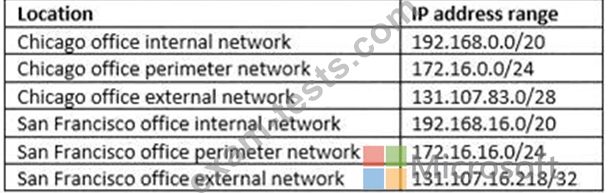
Question 11
Which IP address space should you include in the MFA configuration?
Question 12
You have a Microsoft 365 subscription.
You enable auditing for the subscription.
You plan to provide a user named Auditor with the ability to review audit logs.
You add Auditor to the Global administrator role group.
Several days later, you discover that Auditor disabled auditing.
You remove Auditor from the Global administrator role group and enable auditing.
Be prevented from disabling auditing
Use the principle of least privilege
Be able to review the audit log
To which role group should you add Auditor?
You enable auditing for the subscription.
You plan to provide a user named Auditor with the ability to review audit logs.
You add Auditor to the Global administrator role group.
Several days later, you discover that Auditor disabled auditing.
You remove Auditor from the Global administrator role group and enable auditing.
Be prevented from disabling auditing
Use the principle of least privilege
Be able to review the audit log
To which role group should you add Auditor?
Question 13
You have a Microsoft 365 E5 subscription.
Users and device objects are added and removed daily. Users in the sales department frequently change their device.
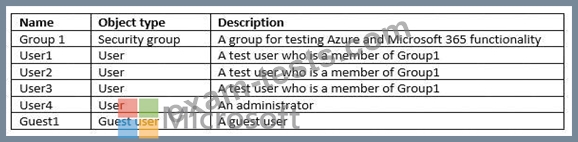
You need to create three following groups:
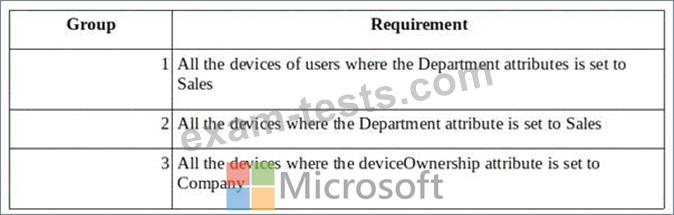
The solution must minimize administrative effort.
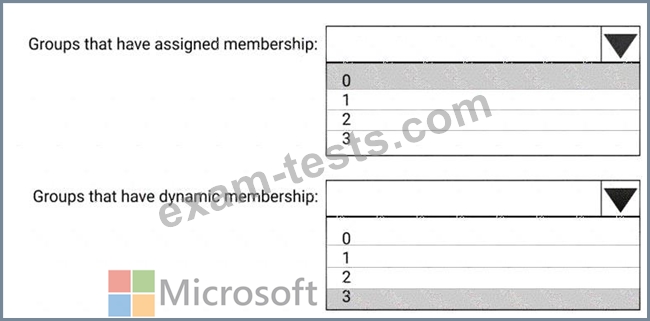
What is the minimum number of groups you should create for each type of membership? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
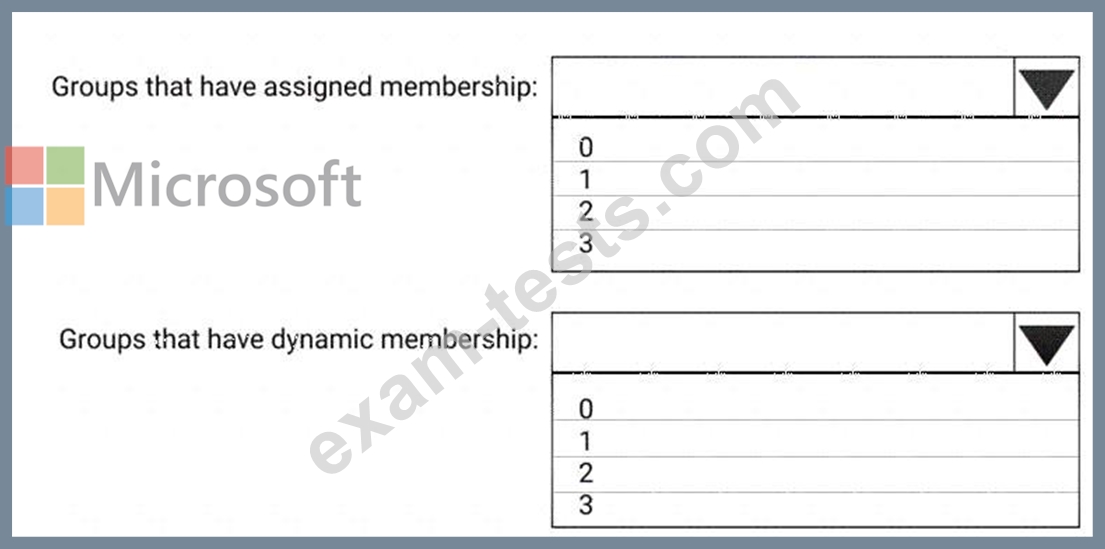
Users and device objects are added and removed daily. Users in the sales department frequently change their device.
You need to create three following groups:

