Question 36
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
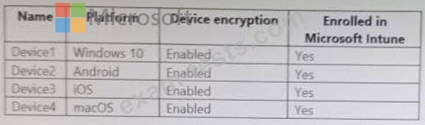
You Plan to use the encryption report in Microsoft Endpoint Manager to view devices that have encryption enabled.
Which devices will be included in the encryption report?

You Plan to use the encryption report in Microsoft Endpoint Manager to view devices that have encryption enabled.
Which devices will be included in the encryption report?
Question 37
You have a Microsoft 365 subscription that contains 1,000 user mailboxes.
An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5.
You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending User5.
Solution: You modify the privacy profile, and then create a Data Subject Request (DSR) case.
Does this meet the goal?
An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5.
You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending User5.
Solution: You modify the privacy profile, and then create a Data Subject Request (DSR) case.
Does this meet the goal?
Question 38
You have a Microsoft 365 E5 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
Azure AD Identity Protection alerts for contoso.com are configured as shown in the following exhibit.
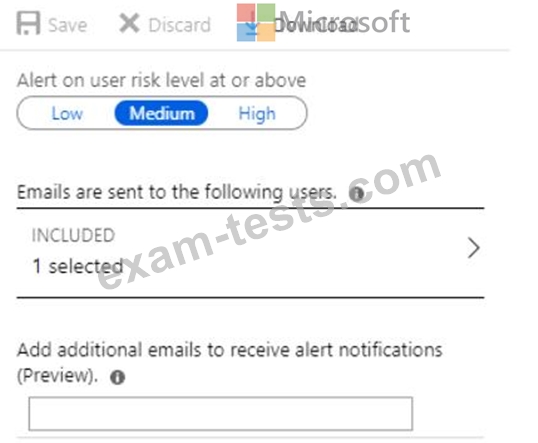
A user named User1 is configured to receive alerts from Azure AD Identity Protection.
You create users in contoso.com as shown in the following table.
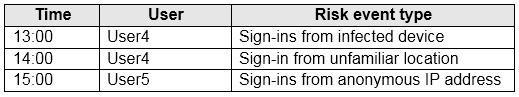
The users perform the sign-ins shown in the following table.
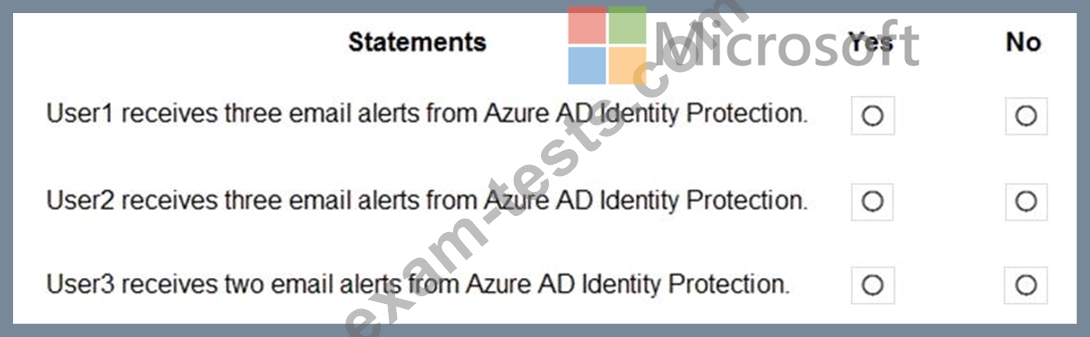
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Azure AD Identity Protection alerts for contoso.com are configured as shown in the following exhibit.

A user named User1 is configured to receive alerts from Azure AD Identity Protection.
You create users in contoso.com as shown in the following table.

The users perform the sign-ins shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Question 39
You have an Azure Sentinel workspace.
You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.
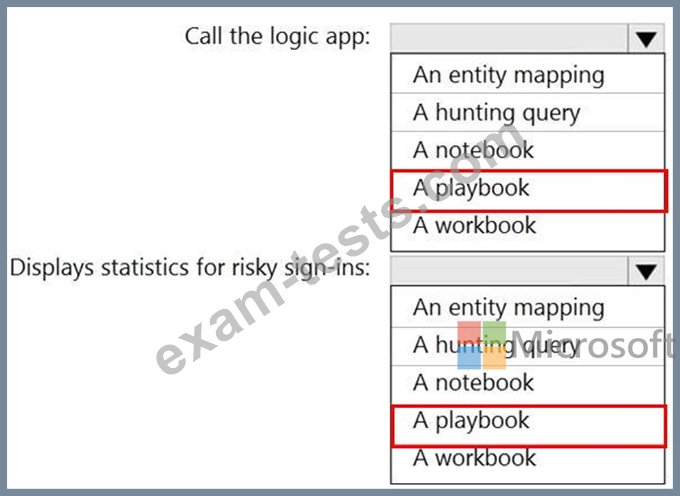
You need to configure the workspace to meet the following requirements:
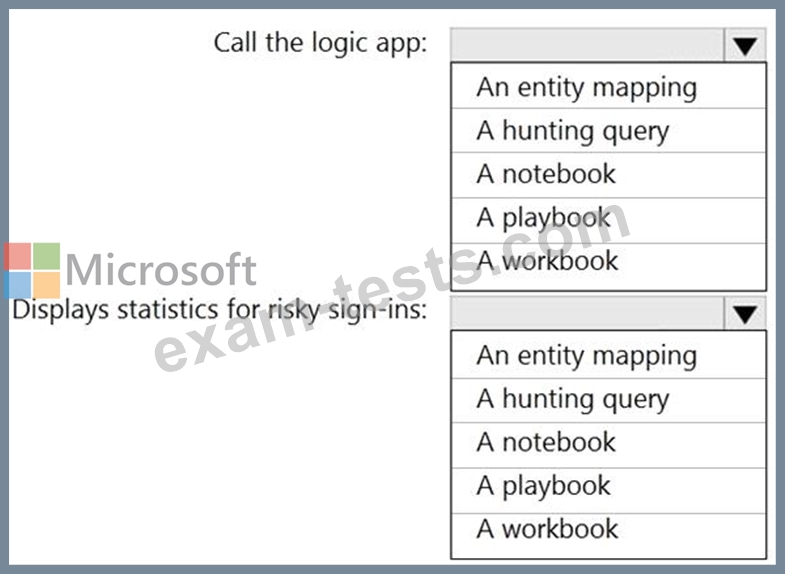
Call the Azure logic app when an alert is triggered for a risky sign-in.
To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.
What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.
You need to configure the workspace to meet the following requirements:
Call the Azure logic app when an alert is triggered for a risky sign-in.
To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.
What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 40
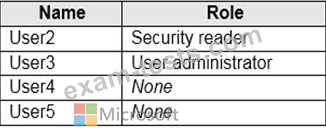
You have a Microsoft 365 E5 subscription that uses insider risk management and contains the users shown in the following table.
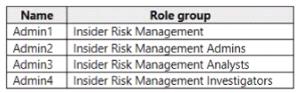
Which users can use Content explorer?

Which users can use Content explorer?