Question 96
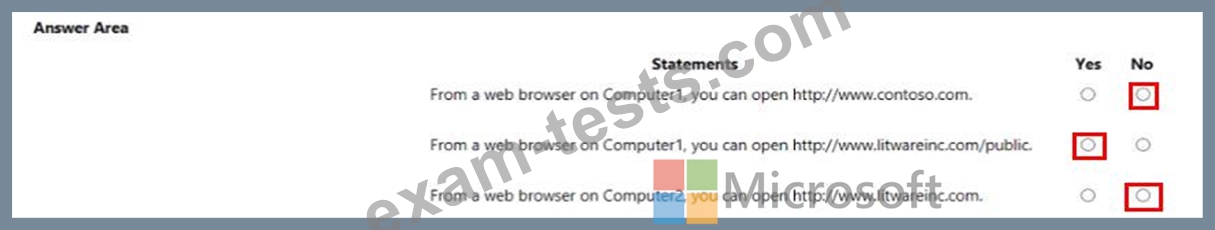
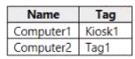
You have a Microsoft Defender for Endpoint deployment that has custom network indicators turned on. Microsoft Defender for Endpoint protects two computers that run Windows 10 as shown in the following table.
Microsoft Defender foe Endpoint has the device groups shown in the following table.
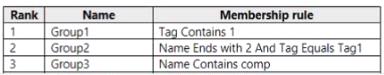

Microsoft Defender foe Endpoint has the device groups shown in the following table.


Question 97
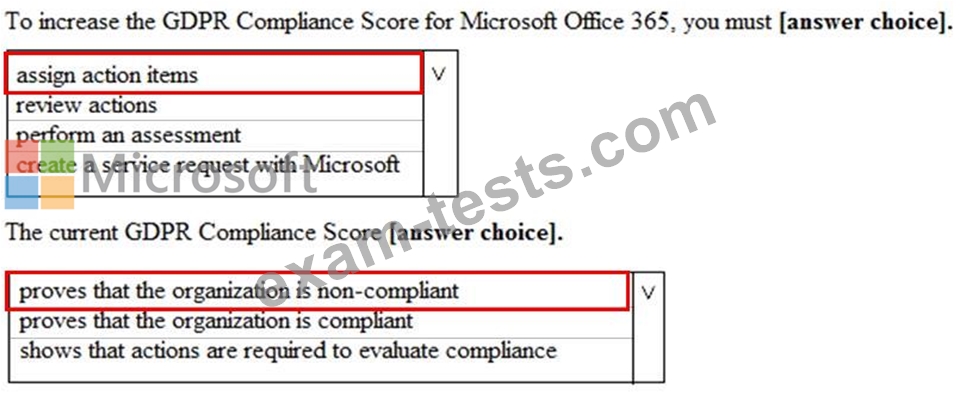
You view Compliance Manager as shown in the following exhibit.
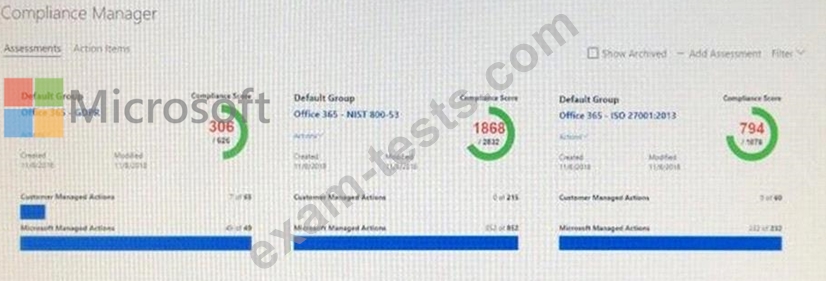
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
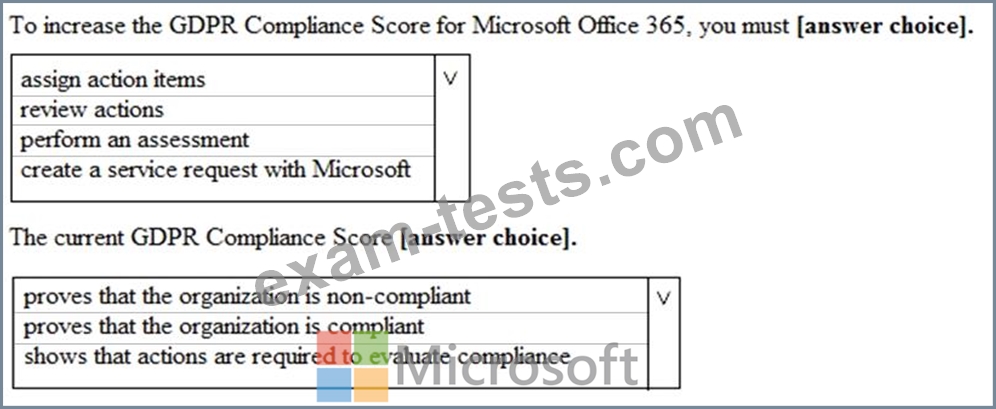

