Question 11
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
Question 12
Which characteristic of serverless computing enables developers to quickly deploy application code?
Question 13
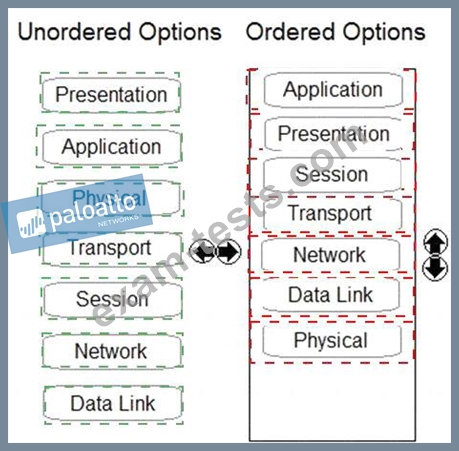
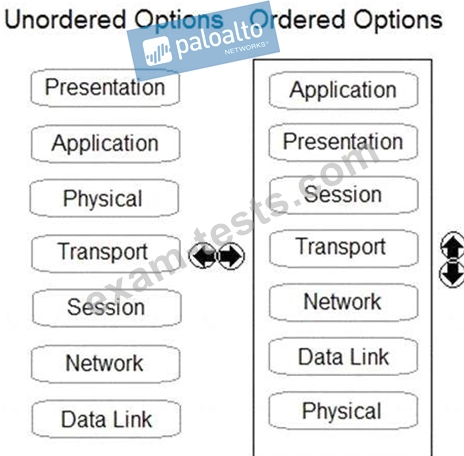
Order the OSI model with Layer7 at the top and Layer1 at the bottom.

Question 14
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
Question 15
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?