Question 11
What kind of the threat typically encrypts user files?
Question 12
Network attacks follow predictable patterns. If you interfere with any portion of this pattern, the attack will be neutralized. Which of the following statements is correct?
Question 13
With a Cortex XDR Prevent license, which objects are considered to be sensors?
Question 14
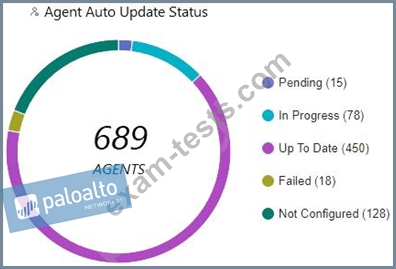
Which statement is true based on the following Agent Auto Upgrade widget?

Question 15
Which module provides the best visibility to view vulnerabilities?

