Question 401
A network technician configures a firewall's ACL to allow outgoing traffic for several popular services such
as email and web browsing. However, after the firewall's deployment, users are still unable to retrieve their
emails. Which of the following would BEST resolve this issue?
as email and web browsing. However, after the firewall's deployment, users are still unable to retrieve their
emails. Which of the following would BEST resolve this issue?
Question 402
A document outlining the types of actions allowed on the corporate network would be BEST defined as an:
Question 403
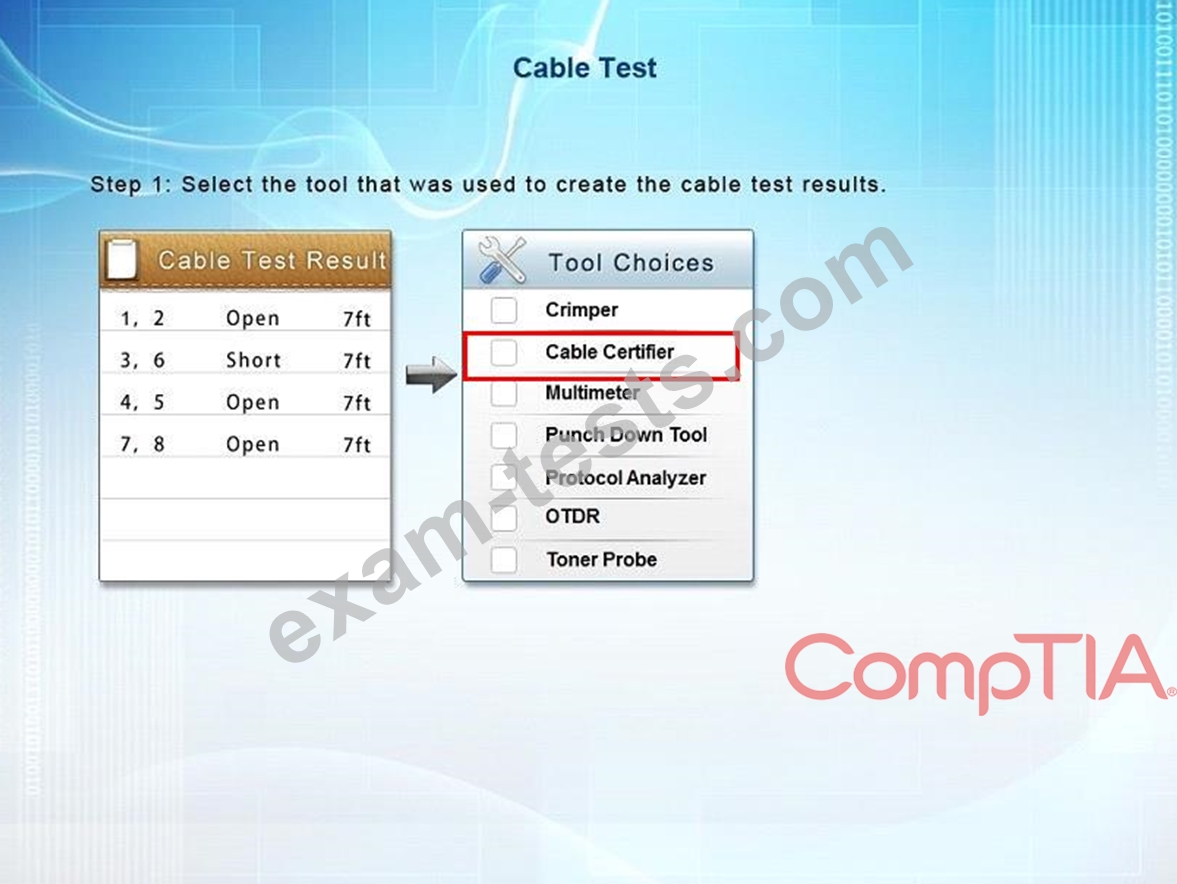
You have been tasked with testing a CAT5e cable. A summary of the test results can be found on the screen.
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the 'Submit Cable Test Analysis' button.
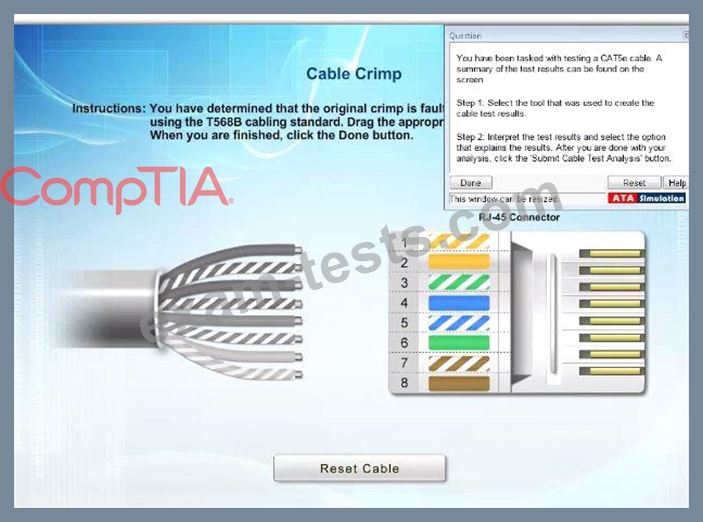
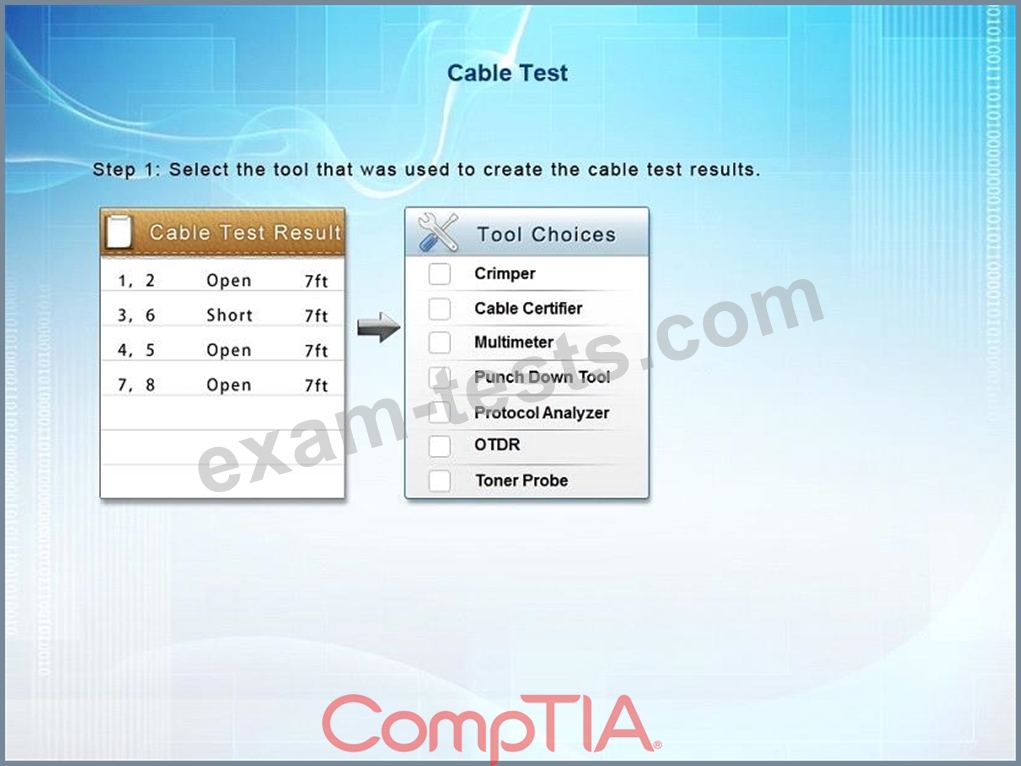
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the 'Submit Cable Test Analysis' button.


Question 404
A user reports a laptop wireless connection is working at the user's desk but not in a recent building addition. A network administrator logs into the wireless controller, searches for the user's MAC address, and receives the following results:
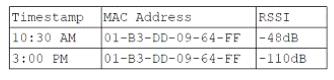
Which of the following describes the reason for the issue?

Which of the following describes the reason for the issue?
Question 405
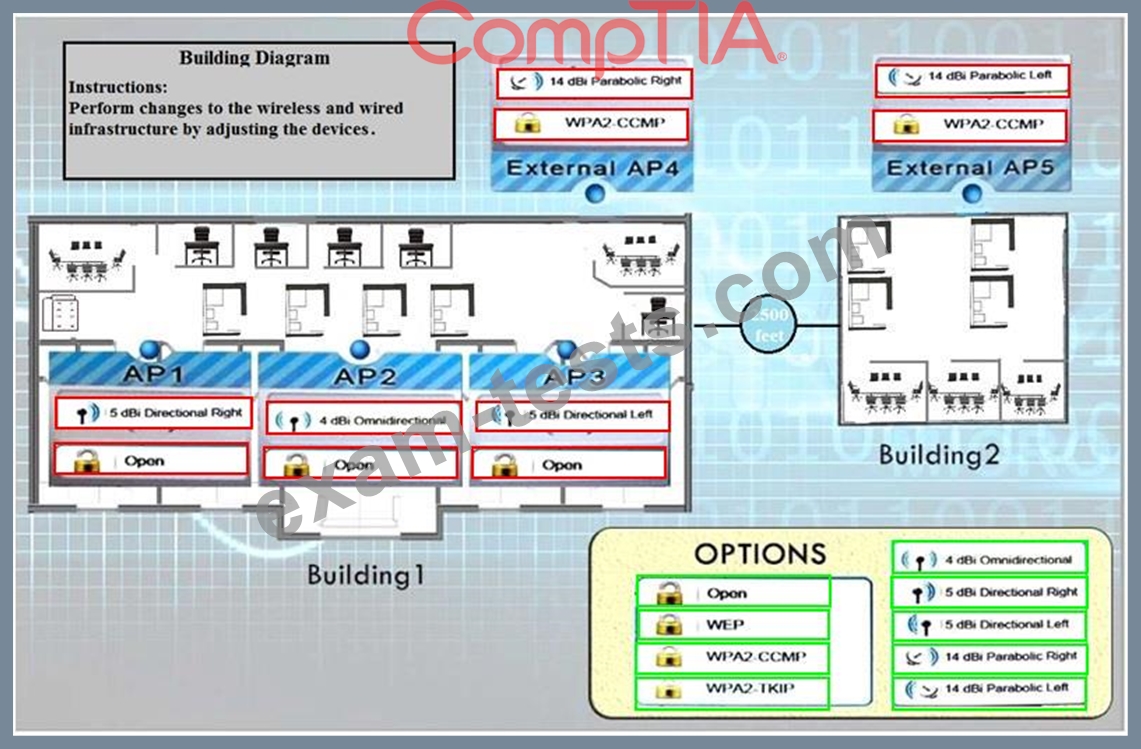
Your company recently purchased a new building down the street from the existing office. For each of the tasks below, select the appropriate antenna type and encryption object for all wireless access point (AP).
1. Create an encrypted wireless connection between the two buildings that BEST controls signal propagation, while maximizing security.
2. Restrict the wireless signal generated by the access points (APs) inside Building 1, so that it minimizes broadcast beyond the building.
3. Maximize wireless coverage inside Building 1.
4. Building 1's internal wireless network is for visitors only and must not require any special configuration on the visitor's device to connect.
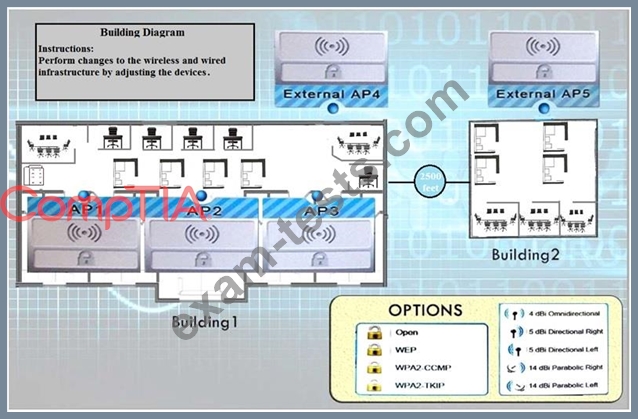
Instructions: When you have completed the simulation, select the Done button to submit.
1. Create an encrypted wireless connection between the two buildings that BEST controls signal propagation, while maximizing security.
2. Restrict the wireless signal generated by the access points (APs) inside Building 1, so that it minimizes broadcast beyond the building.
3. Maximize wireless coverage inside Building 1.
4. Building 1's internal wireless network is for visitors only and must not require any special configuration on the visitor's device to connect.

Instructions: When you have completed the simulation, select the Done button to submit.