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Question 98
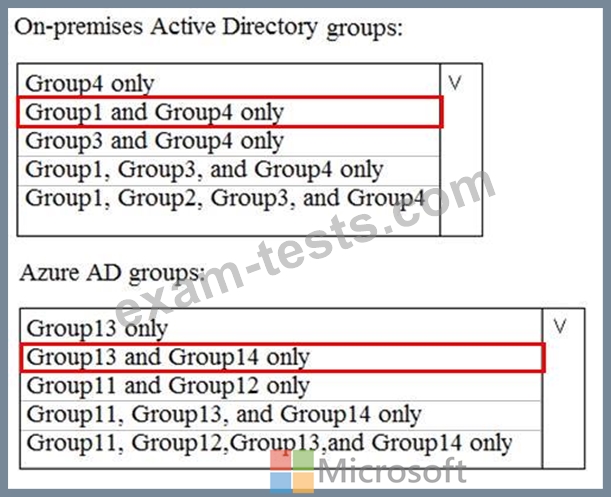
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the groups shown in the following table.
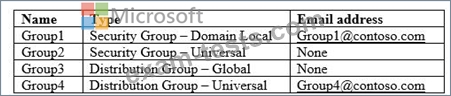
The domain is synced to a Microsoft Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.

You create an Azure Information Protection policy named Policy1.
You need to apply Policy1.
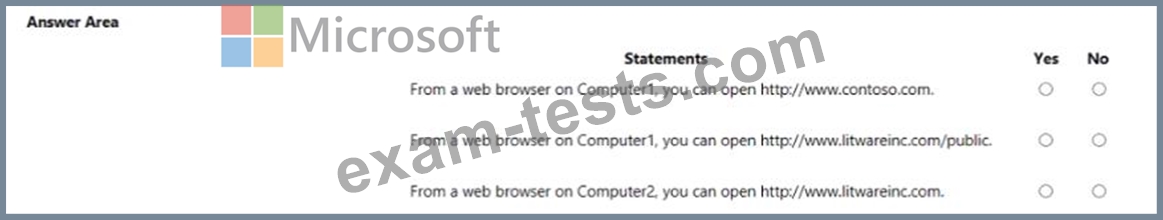
To which groups can you apply Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
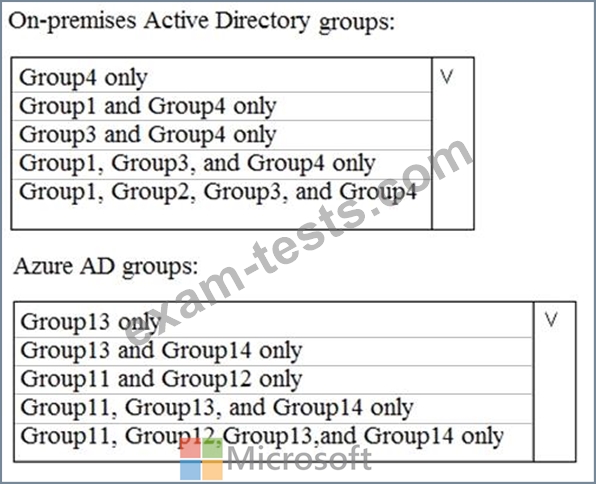

The domain is synced to a Microsoft Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.

You create an Azure Information Protection policy named Policy1.
You need to apply Policy1.
To which groups can you apply Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 99
You have a Microsoft 365 subscription.
You need to recommend a passwordless authentication solution that uses biometric authentication.
What should you include in the recommendation?
You need to recommend a passwordless authentication solution that uses biometric authentication.
What should you include in the recommendation?
Question 100
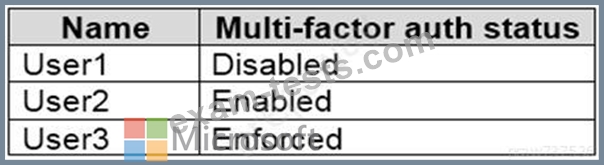
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
You configure the Security Operator role in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.
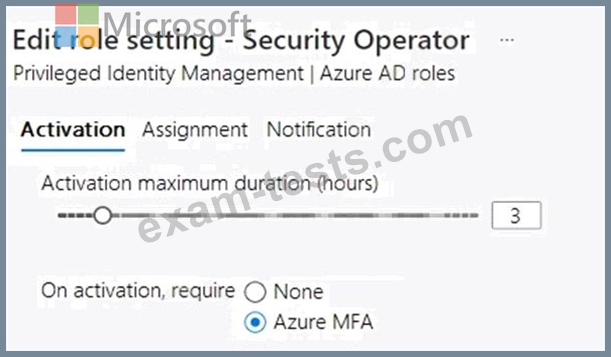
You add assignments to the Security Operator role as shown in the following table.
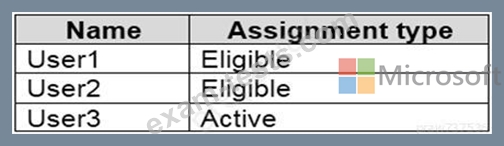
Which users can activate the Security Operator role?

You configure the Security Operator role in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.

You add assignments to the Security Operator role as shown in the following table.

Which users can activate the Security Operator role?