you create a user named User1.
You need to ensure that User1 can publish retention labels from the Security & Compliance admin center. The solution must use the principle of least privilege.
To which role group should you add User1?
Question 60
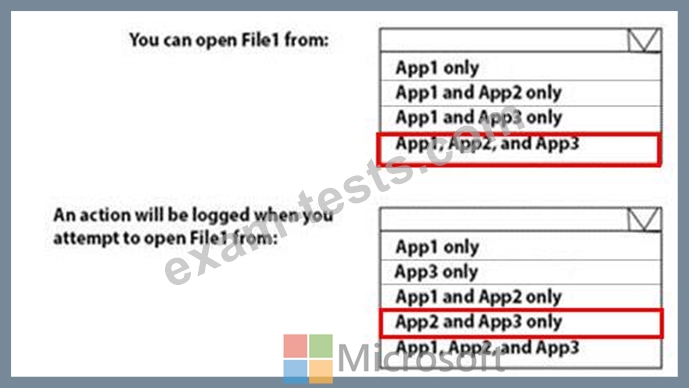
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You have three applications App1, App2, App3. The Apps use files that have the same file extensions.
Your company uses Windows Information Protection (WIP). WIP has the following configurations:
Windows Information Protection mode: Silent
Protected apps: App1
Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.

You have three applications App1, App2, App3. The Apps use files that have the same file extensions.
Your company uses Windows Information Protection (WIP). WIP has the following configurations:
Windows Information Protection mode: Silent
Protected apps: App1
Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.