Question 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
Question 2
You are developing an interactive invoicing application mat will be used by end users. The application will have the following features:
* Save invoices generated by a user to the user s OneDrive for Business.
* Email daily automated reminders.
You need to identify which permissions to grant for the application features. The solution must use the principle of least privilege. Which permission type should you grant for each feature? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

* Save invoices generated by a user to the user s OneDrive for Business.
* Email daily automated reminders.
You need to identify which permissions to grant for the application features. The solution must use the principle of least privilege. Which permission type should you grant for each feature? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 3
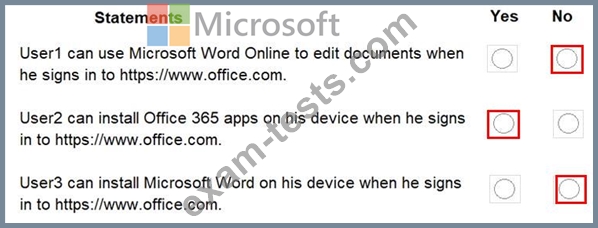
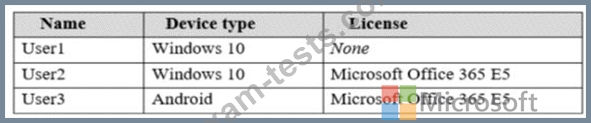
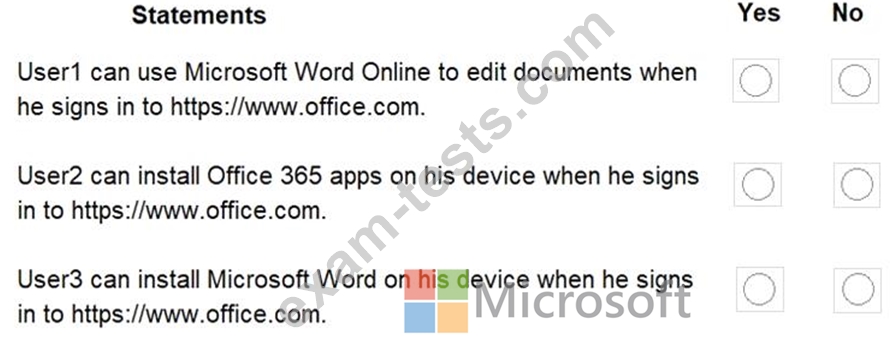
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.
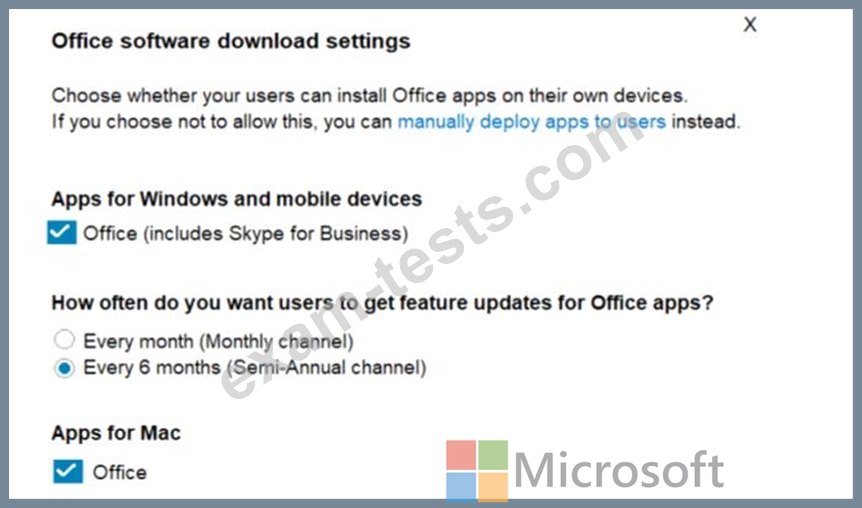
You configure the Office software download settings as shown in the exhibit. (Click the Exhibit tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You configure the Office software download settings as shown in the exhibit. (Click the Exhibit tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Question 4
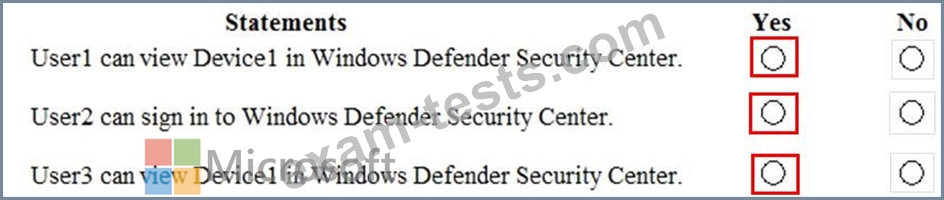
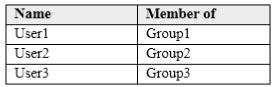
You have a Microsoft Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
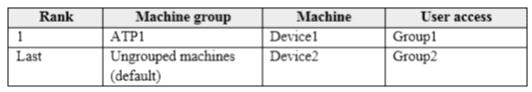
Your company uses Windows Defender Advanced Threat Protection (ATP). Windows Defender ATP contains the roles shown in the following table.

Windows Defender ATP contains the device groups shown in the following table.
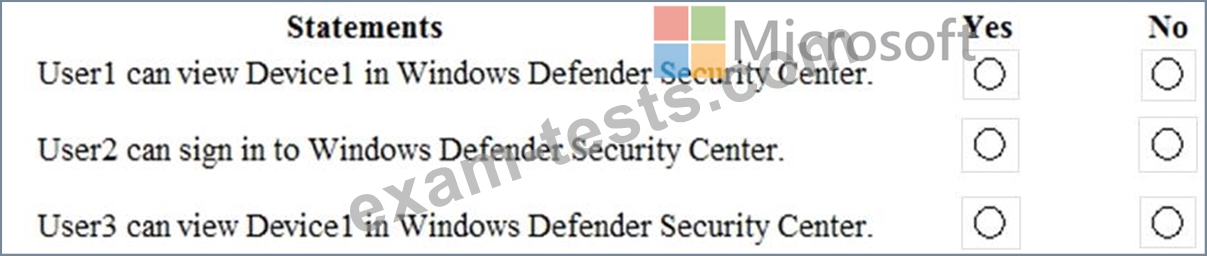
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Your company uses Windows Defender Advanced Threat Protection (ATP). Windows Defender ATP contains the roles shown in the following table.

Windows Defender ATP contains the device groups shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Question 5
Your network contains an on-premises Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant.
The on-premises network contains a file server named Server1. Server1 has a share named Share1 that contains company documents.
Your company purchases a Microsoft 365 subscription.
You plan to migrate data from Share1 to Microsoft 365. Only data that was created or modified during the last three months will be migrated.
You need to identify all the files in Share1 that were modified or created during the last 90 days.
What should you use?
The on-premises network contains a file server named Server1. Server1 has a share named Share1 that contains company documents.
Your company purchases a Microsoft 365 subscription.
You plan to migrate data from Share1 to Microsoft 365. Only data that was created or modified during the last three months will be migrated.
You need to identify all the files in Share1 that were modified or created during the last 90 days.
What should you use?