The solution must minimize administrative effort.
What is the minimum number of groups you should create for each type of membership? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 14
Your company has 500 computers.
You plan to protect the computers by using Windows Defender Advanced Threat Protection (Windows Defender ATP). Twenty of the computers belong to company executives.
You need to recommend a remediation solution that meets the following requirements:
Windows Defender ATP administrators must manually approve all remediation for the executives Remediation must occur automatically for all other users What should you recommend doing from Windows Defender Security Center?
You plan to protect the computers by using Windows Defender Advanced Threat Protection (Windows Defender ATP). Twenty of the computers belong to company executives.
You need to recommend a remediation solution that meets the following requirements:
Windows Defender ATP administrators must manually approve all remediation for the executives Remediation must occur automatically for all other users What should you recommend doing from Windows Defender Security Center?
Question 15
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.

You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings:
* Assignments: Include Group1, Exclude Group2
* Conditions: Sign in risk of Low and above
* Access: Allow access, Require password multi-factor authentication
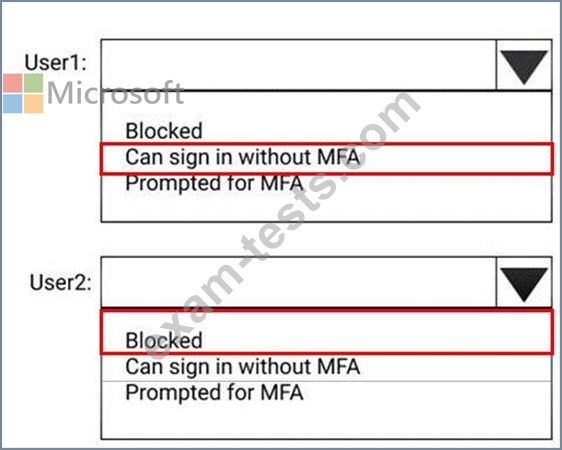
You need to identify how the policy affects User1 and User2.
What occurs when each user signs in from an anonymous IP address? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
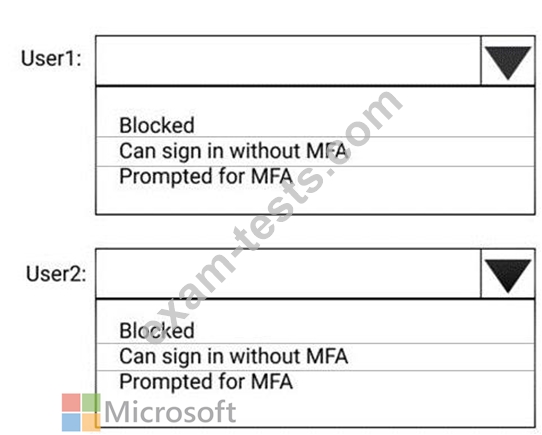

You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings:
* Assignments: Include Group1, Exclude Group2
* Conditions: Sign in risk of Low and above
* Access: Allow access, Require password multi-factor authentication
You need to identify how the policy affects User1 and User2.
What occurs when each user signs in from an anonymous IP address? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.