Question 56
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
Question 57
A customer has a requirement to automatically protect all Lambda functions with runtime protection. What is the process to automatically protect all the Lambda functions?
Question 58
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
Question 59
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User:
$ADMIN_USER
Which command generates the YAML file for Defender install?
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User:
$ADMIN_USER
Which command generates the YAML file for Defender install?
Question 60
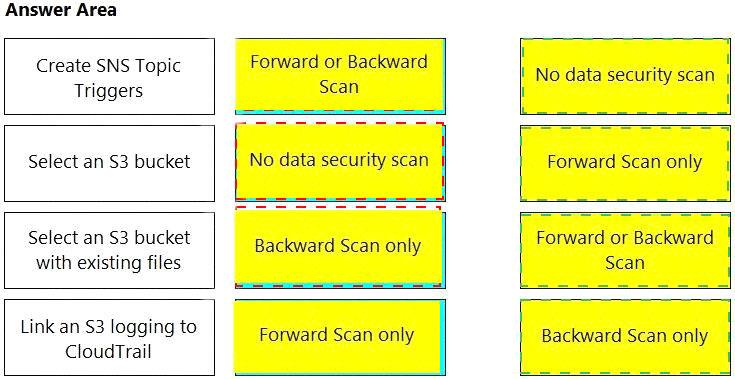
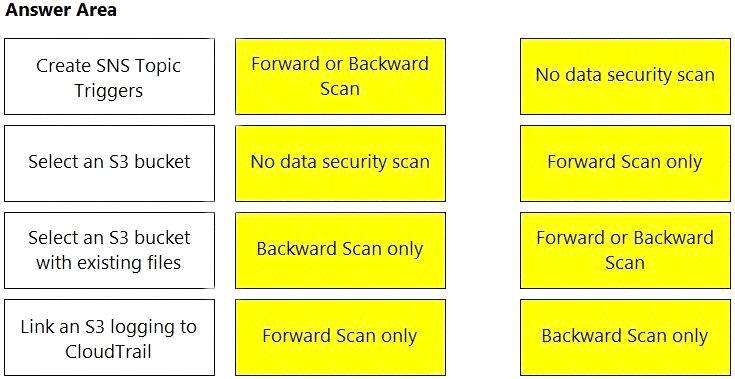
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
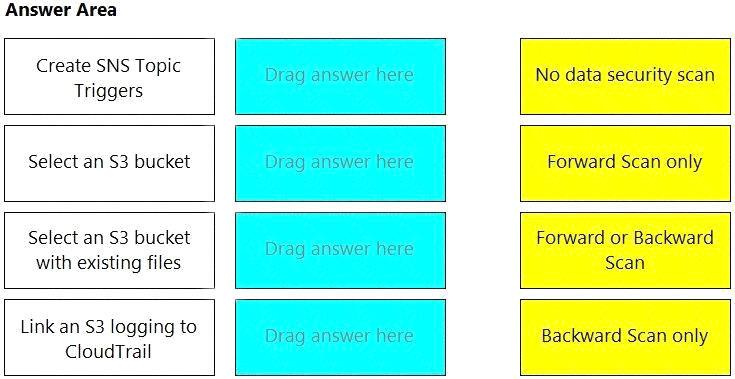
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)