Question 56
A host is unable to access volumes as shown in the exhibit.
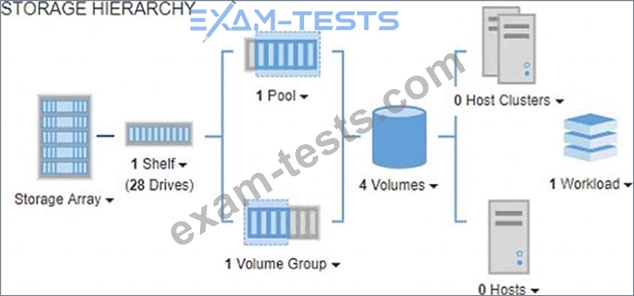
Which statement is correct in this scenario?

Which statement is correct in this scenario?
Question 57
A company is using the Federal Information Processing Standard (FIPS) on all volume groups. However, one volume group failed a security audit.
In this scenario what would cause a volume group to fail the security audit?
In this scenario what would cause a volume group to fail the security audit?
Question 58
Storage system volumes can be built upon what two types of logical structures? (Choose the best answer.)
Question 59
Exhibit:
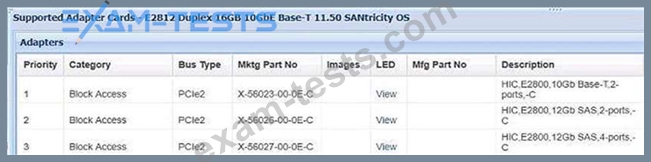
You ordered a NetApp E2812 Duplex 16GB 10GbE Base-T system.
Referring to the exhibit, what is the maximum number of 10GbE Base-T ports available to be used?

You ordered a NetApp E2812 Duplex 16GB 10GbE Base-T system.
Referring to the exhibit, what is the maximum number of 10GbE Base-T ports available to be used?
Question 60
Exhibit:

Referring to the exhibit, what is the total number of ALUA paths from the host to a volume on the EF280?

Referring to the exhibit, what is the total number of ALUA paths from the host to a volume on the EF280?

