Question 31
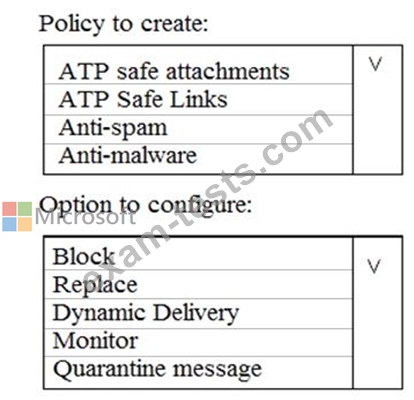
You need to recommend an email malware solution that meets the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 32
You have an Azure Sentinel workspace.
You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.
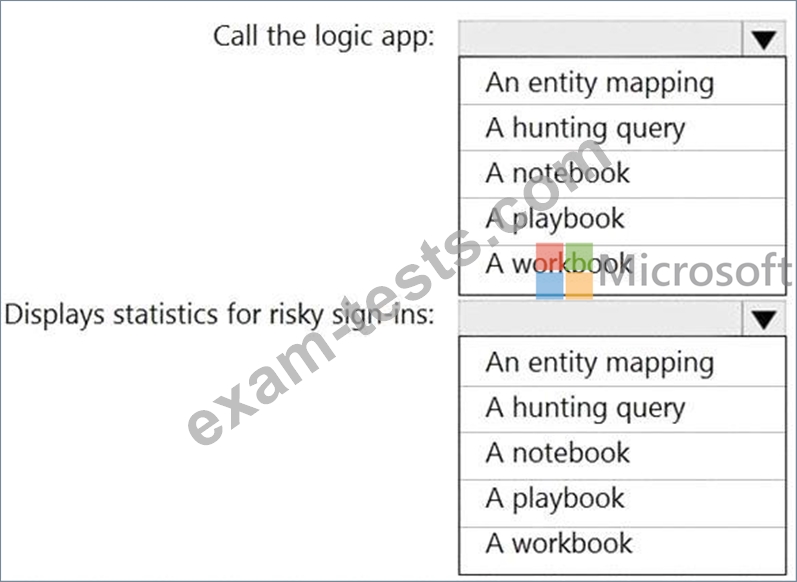
You need to configure the workspace to meet the following requirements:
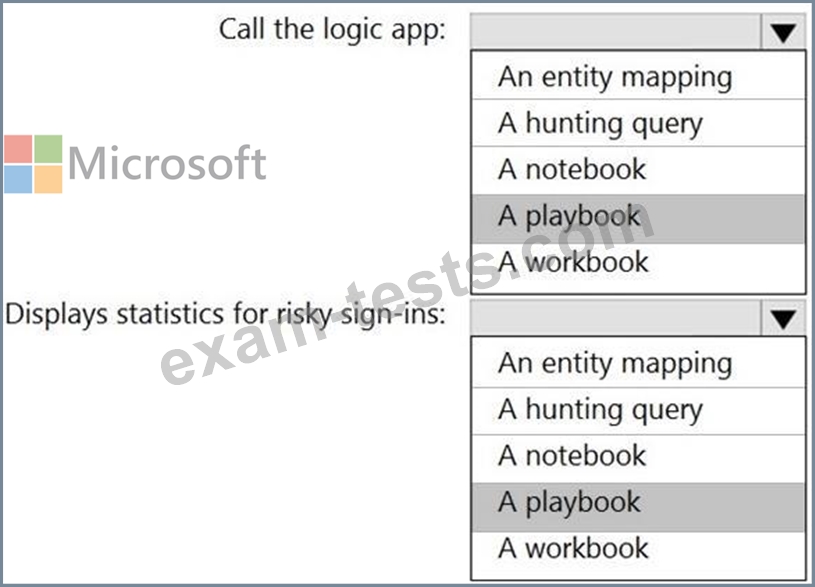
* Call the Azure logic app when an alert is triggered for a risky sign-in.
* To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.
What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.
You need to configure the workspace to meet the following requirements:
* Call the Azure logic app when an alert is triggered for a risky sign-in.
* To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.
What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 33
You have a Microsoft 365 subscription that include three users named User1, User2, and User3.
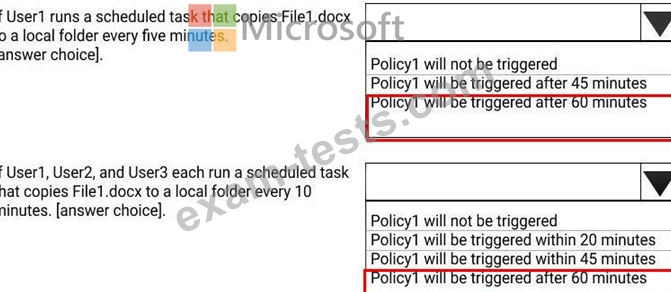
A file named File1.docx is stored in Microsoft OneDrive. An automated process updates File1.docx every minute.
