Question 11
You want to use a Fabric Pool to store destination SnapMirror data to an external capacity tier. Which tiering policy would be used inthis scenario?
Question 12
You are the administrator of an ONTAP 9.7 cluster. You configured an hourly Snapshot schedule for all volumes. One of your users accidentally deleted an important spreadsheet file on an SMB share. This file must be restored within a minimum amount of time.
Which two actions satisfy this requirement? (Choose two.)
Which two actions satisfy this requirement? (Choose two.)
Question 13
You are upgrading your Data ONTAP cluster from clustered Data ONTAP 8.3 to clustered Data ONTAP 9.1.
Which two actions mustbe performed for the SnapMirror relationships? (Choose two.)
Which two actions mustbe performed for the SnapMirror relationships? (Choose two.)
Question 14
Click the Exhibit button.
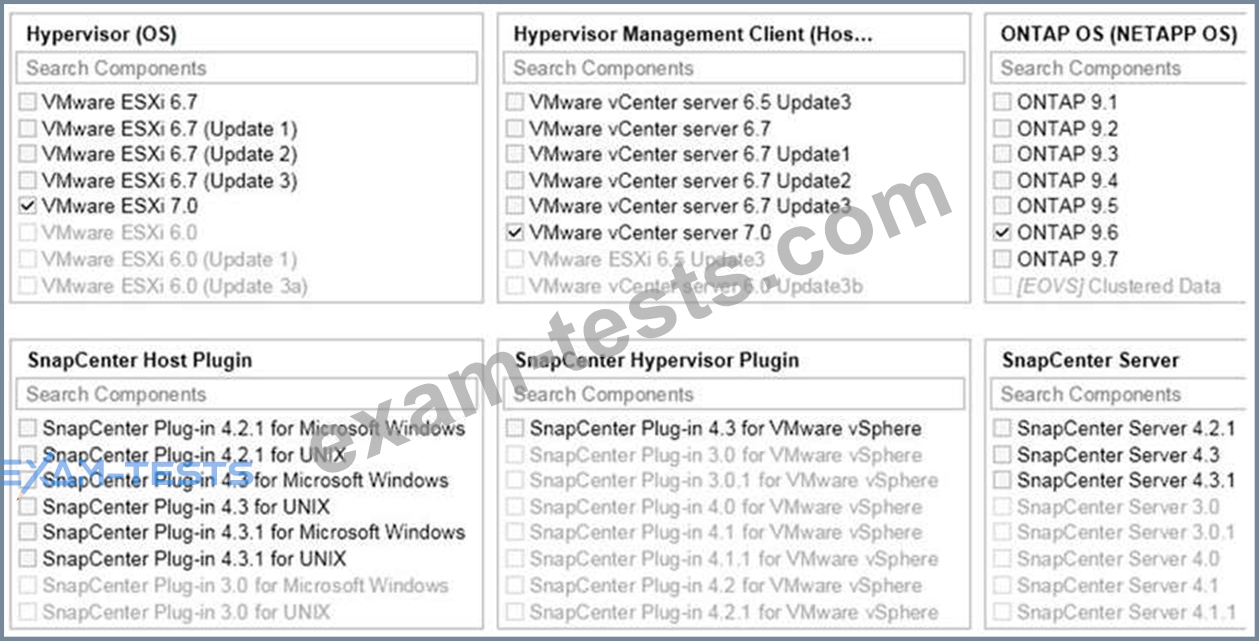
An AFF A700 administrator is told that the VMwareenvironment will be upgraded to vSphere 7 and it will continue to use NFSv3 for their datastores.
Referring to the exhibit, which version of SnapCenter Hypervisor Plugin and SnapCenter Server should they use?

An AFF A700 administrator is told that the VMwareenvironment will be upgraded to vSphere 7 and it will continue to use NFSv3 for their datastores.
Referring to the exhibit, which version of SnapCenter Hypervisor Plugin and SnapCenter Server should they use?
Question 15
Click the Exhibit button.
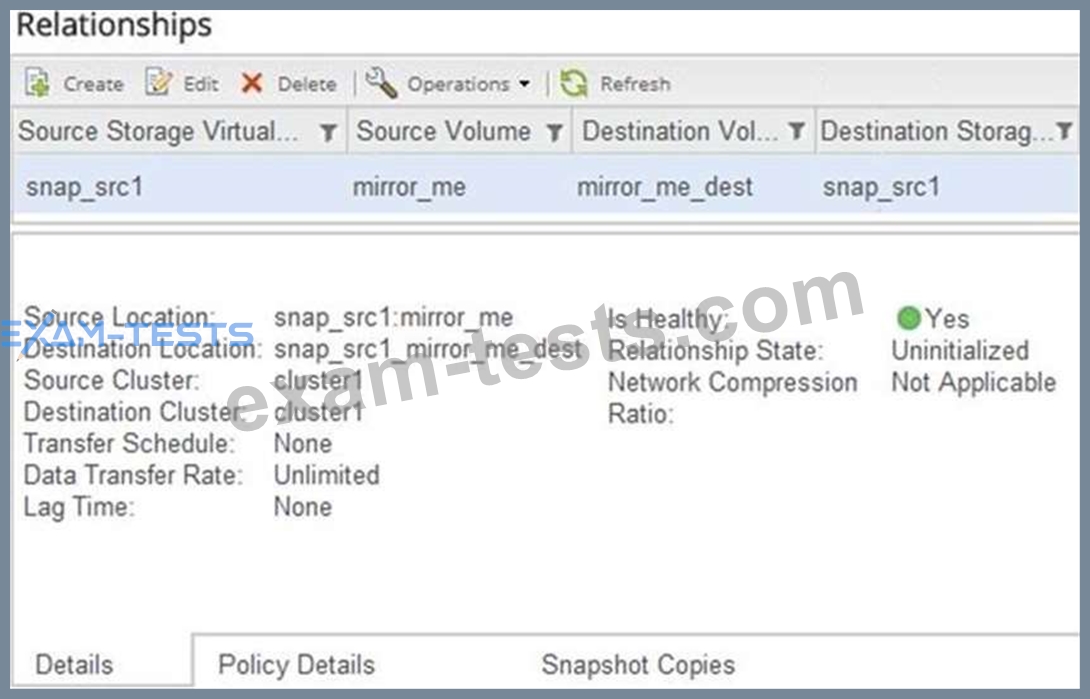
Your customer wants to protect a volume and replicate it to a secondary volume. The customer has tried to configure this relationship using OnCommand System Manager. Upon reviewing this newly configured relationship, you discover that the configuration does not satisfy the customer's stated requirements.
Referring to the exhibit, what should you do to ensure that the volume is protected?

Your customer wants to protect a volume and replicate it to a secondary volume. The customer has tried to configure this relationship using OnCommand System Manager. Upon reviewing this newly configured relationship, you discover that the configuration does not satisfy the customer's stated requirements.
Referring to the exhibit, what should you do to ensure that the volume is protected?

