Question 231
You have a Microsoft 365 E5 subscription that contains a user named User1.
The Azure Active Directory (Azure AD) Identity Protection risky users report identities User1.
For User1, you select Confirm user compromised.
User1 can still sign in.
You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the user risk policy to block access when the user risk level is high.
Does this meet the goal?
The Azure Active Directory (Azure AD) Identity Protection risky users report identities User1.
For User1, you select Confirm user compromised.
User1 can still sign in.
You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the user risk policy to block access when the user risk level is high.
Does this meet the goal?
Question 232
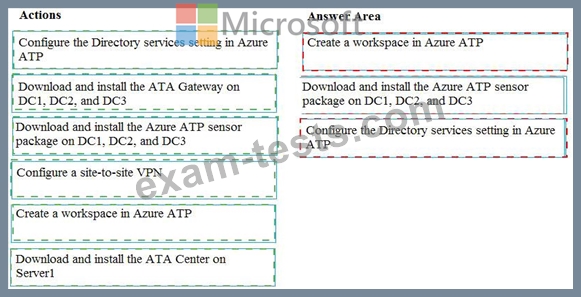
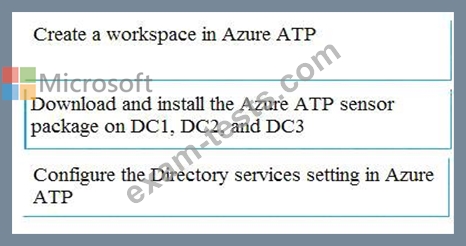
You need to configure threat detection for Active Directory. The solution must meet the security requirements.
Which three actions should youperform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Which three actions should youperform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 233
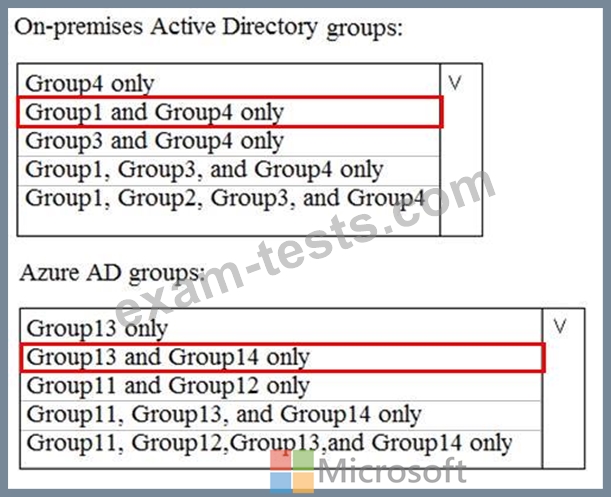
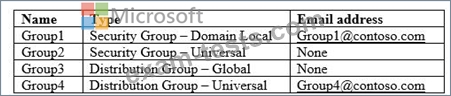
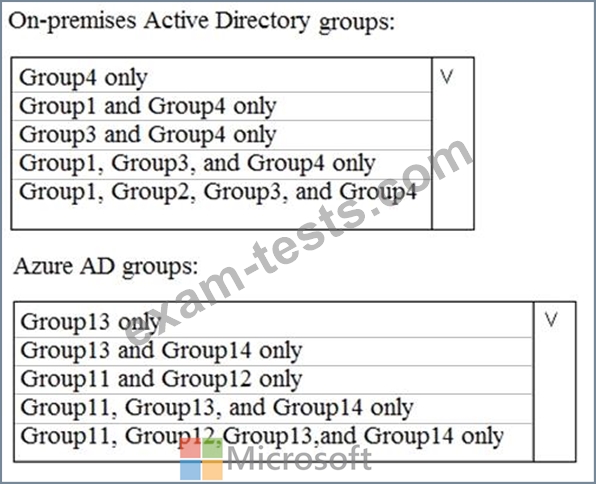
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the groups shown in the following table.
The domain is synced to a Microsoft Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.

You create an Azure Information Protection policy named Policy1.
You need to apply Policy1.
To which groups can you apply Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

The domain is synced to a Microsoft Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.

You create an Azure Information Protection policy named Policy1.
You need to apply Policy1.
To which groups can you apply Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 234
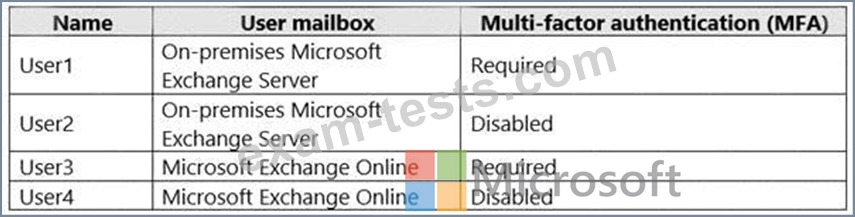
You have a hybrid deployment of Microsoft 365 that contains the users shown in the following table.
You plan to use Microsoft 365 Attack Simulator.
You need to identify the usersagainst which you can use Attack Simulator.
Which users should you identify?

You plan to use Microsoft 365 Attack Simulator.
You need to identify the usersagainst which you can use Attack Simulator.
Which users should you identify?
Question 235
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
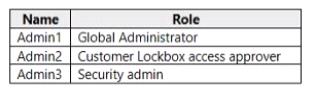
You enable Customer Lockbox.
Which users will be notified when a Microsoft support engineer requests access to the organization?

You enable Customer Lockbox.
Which users will be notified when a Microsoft support engineer requests access to the organization?