You create an alert policy named Policy1 as shown in the following exhibit.
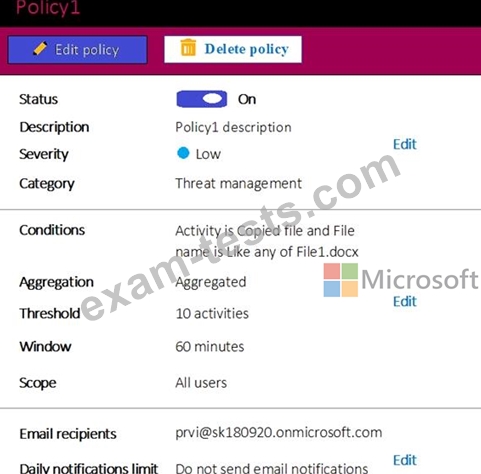
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
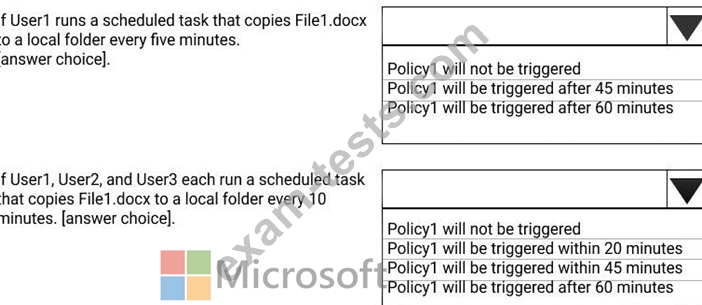
A file named File1.docx is stored in Microsoft OneDrive. An automated process updates File1.docx every minute.
You create an alert policy named Policy1 as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Question 34
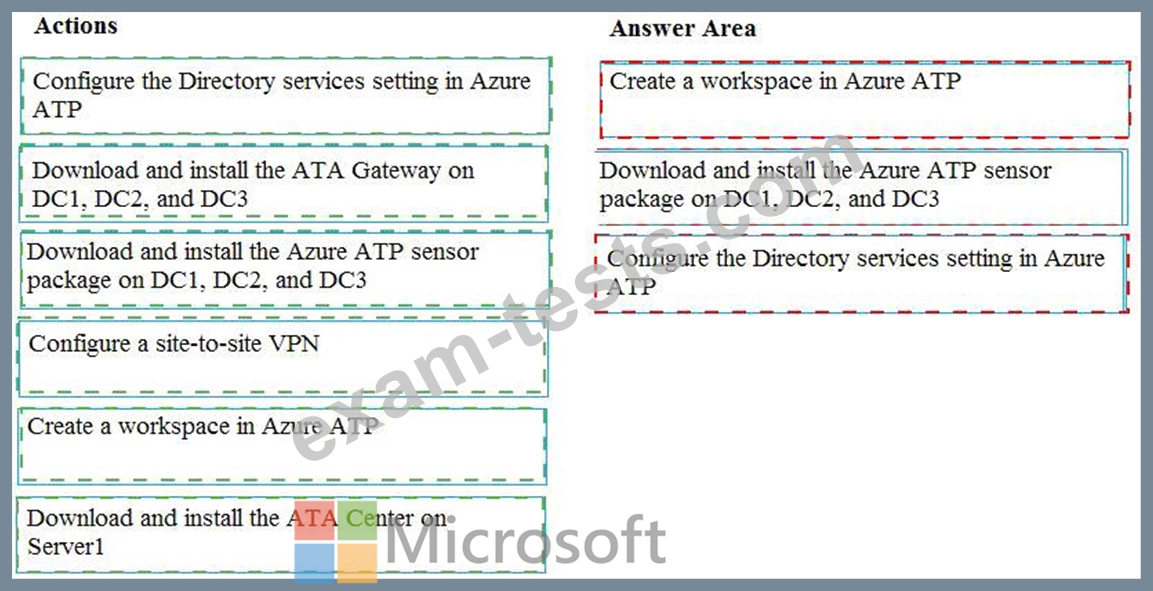
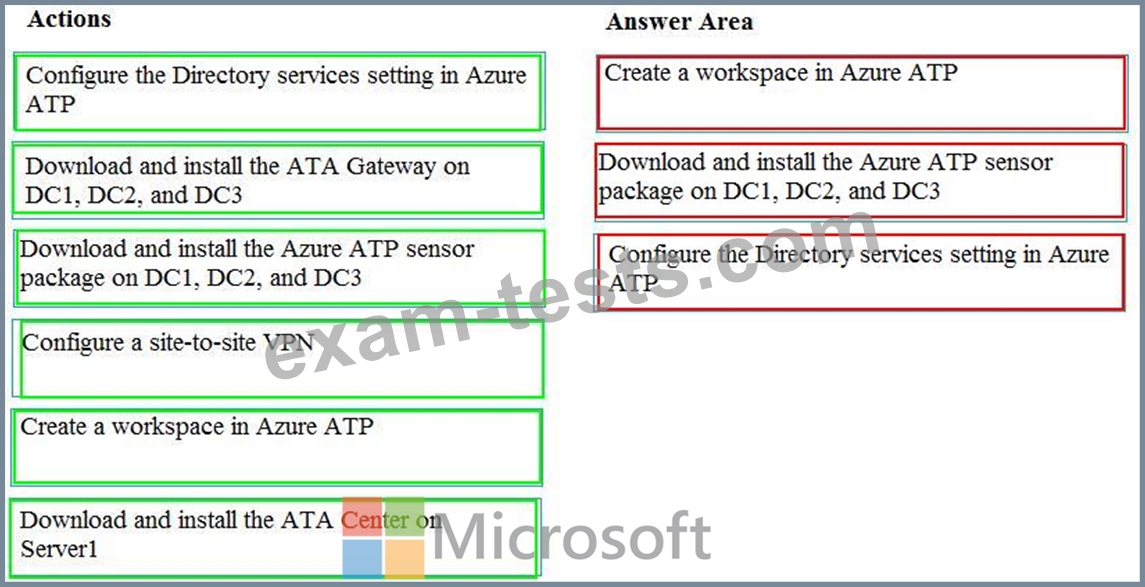
