Question 21
Which type of security rule will match traffic between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone?
Question 22
How are Application Fillers or Application Groups used in firewall policy?
Question 23
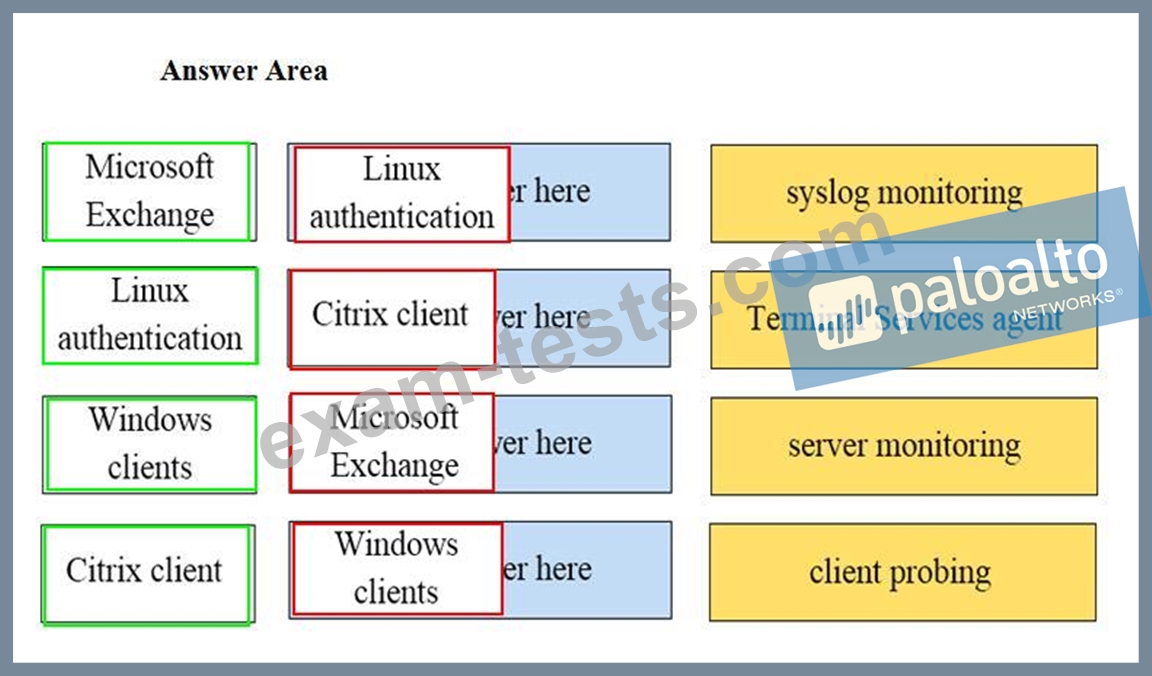
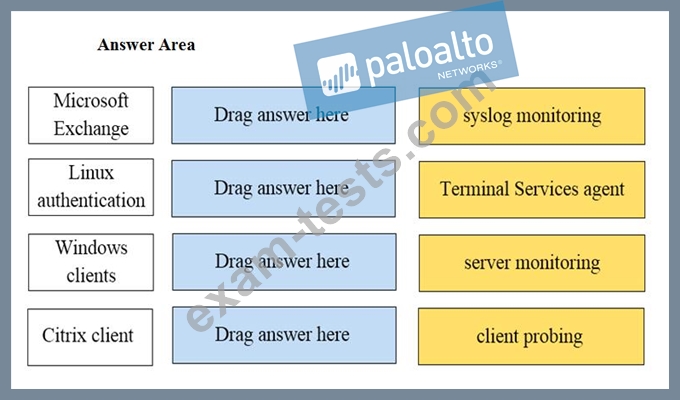
Match the network device with the correct User-ID technology.

Question 24
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
Question 25
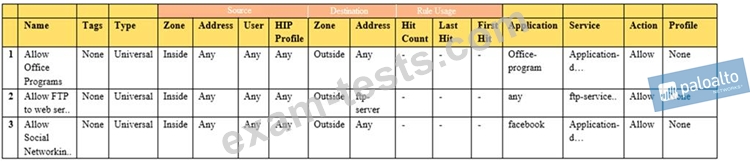
Given the image, which two options are true about the Security policy rules. (Choose two.)

Premium Bundle
Newest PCNSA Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PCNSA Exam! BraindumpsPass.com now offer the updated PCNSA exam dumps, the BraindumpsPass.com PCNSA exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PCNSA pdf dumps with Exam Engine here: