Question 36
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
Question 37
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
Question 38
Which of these accounts onboarding methods is considered proactive?
Question 39
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
Question 40
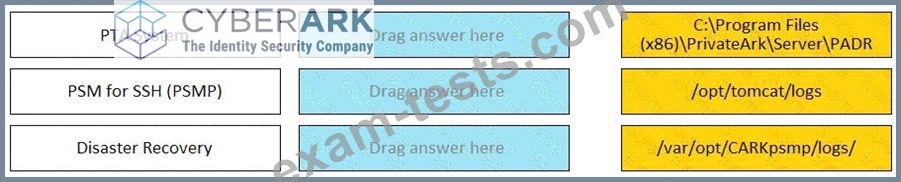
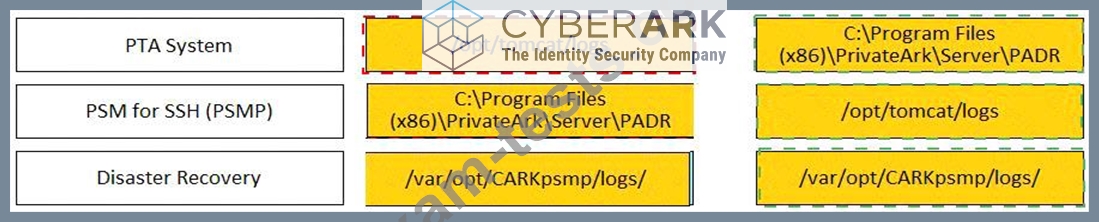
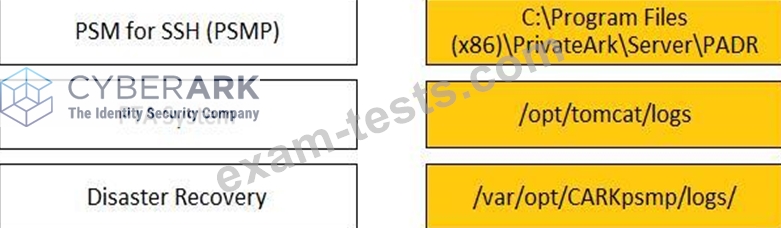
Match each component to its respective Log File location.