Question 6
Where in the Support Portal is the Best Practices guide for vSphere Networking located?
Question 7
An administrator learns that some security settings in a cluster have been changed. The environment is out of compliance with required policies.
Which function should be used to revert any settings that have changed from the defaults and prevent further violations?
Which function should be used to revert any settings that have changed from the defaults and prevent further violations?
Question 8
An administrator is supporting a business critical environment and deploys metro availability to achieve a zero data loss configuration. The two clusters are connected by a 1GbE connection. A new workload is going to be deployed to this cluster. This workload requires a sustained 150MB/S of write throughput and 20MB/s of read throughput.
Which change must be made to deploy the workload successfully on this cluster?
Which change must be made to deploy the workload successfully on this cluster?
Question 9
After finishing foundation on an AHV cluster, a consultant is preparing to plug into the customer network given the following set of requirements:
* All network traffic on trunks is tagged
* Customer is using LACP
* A native VLAN is not in use
Which set of commands should the consultant use to ensure cluster connectivity on customer equipment?
* All network traffic on trunks is tagged
* Customer is using LACP
* A native VLAN is not in use
Which set of commands should the consultant use to ensure cluster connectivity on customer equipment?
Question 10
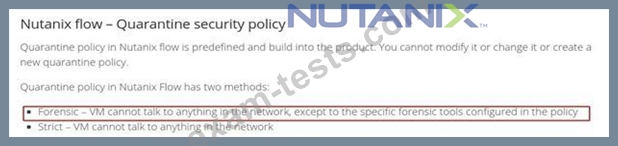
An administrator of a Nutanix Enterprise Cloud has microsegmentation enabled and a firewall VM installed.
The security team notifies the administrator that one of the VMs hosted in the environment has been exhibiting suspect network activity. The administrator wants to isolate the VM from the production network, but must still be able to access it to perform diagnostics.
What should the administrator do to meet the requirement?
The security team notifies the administrator that one of the VMs hosted in the environment has been exhibiting suspect network activity. The administrator wants to isolate the VM from the production network, but must still be able to access it to perform diagnostics.
What should the administrator do to meet the requirement?