Question 176
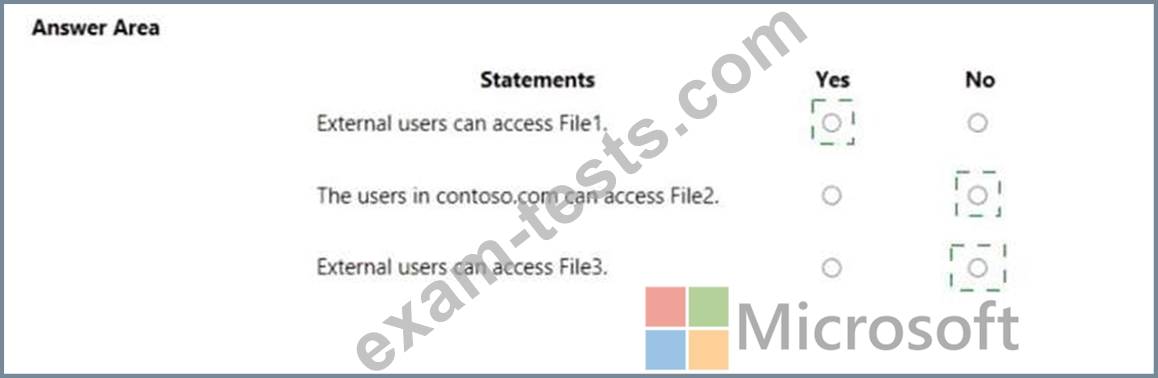
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. OneDrive stores files that are shared with external users. The files are configured as shown in the following table.
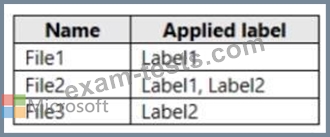
You create a data loss prevention (DLP) policy that applies to the content stored in OneDrive accounts. The policy contains the following three rules:
* Rulel:
* Conditions: Label 1, Detect content that's shared with people outside my organization
* Actions: Restrict access to the content for external users
* User notifications: Notify the user who last modified the content
* User overrides: On
* Priority: 0
* Rule2:
* Conditions: Label 1 or Label2
* Actions: Restrict access to the content
* Priority: 1
* Rule3:
* Conditions: Label2, Detect content that's shared with people outside my organization
* Actions: Restrict access to the content for external users
* User notifications: Notify the user who last modified the content
* User overrides: On
* Priority: 2
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.


You create a data loss prevention (DLP) policy that applies to the content stored in OneDrive accounts. The policy contains the following three rules:
* Rulel:
* Conditions: Label 1, Detect content that's shared with people outside my organization
* Actions: Restrict access to the content for external users
* User notifications: Notify the user who last modified the content
* User overrides: On
* Priority: 0
* Rule2:
* Conditions: Label 1 or Label2
* Actions: Restrict access to the content
* Priority: 1
* Rule3:
* Conditions: Label2, Detect content that's shared with people outside my organization
* Actions: Restrict access to the content for external users
* User notifications: Notify the user who last modified the content
* User overrides: On
* Priority: 2
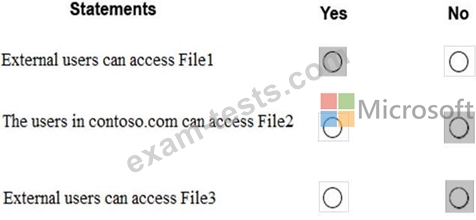
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Question 177
You company has a Microsoft 36S E5 subscription and a hybrid Azure active Directory named contoso.com.
Contoso.com includes the following users:
You configure Password protection for Contoso.com as shown in the following exhibit.
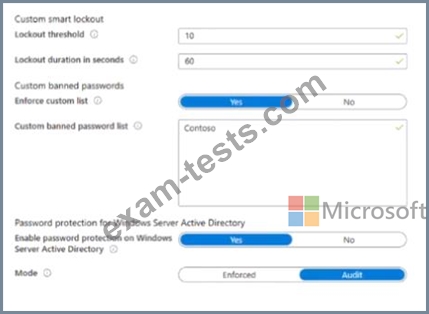

Contoso.com includes the following users:
You configure Password protection for Contoso.com as shown in the following exhibit.


Question 178
どの役割をUser1に割り当てますか?
Question 179
Several users in your Microsoft 365 subscription report that they received an email message without the attachment.
You need to review the attachments that were removed from the messages.
Which two tools can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to review the attachments that were removed from the messages.
Which two tools can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Question 180
You have a Microsoft 365 E5 subscription.
From Microsoft Azure Active Directory (Azure AD), you create a security group named Group1. You add 10 users to Group1.
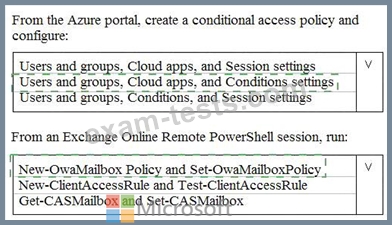
You need to apply app enforced restrictions to the members of Group1 when they connect to Microsoft Exchange Online from non-compliant devices, regardless of their location.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
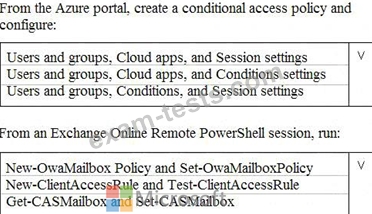
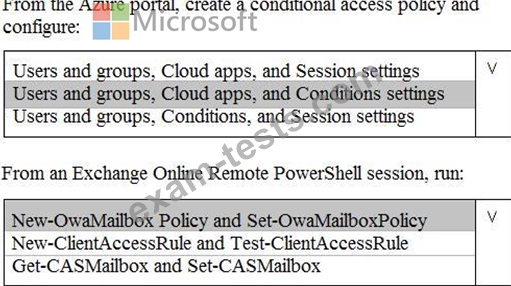
From Microsoft Azure Active Directory (Azure AD), you create a security group named Group1. You add 10 users to Group1.
You need to apply app enforced restrictions to the members of Group1 when they connect to Microsoft Exchange Online from non-compliant devices, regardless of their location.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.