Question 66
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization.
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft Office 365 Attack simulator to model a spear-phishing attack that targets the Research group members.
The email address that you intend to spoof belongs to the Executive group members.
What should you do first?
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft Office 365 Attack simulator to model a spear-phishing attack that targets the Research group members.
The email address that you intend to spoof belongs to the Executive group members.
What should you do first?
Question 67
Your company has a Microsoft 365 subscription that contains the usersshown in the following table.
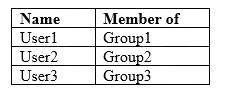
The company implements Windows Defender Advanced Threat Protection (Windows Defender ATP).
Windows Defender ATP includes the roles shown in the following table:
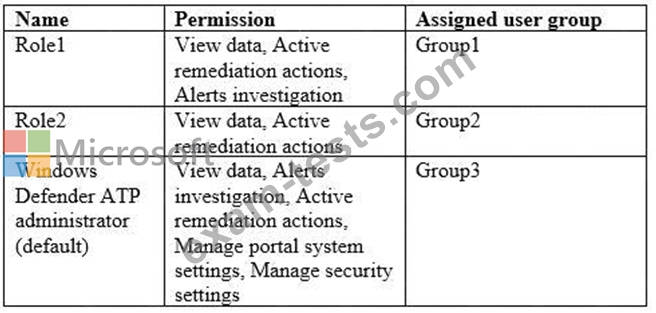
Windows Defender ATP contains the machine groups shown inthe following table:

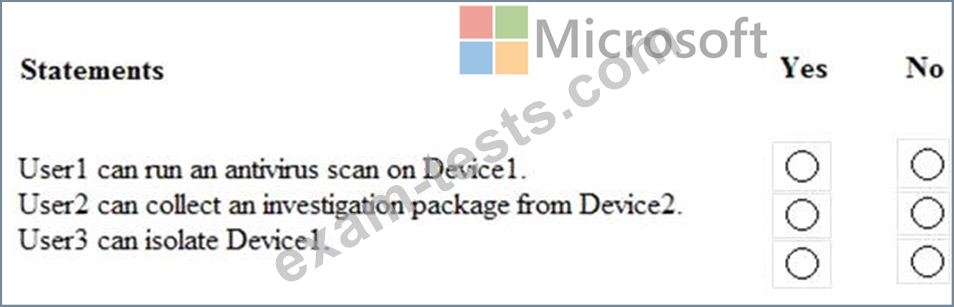
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.

The company implements Windows Defender Advanced Threat Protection (Windows Defender ATP).
Windows Defender ATP includes the roles shown in the following table:

Windows Defender ATP contains the machine groups shown inthe following table:

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.

Question 68
You have a Microsoft 365 subscription that contains a user named User1.
You plan to use Compliance Manager.
You need to ensure that User1 can assign Compliance Manager roles to users. The solution must use the principle of least privilege.
Which role should you assign to User1?
You plan to use Compliance Manager.
You need to ensure that User1 can assign Compliance Manager roles to users. The solution must use the principle of least privilege.
Which role should you assign to User1?
Question 69
You have a Microsoft 365 subscription that uses a default domain name of contoso.com.
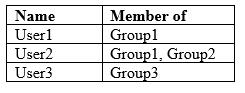
Microsoft Azure Active Directory (Azure AD) contains the users shown in the following table.
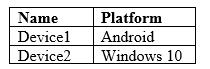
Microsoft Intune has two devices enrolled as shown in the following table:
Both devices have three apps named App1, App2, and App3 installed.
You create an app protection policy named ProtectionPolicy1 that has the following settings:
* Protected apps: App1
* Exempt apps: App2
* Windows Information Protection mode: Block
You apply ProtectionPolicy1 to Group1 and Group3. You exclude Group2 from ProtectionPolicy1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Microsoft Azure Active Directory (Azure AD) contains the users shown in the following table.

Microsoft Intune has two devices enrolled as shown in the following table:

Both devices have three apps named App1, App2, and App3 installed.
You create an app protection policy named ProtectionPolicy1 that has the following settings:
* Protected apps: App1
* Exempt apps: App2
* Windows Information Protection mode: Block
You apply ProtectionPolicy1 to Group1 and Group3. You exclude Group2 from ProtectionPolicy1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Question 70
You need to create a policy that identifies content in Microsoft OneDrive that contains credit card numbers.
To complete this task, sign in to the Microsoft 365 portal.
To complete this task, sign in to the Microsoft 365 portal.





