Question 66
Which two are valid ACC GlobalProtect Activity tab widgets? (Choose two.)
Question 67
To support a new compliance requirement, your company requires positive username attribution of every IP address used by wireless devices You must collect IP address-to-username mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves The wireless devices are from various manufacturers Given the scenario, choose the option for sending IP address-to-username mappings to the firewall
Question 68
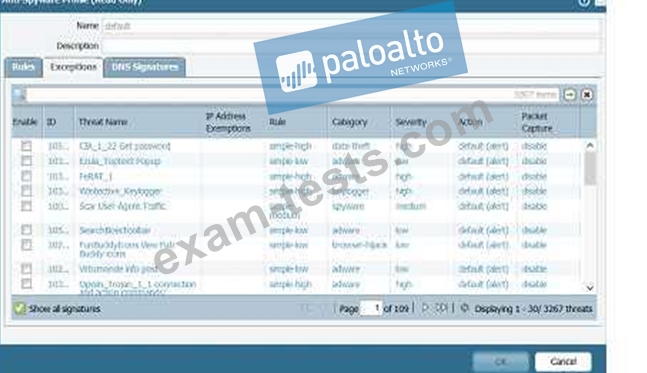
A network Administrator needs to view the default action for a specific spyware signature. The administrator follows the tabs and menus through Objects> Security Profiles> Anti-Spyware and select default profile.
What should be done next?
What should be done next?
Question 69
Which client software can be used to connect remote Linux client into a Palo Alto Networks Infrastructure without sacrificing the ability to scan traffic and protect against threats?
Question 70
An administrator has a PA-820 firewall with an active Threat Prevention subscription The administrator is considering adding a WildFire subscription.
How does adding the WildFire subscription improve the security posture of the organization1?
How does adding the WildFire subscription improve the security posture of the organization1?