You need to configure threat detection for Active Directory. The solution must meet the security requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
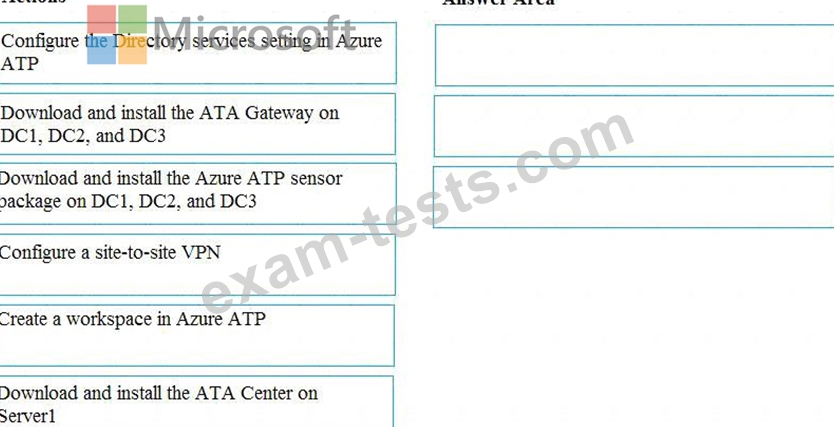
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 35
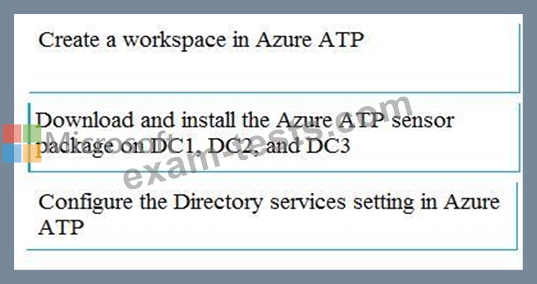
You need to configure threat detection for Active Directory. The solution must meet the security requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
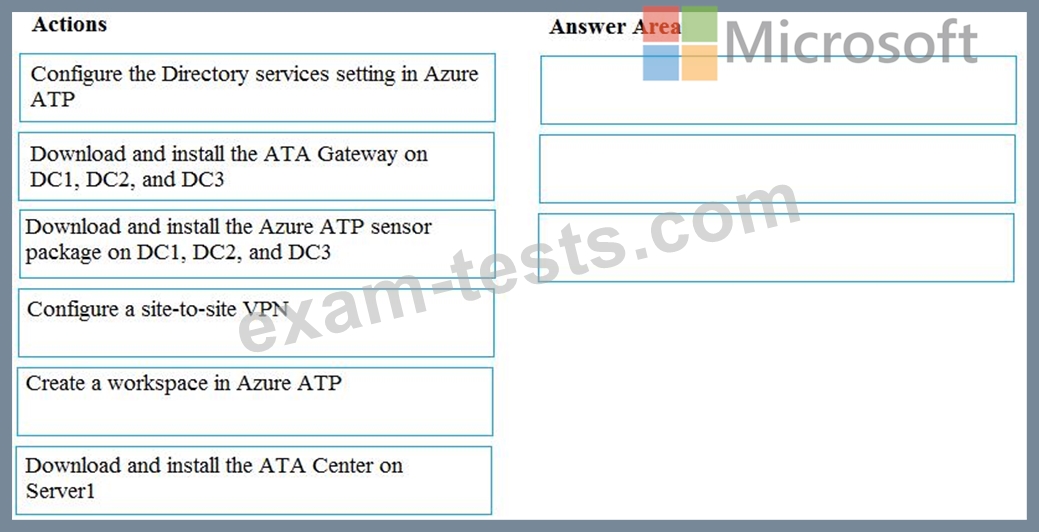
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.