Question 96
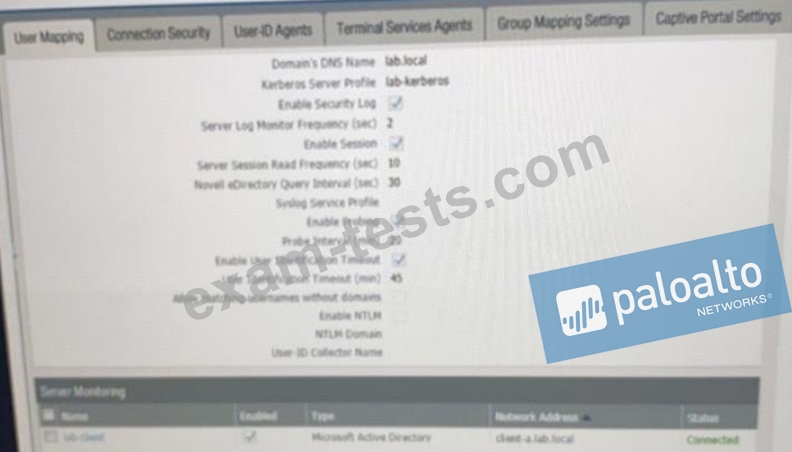
Based on the graphic which statement accurately describes the output shown in the server monitoring panel?



Question 97
Which statement is true regarding a Best Practice Assessment?
Question 98
Which two configuration settings shown are not the default? (Choose two.)


Question 99
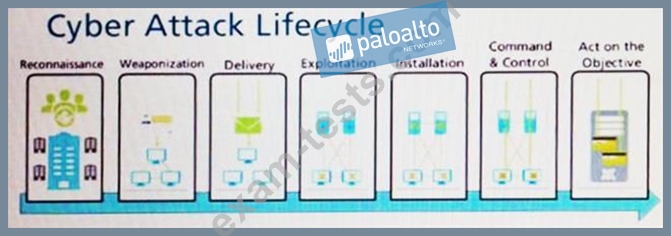
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.

Question 100
Which Palo Alto networks security operating platform service protects cloud-based application such as Dropbox and salesforce by monitoring permissions and shared and scanning files for Sensitive information?

