Question 56
Which two configuration settings shown are not the default? (Choose two.)
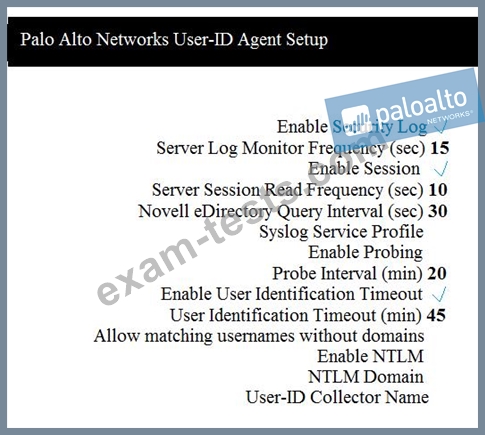

Question 57
Your company is highly concerned with their Intellectual property being accessed by unauthorized resources. There is a mature process to store and include metadata tags for all confidential documents.
Which Security profile can further ensure that these documents do not exit the corporate network?
Which Security profile can further ensure that these documents do not exit the corporate network?
Question 58
During the packet flow process, which two processes are performed in application identification? (Choose two.)
Question 59
Which statement best describes the use of Policy Optimizer?
Question 60
The firewall sends employees an application block page when they try to access Youtube.
Which Security policy rule is blocking the youtube application?
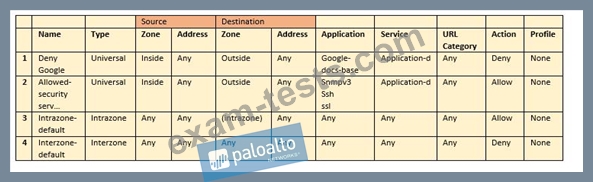
Which Security policy rule is blocking the youtube application?

Premium Bundle
Newest PCNSA Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PCNSA Exam! BraindumpsPass.com now offer the updated PCNSA exam dumps, the BraindumpsPass.com PCNSA exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PCNSA pdf dumps with Exam Engine here:

