Question 146
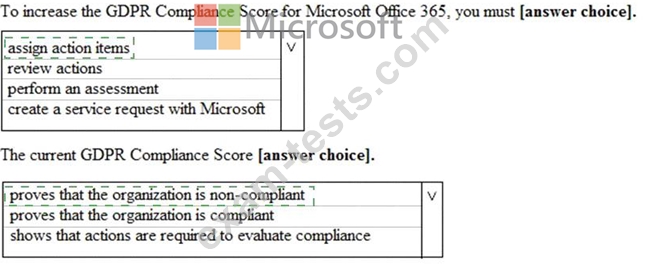
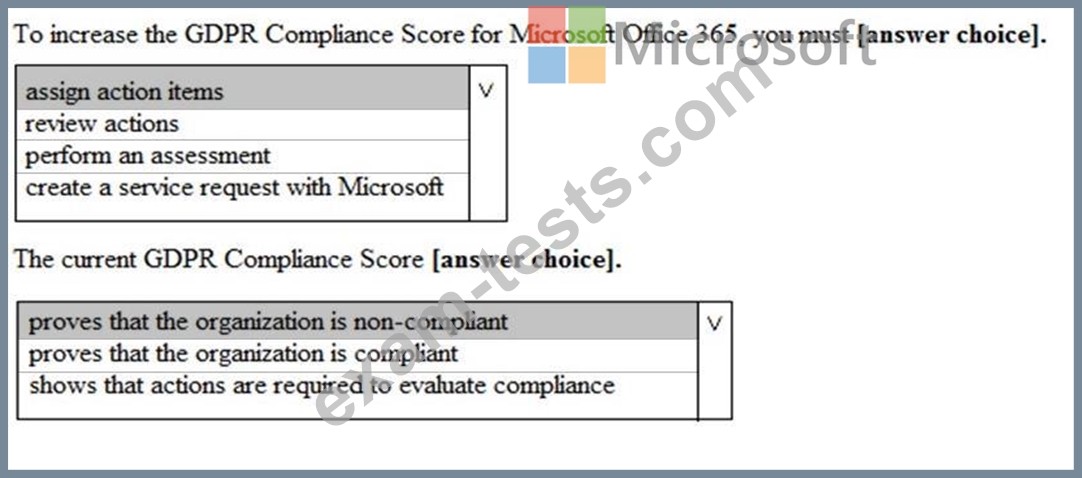
You view Compliance Manager as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
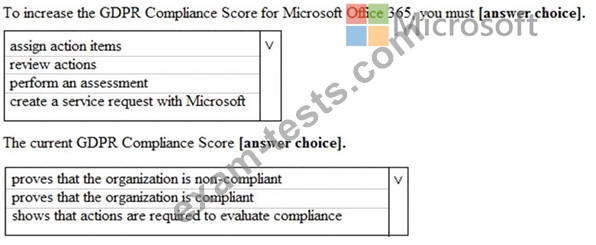

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Question 147
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.
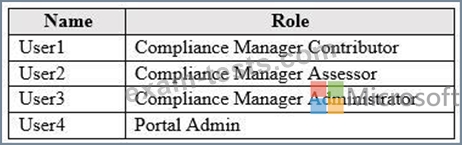
You discover that all the users in the subscription can access Compliance Manager reports.
The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend removing User1 from the Compliance Manager Contributor role.
Does that meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.

You discover that all the users in the subscription can access Compliance Manager reports.
The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend removing User1 from the Compliance Manager Contributor role.
Does that meet the goal?
Question 148
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
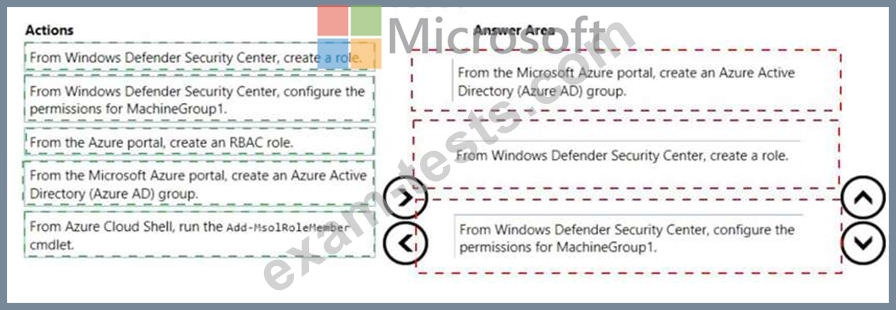
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
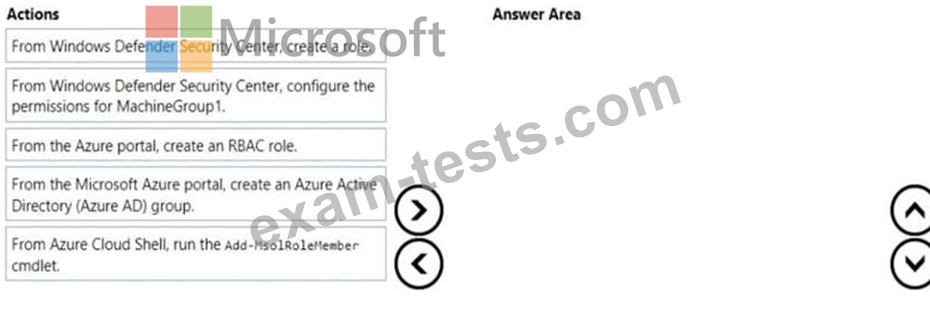
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 149
You need to ensure that unmanaged mobile devices are quarantined when the devices attempt to connect to Exchange Online.
To complete this task, sign in to the Microsoft 365 portal.
To complete this task, sign in to the Microsoft 365 portal.
Question 150
You create a data loss prevention (DLP) policy as shown in the following shown:
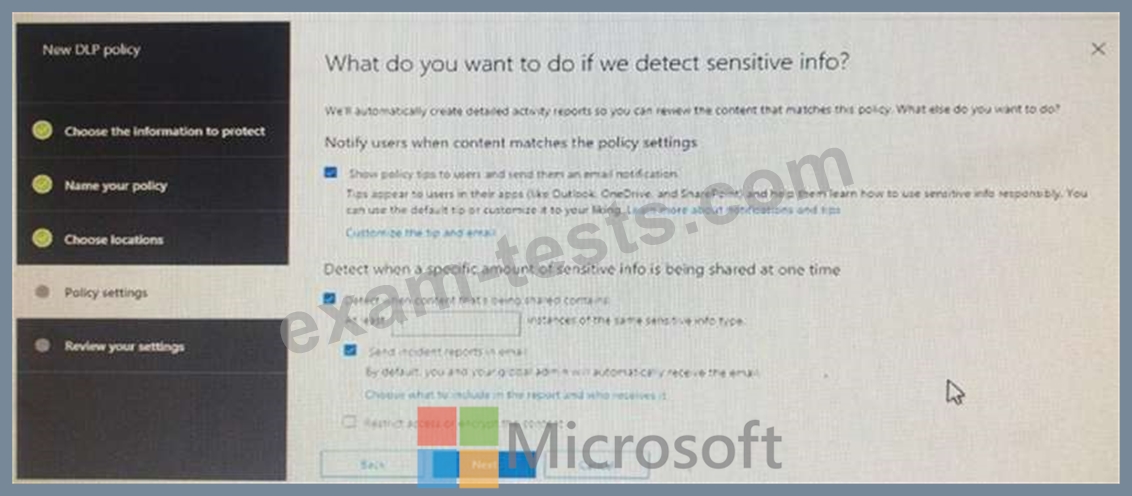
What is the effect of the policy when a user attempts to send an email messages that contains sensitive information?

What is the effect of the policy when a user attempts to send an email messages that contains sensitive information?
Premium Bundle
Newest MS-500 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing MS-500 Exam! BraindumpsPass.com now offer the updated MS-500 exam dumps, the BraindumpsPass.com MS-500 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com MS-500 pdf dumps with Exam Engine here: