Question 21
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault?
Question 22
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
Question 23
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment.
Which security configuration should you recommend?
Which security configuration should you recommend?
Question 24
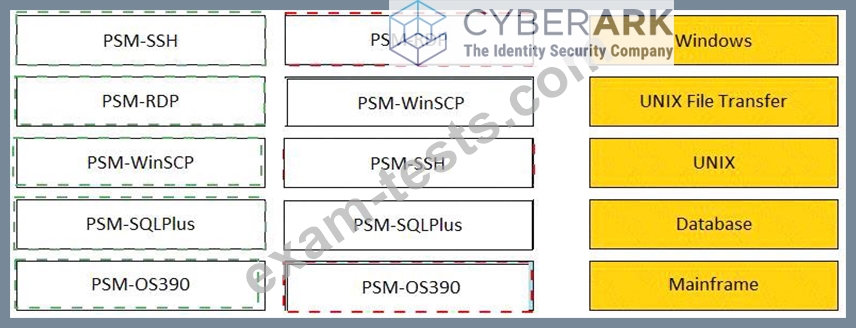
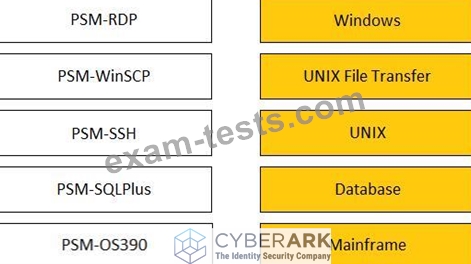
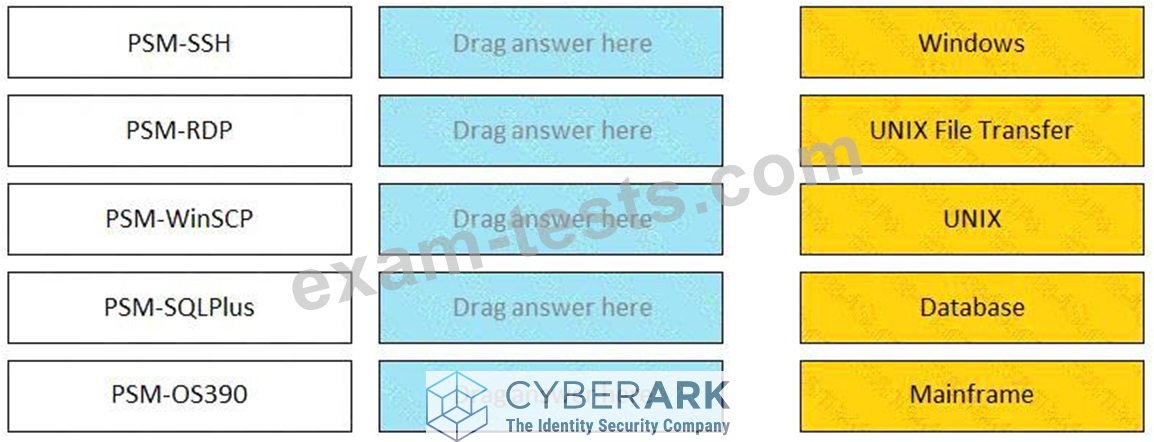
Match the connection component to the corresponding OS/Function.

Question 25
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur