Question 81
Match each tool to its definition.
Instructions: To answer, drag the appropriate tool from the column on the left to its definition on the right.
Each tool may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.

Instructions: To answer, drag the appropriate tool from the column on the left to its definition on the right.
Each tool may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.

Question 82
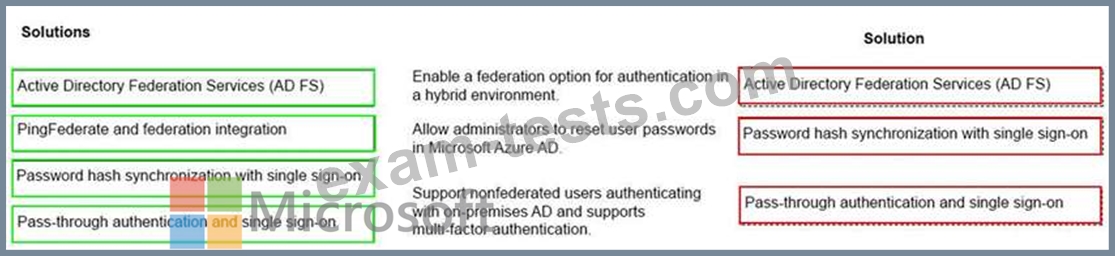
An organization plans to deploy Microsoft 365 in a hybrid scenario.
You need to provide a recommendation based on some common identity and access management scenarios. The solution must minimize costs.
Match each solution to its appropriate scenario. To answer, drag the appropriate solutions from the column on the left to the scenarios on the right. Each solution may be used once, more than once, or not at all. Each correct match is worth one point.
NOTE: Each correct selection is worth one point.

You need to provide a recommendation based on some common identity and access management scenarios. The solution must minimize costs.
Match each solution to its appropriate scenario. To answer, drag the appropriate solutions from the column on the left to the scenarios on the right. Each solution may be used once, more than once, or not at all. Each correct match is worth one point.
NOTE: Each correct selection is worth one point.

Question 83
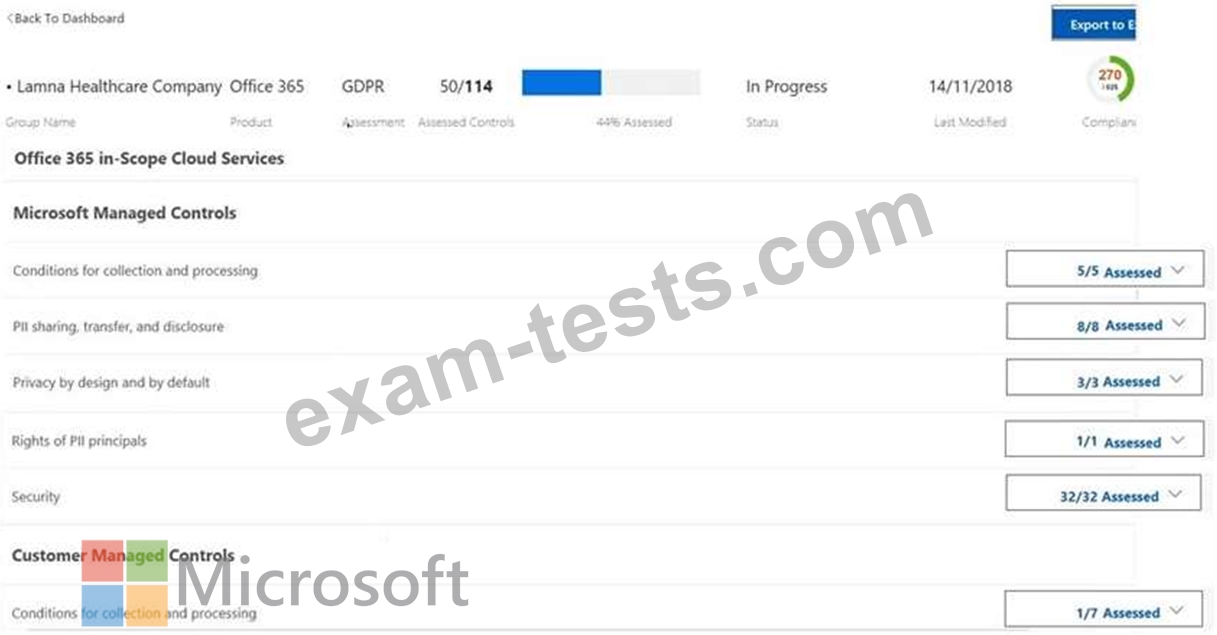
You implement Compliance Manager.
You need to retrieve status information for a control task.
Which two options can you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to retrieve status information for a control task.
Which two options can you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 84
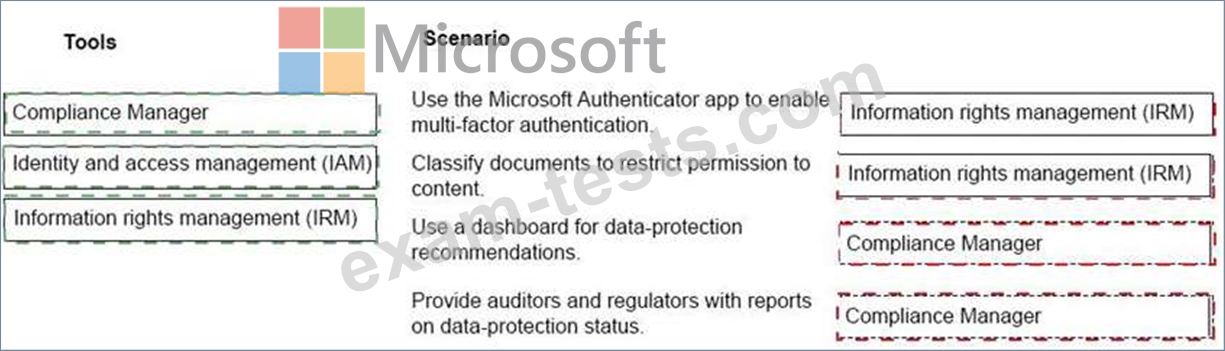
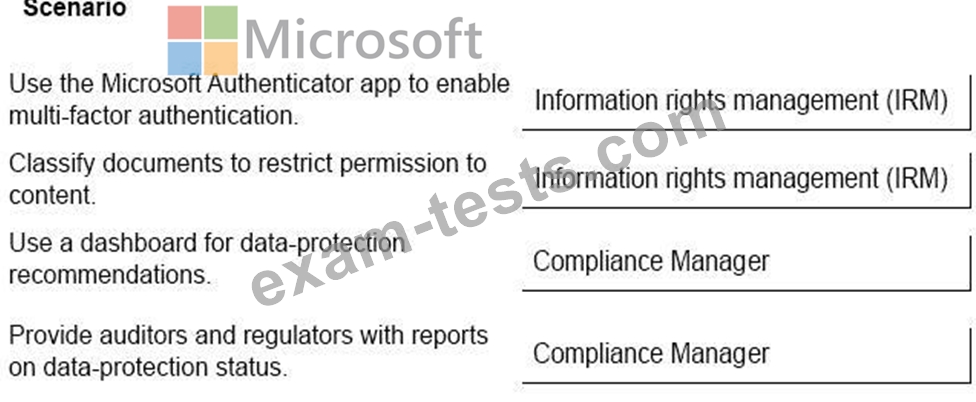
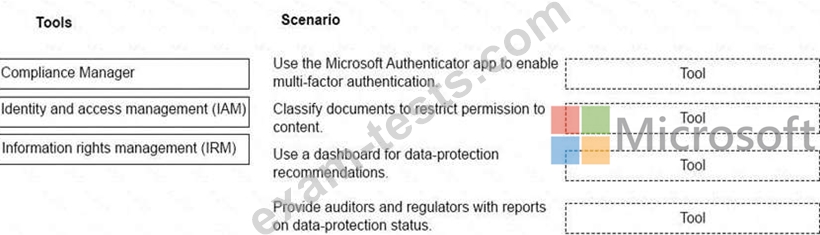
Your company has a Microsoft 365 subscription.
You need to implement security policies to ensure that sensitive data is protected.
Which tools should you use? To answer, drag the appropriate tools to the correct scenarios. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You need to implement security policies to ensure that sensitive data is protected.
Which tools should you use? To answer, drag the appropriate tools to the correct scenarios. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

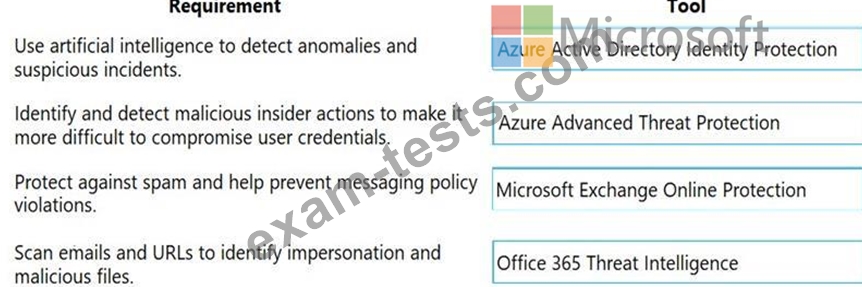
Question 85
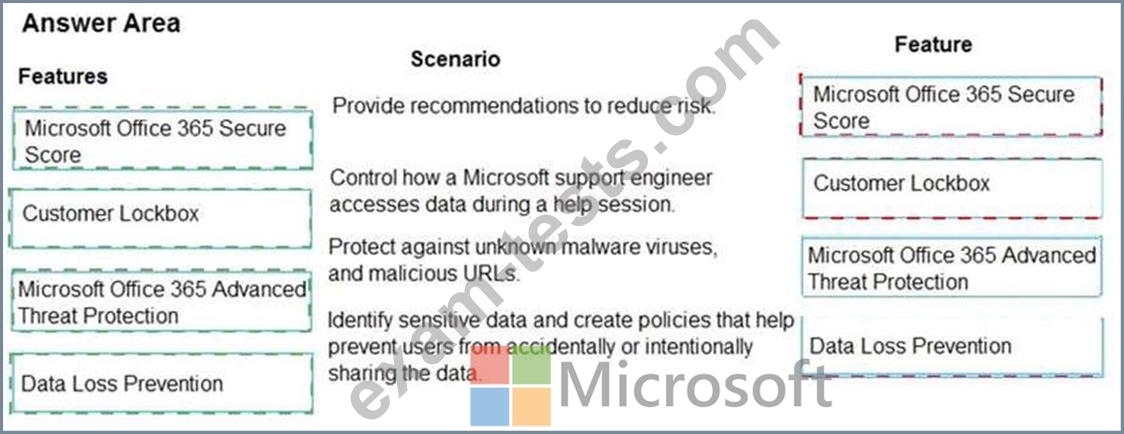
A company purchases Microsoft 365 E5.
You need to determine which security features you should implement.
Which features should you implement? To answer, drag the appropriate features to the correct scenarios. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to determine which security features you should implement.
Which features should you implement? To answer, drag the appropriate features to the correct scenarios. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.